As organizations increasingly rely on digital collaboration tools like Microsoft Teams, the inadvertent leakage of Teams meetings within companies has emerged as a significant concern, casting a shadow on organizational security and confidentiality.
Such incidents can potentially lead to a cascade of issues, including the exposure of sensitive discussions, proprietary information, and strategic plans to unauthorized individuals. This breach of privacy not only jeopardizes a company’s competitive advantage but also undermines client trust and regulatory compliance efforts.
As confidential meetings find their way into the wrong hands, the repercussions can range from compromised intellectual property to damaged reputations, emphasizing the urgent need for robust data loss prevention measures and comprehensive employee education to mitigate this growing threat.
To effectively address the risk of Teams meeting data exfiltration, consider the following steps in the implementation of a tactical DLP rule:
- Understand Your Data: Identify and categorize sensitive information discussed in Teams meetings, such as financial data, intellectual property, or customer information.2.
- Customized DLP Policies: Create customized DLP policies within Microsoft DLP to recognize specific patterns, keywords, or regular expressions associated with sensitive discussions. Tailor these policies to flag potential data leakage within Teams meetings.
- Comprehensive Endpoint Protection: Extend DLP policies to endpoints and devices accessing Teams meetings. Monitor and block data transfers involving sensitive information even when meetings are accessed outside the corporate network.
- Educate and Train Employees: Provide comprehensive training to employees on the risks of data leakage during Teams meetings. Encourage best practices, such as refraining from sharing sensitive data and utilizing secure channels.
- Monitor and Audit Regularly: Set up alerts to be notified of potential DLP policy violations within Teams meetings. Regularly review logs and reports to identify unusual patterns or potential incidents.
Tactical DLP Rule
– Policy Name: Teams Meeting Data Exfiltration Prevention
– Rule Description: Detects and prevents the unauthorized sharing of sensitive data during Microsoft Teams meetings.
– Rule Criteria:
– Monitor: Teams Meetings
– Condition: Content includes predefined keywords or patterns associated with sensitive data
– Action: Notify and block the sharing of the sensitive content
– Endpoint Protection: Apply the rule to both network and endpoint devices
– Compliance: Ensure adherence to industry regulations and company policies
By implementing this tactical DLP rule, your organization can significantly mitigate the risks of leaked Teams meetings and fortify data loss prevention efforts across your collaboration platforms.
Feel free to adjust the content and DLP rule based on your organization’s specific needs and policies.
Implementation
1 Navigate to compliance.microsoft.com and select Data Loss Prevention – Policies
2 Select: Create Policy
3 Select Custom Policy and select Next.
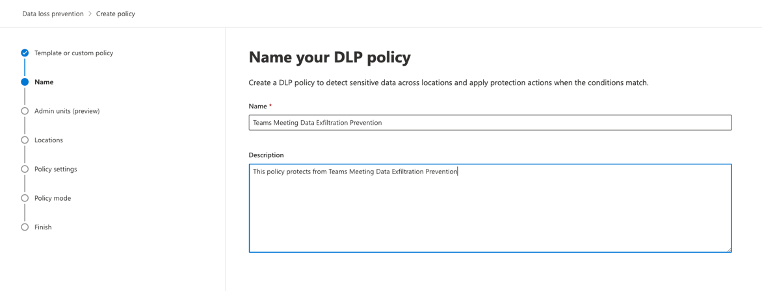
4 Name the policy and provide an accurate description of the policy.
5 Select Next and Next again, as we want to assign this policy to all groups and users.
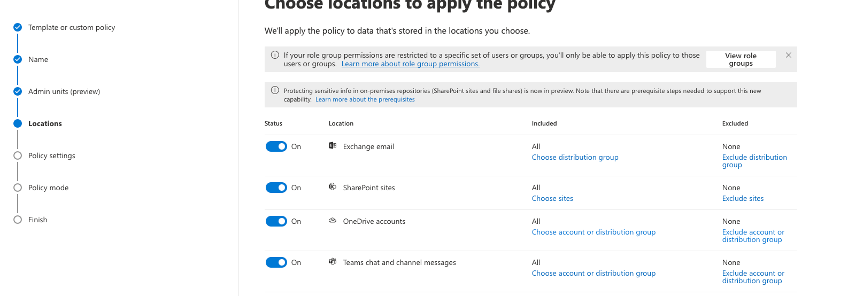
6 Select your locations to apply the policy – in this case we are leveraging multiple technologies in the stack, from Exchange to Teams.
7 Under Define Policy Settings – Create or customize advanced DLP rules will be selected. You can select Next.
8 Select Create Rule. This opens the Create Rule Panel:
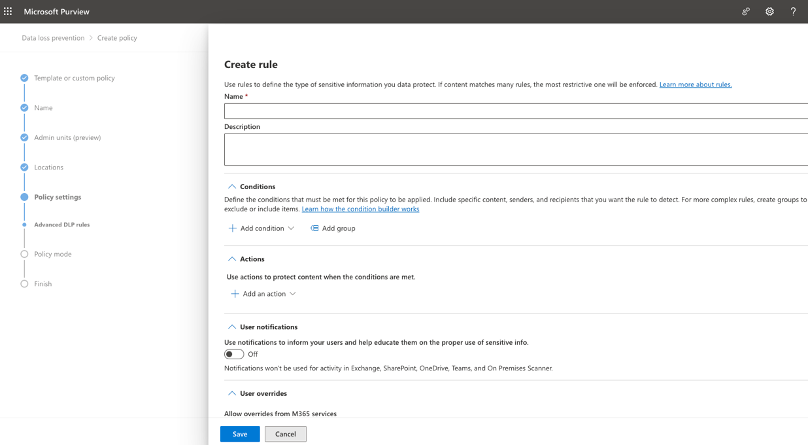
9 Input a Name and description for the Rule.
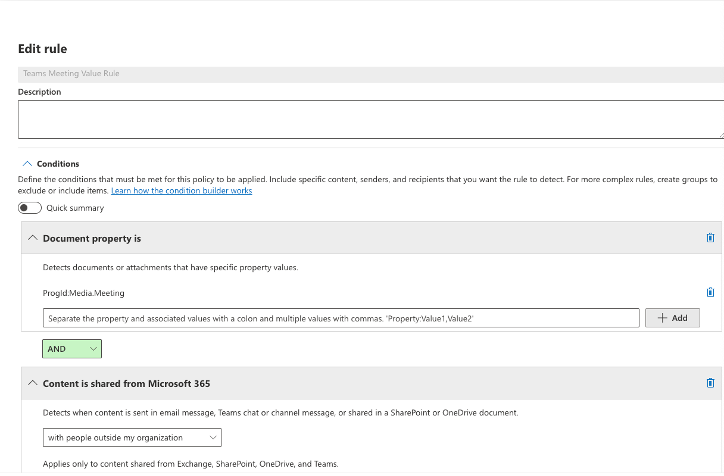
10 Your conditions are:
- Document Property is : ProgId:Media.Meeting
- Content is shared from Microsoft 365: With people outside my organization
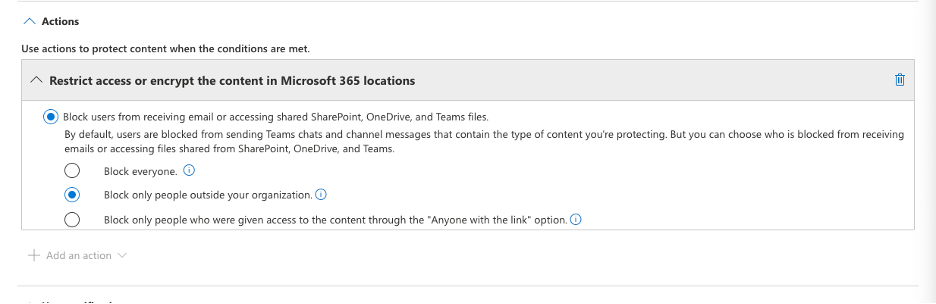
11 From here we can select an action. In this case we want to Block only people outside your organization.
12 From here you can finish the rules user notifications and set alarms for the incident for review by a security team, should this event occur.
- Save your rule.
- Select Next.
- Select Test it out First.
- Verify testing and behavior.
The Author
William Tooley is the Technical Director for Azure and o365 at Novacoast. He’s a seasoned security engineer with two decades’ worth of expertise, specializing in Microsoft Technologies and Information Security.




