The Google Chrome Web Store has a history of malicious actors abusing it to deliver malware-laden browser extensions. While Chrome extensions do have a granular permissions specification with specifics about what each extension can read and change stated in the installer (with a “show details” click), the extent and gravity of those permissions is often understated or not well understood by users.
Last year, SOC-as-a-Service provider Pillr discovered a particular long running browser extension malware campaign presenting in its monitored endpoints. This was a security incident, stopped before it became a breach, which is in line with a notable finding from a 2018 Verizon investigative report: in “60% of cases, the breach was discovered by an external party.”[1]
In this article, threat researcher Kelsey O’Connell covers the tactics and technique utilized for the GalComm malware.
CommuniGal…malware by any name
Many of these extensions had one commonality, their registrar, CommuniGal Communication Ltd. (Also goes by – GalComm, CommuniGal, and Gal Communication Ltd), a company located in Netanya, Israel.
These malicious browser extensions are considered Man-in-the-Browser attacks and can be mapped to the MITRE ATT&CK technique T1176: Browser Extensions.[2]
To determine whether a browser extension is malicious, analysis must be done on the various permissions they require. Many browser extensions request over-reaching permissions, such as the ability to view all activity on every website visited, access to cookies (can be used in credential stealing), ability to make changes to privacy settings, capture audio directly from the microphone, and a multitude of others.
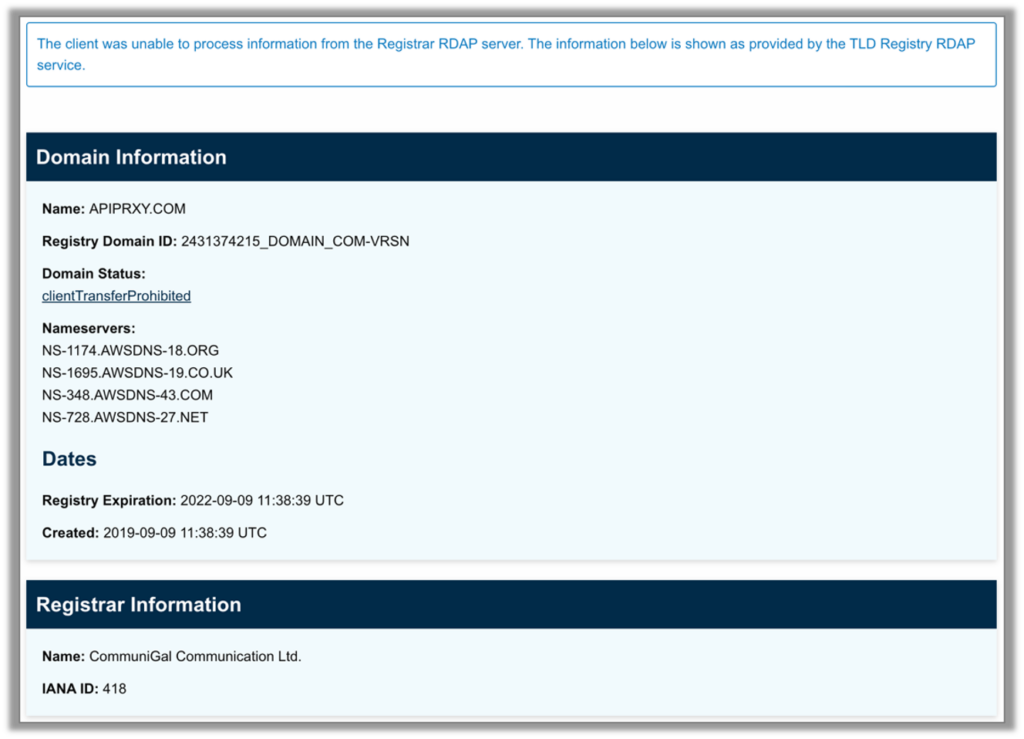
In the permissions section of the extensions, specific domains are listed. Performing a search using ICANN Lookup reveals that these extensions are registered under CommuniGal Communication Ltd.
All the extensions requested excessive permissions. Some of the most intrusive of the permissions are:
all_urls |
Read and change all your data on the websites you visit, including file:///* (local storage) Access to run on all sites and schemes, including file:///* (local storage) |
bookmarks |
Read and change your bookmarks |
cookies |
Query and modify cookies, and to be notified when they change (Can be used for credential stealing) |
management |
Access and manage your installed apps, extensions, and themes |
storage |
Store, retrieve, and track changes to user data |
tabs |
Read your browsing history Interact with browser’s tab system, create, modify, and rearrange tabs and windows in the browser |
topSites |
Read a list of your most frequently visited websites |
webRequest webRequestBlocking |
Observe and analyze traffic and to intercept, block, or modify request in-flight |
Although these domains are linked to extensions that have been labeled malicious and removed from the Chrome Web Store, they are still registered with CommuniGal Communications Ltd. and are not set to expire until the year 2022.
novaSOC is seeing this as a far-reaching, widespread campaign. Although many of these extensions discovered by novaSOC are newly discovered identifiers, some of the malicious extensions were previously written about in Tom’s Guide[3] and an Awake Security report.[4]
Reach of Incident by the Numbers
- 61 Unique Extension Identifiers
- 27 Unique Domains
- 12 Unique Extension Names (case sensitive)
- 30 Previously Unidentified Extension Identifiers
- 20 Previously Unidentified Domains
Diving into Source Code
Extension Name: Search Manager
Extension Identifier: bahkljhhdeciiaodlkppoonappfnheoi
Users: 1,000,000
Reviews: 3,578
Web Store Rating: 4.0/5
With the help of data that was captured in our own backend, we were able to take a closer look at the source code for the Chrome extension “Search Manager.” The source code gives us a better understanding of what the extension is: 1) what it is doing, and 2) who is it communicating with? Figure 2 below is a snippet of the extension’s manifest.json file. It shows that this extension is a browser hijacker that changes the browser’s default search engine to “http://srchbar[.]com”.
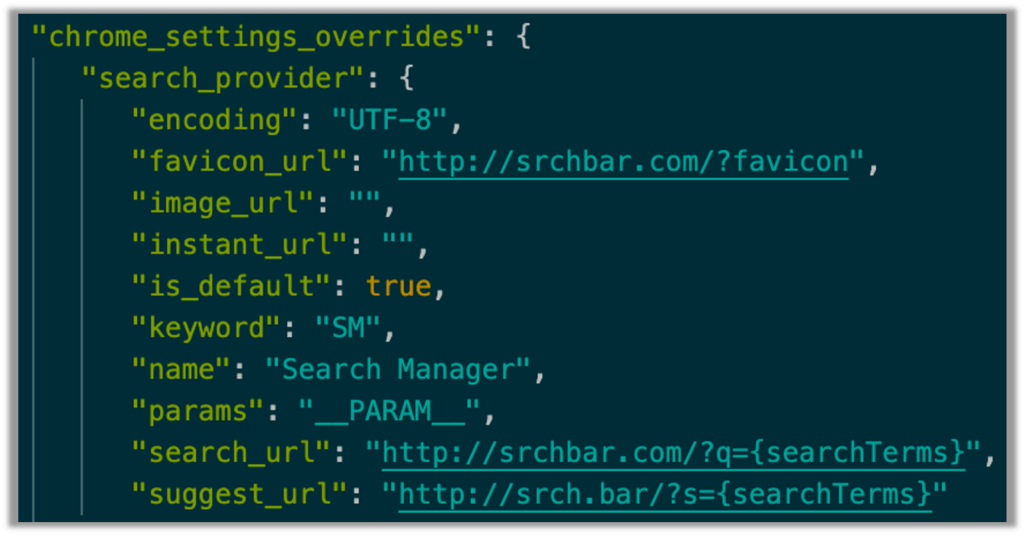
Shown in Figure 2, Line 16 of the manifest.json file includes the URL for the favorites icon (favicon). But is it really a favorites icon? Using a browser isolator, navigating to http://srchbar[.]com/?favicon does not lead to a nice little .png file; instead, it instantly redirects to the Yahoo! Search page (Figure 3).
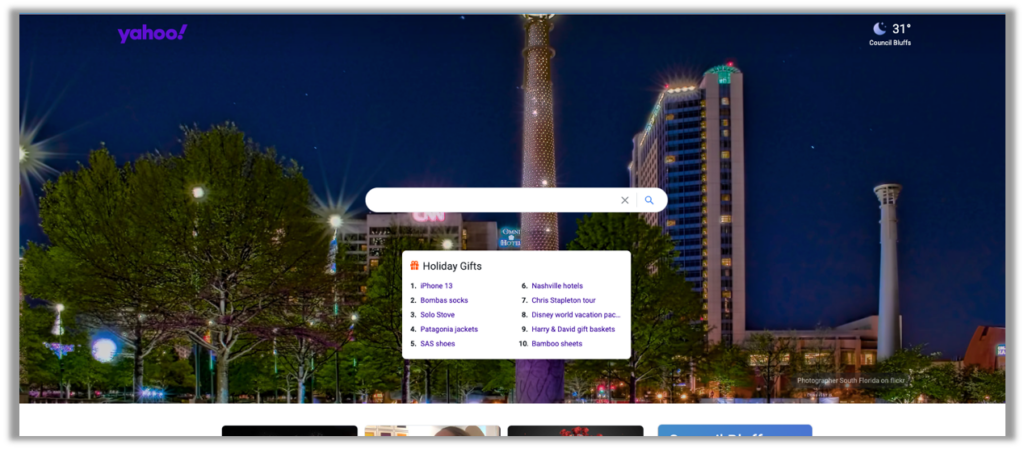

Buried in the query string of the URL is the attribution for what redirected/referred the user to Yahoo! (Figure 5), Search Manager.

Diving even deeper into the source code leaves no doubt as to the nefarious nature of these extensions. Figure 6 shows the AmpSearchServiceLocalList.json file.
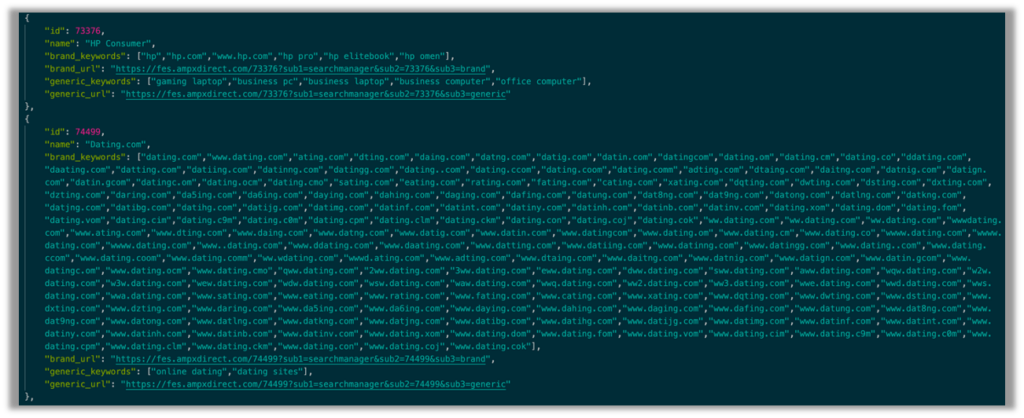
The first and most revealing string reads “advertisers.” The rest of the code shows ID numbers, company names, possible permutations and typos of the brand names, redirection URLs, and applicable search terms.
The redirection domain leads to ampxdirect[.]com, a domain that is registered to “adMarketplace.” The company name is an indicator of adware, which employs the use of referral codes and URL redirects (browser hijacking). The referral code is used to track and give financial incentives to the referrer (i.e. the adware creator) for every click, then redirects the user to the specified website.
Conclusion
GalComm is a registrar that appears complicit in the dubious activities of these extensions, which are used to create ad revenue for the makers of these extensions, unbeknownst to the users. Browser extensions often face less scrutiny than downloaded software, so they easily fly under the radar of the user who is just looking for a convenient feature-driven solution and are disarmed by the implied legitimacy of the Chrome Web Store. Users should acquaint themselves with the permissions that an extension is requesting and educate themselves on what an extension does under the hood.
Threat Indicators
Below are Indicators of Compromise (IOCs) discovered in GalComm malware. IOCs are used to detect malware infections and can be actively searched for during threat hunting or set as alarms.
| Chrome Extension Name | Chrome Extension Identifier |
|---|---|
| DoctoPDF | ijcgfgdkipppfbkiikoddcjflephnpmf |
| DoctoPDF | jfgkpeobcmjlocjpfgocelimhppdmigj |
| DoctoPDF | keceijnpfmmlnebgnkhojinbkopolaom |
| DOCtoPDF | jgjakaebbliafihodjhpkpankimhckdf |
| DOCtoPDF | mdodmpdhcdbdlbeahilnfoeidccceegj |
| DOCtoPDF | npaklgbiblcbpokaiddpmmbknncnbljb |
| DOCtoPDF | pgahbiaijngfmbbijfgmchcnkipajgha |
| EasyConvert | annjkojdjjedabhfdnfacdiafkmpijbl |
| EasyConvert | baimmgglolfkaaefedmlgfkdajckmpfm |
| EasyConvert | bngebgoljdhmkgmecefkcfhjngffihii |
| EasyConvert | gfihbklhmmihlkkjnemjppijdlmkcgbb |
| EasyConvert | gofhadkfcffpjdbonbladicjdbkpickk |
| EasyConvert | hmamdkecijcegebmhndhcihjjkndbjgk |
| EasyConvert | jkppdkadcnfnafkfjdhgbmhklhilimli |
| EasyConvert | labpefoeghdmpbfijhnnejdmnjccgplc |
| EasyConvert | lpajppfbbiafpmbeompbinpigbemekcg |
| EasyConvert | ojmoedcpcgeminijlnogdmkelkcfalfl |
| PDF Extra | ipagcbjbgailmjeaojmpiddflpbgjngl |
| PDF Ninja Converter | khhemdcdllgomlbleegjdpbeflgbomcj |
| PDF Opener | elflophcopcglipligoibfejllmndhmp |
| PDF Opener | ggijmaajgdkdijomfipnpdfijcnodpip |
| PDF Opener | jkdngiblfdmfjhiahibnnhcjncehcgab |
| PDFcreate | hjncnnhioabgjeokhinifgjcallhenll |
| Search Manager | bahkljhhdeciiaodlkppoonappfnheoi |
| Search Manager | bhoagceacaklimpcejjofabngcjkebfg |
| Search Manager | cpgoblgcfemdmaolmfhpoifikehgbjbf |
| Search Manager | gihcgddmlhacnmdenbdkokeaffnekgob |
| Search Manager | icmgebopaejnjlncllgmcenbbflikfjd |
| Search Manager | kbdbmddhlgckaggdapibpihadohhelao |
| Search Manager | kjcfanhkgmaaneaenocapblddnobeeci |
| Search Manager | kjgaljeofmfgjfipajjeeflbknekghma |
| Search Manager | ljnppgaebjnbbahgmjajfbcoabdpopfb |
| Search Manager | majekhlfhmeeplofdolkddbecmgjgplm |
| Search Manager | mhinpnedhapjlbgnhcifjdkklbeefbpa |
| Search Manager | mopkkgobjofbkkgemcidkndbglkcfhjj |
| Search Manager | nahhmpbckpgdidfnmfkfgiflpjijilce |
| Search Manager | nccfgpamboionigdpfjmijhlgmgdbael |
| Search Manager | ocilpnnapnkmcdabaeoobbamlniheaep |
| Search Manager | olojcnagmcbplpdddabmpfehhlleobpb |
| Search Manager | ommbgnllpkjnidkcnginhlacffdcdijc |
| Search Manager | pilplloabdedfmialnfchjomjmpjcoej |
| Search Manager | pknkncdfjlncijifekldbjmeaiakdbof |
| Search Manager | ijahobfejgeblmkpcmgpelfibgnnjpil |
| Search Manager | gemcaenpcldkhfkohjjkfgfopgghpkng |
| TheDocPDFConverter | fmbgbhkodhifcbilahghgbloblanpeig |
| TheDocPDFConverter | gdifegeihkihjbkkgdijkcpkjekoicbl |
| TheDocPDFConverter | kifdhfgalmlmpcbbbimokkipeobjmpcl |
| TheDocPDFConverter | onkopdeihmdimjphfbmlefelnegjkefb |
| ViewPDF | apjnadhmhgdobcdanndaphcpmnjbnfng |
| ViewPDF | ciiobgcookficfhfccnjfcdmhekiadje |
| ViewPDF | dipecofobdcjnpffbkmfkdbfmjfjfgmn |
| ViewPDF | feahcinjmgpdpiidkcemfgkakemfamjg |
| ViewPDF | ghgjhnkjohlnmngbniijbkidigifekaa |
| ViewPDF | hbhldhipemjbfcdlanhifabdgapnhgbd |
| ViewPDF | jkofpdjclecgjcfomkaajhhmmhnninia |
| ViewPDF | lhjdepbplpkgmghgiphdjpnagpmhijbg |
| ViewPDF | mpledlgefahhhgodkdamhlplcjdgalme |
| ViewPDF | ncepfbpjhkahgdemgmjmcgbgnfdinnhk |
| ViewPDF | pnciakodcdnehobpfcjcnnlcpmjlpkac |
| Your Docs To PDF | nofdiclilfkicekdajkiaieafeciemlh |
| YourEasyConvert | fpagmddnoehfplillifalekcnfehinhb |
| Suspected Malicious Domains |
|---|
| apiprxy.com |
| docpdfconv.com |
| doctopdf.io |
| doctopdfpro.com |
| doctopdftech.com |
| easyconvertt.com |
| ezconvertor.com |
| fastdoctopdf.com |
| getdoctopdf.com |
| getsrchmgr.com |
| mysrchmanager.com |
| pdfconvert.ninja |
| pdfsrch.com |
| searchmanagertech.com |
| searchmgr.com |
| srchbar.com |
| srchmgrk.com |
| srchmgrl.com |
| srchmgrq.com |
| thedocpdfconverter.com |
| thedoctopdf.com |
| thepdfcreate.com |
| thepdfopener.com |
| viewpdf.com |
| viewpdf.io |
| yourdocstopdf.com |
| youreasyconvert.com |
References
- Verizon 2018 Data Breach Investigations Report
https://www.verizon.com/business/resources/reports/dbir.pdfx - https://attack.mitre.org/techniques/T1176/
- “Nearly 80 Chrome extensions caught spying – how to protect yourself”. -Nicholas Fearn. https://www.tomsguide.com/news/chrome-extension-spyware
- “The Internet’s New Arms Dealers: Malicious Domain Registrars”. Awake Security. https://cdn2.hubspot.net/hubfs/3455675/wp-the-internets-new-arms-dealers-malicious-domain-registrars.pdf
The author
Kelsey O’Connell is a researcher with novaSOC‘s Threat Operations Team, investigating suspected malicious software/services and profiling advanced persistent threats.





