In the creepy, fluid landscape of cybersecurity, threats continually evolve and adapt, just like creatures from a compromised bio-lab. Hackers excel at developing new clever methods to gain unauthorized access to networks and systems, usually in the interest of money and sometimes individually wrapped snack-size candy.
The impact on businesses successfully hacked can be costly; recovery of valuable data and system restoration have huge price tags attached, not to mention the loss of reputation after an attack is known to customers and the public at large.
It’s a spooky thing, and many of us lay awake at night throughout the year—not just Halloween—staring at the ceiling and struggling to contain our fear of the next cyber attack. Is that scraping on the door a malware-for-hire mercenary trying to phish your HR manager? The hair on your neck stands at attention as a howl in the distance signals a new RCE zero-day being announced…
Snap out of it! There are some simple ways to quell threats, protect your business, and minimize damage if a cyberattack does happen. Let’s take a look.
1. Software Updates and Patches
Keeping servers and workstations updated to latest versions and installing security patches that fix vulnerabilities is a simple way to keep attackers from capitalizing on the low-hanging fruit of well-known bugs. In most cases, updates to operating systems and software applications enjoy performance gains as well.
Cybercriminals leverage vulnerabilities as a foothold into accessing systems. Keeping everything updated and patched goes a long way towards preventing unauthorized access that can lead to a data breach, or worse, by hackers.
2. Long Complex Passwords and Multifactor Authentication
Passwords are an core element of security that needs full attention. Longer complex passwords are more difficult for hackers to brute force to gain unauthorized access.
A recent study shows how quickly hackers can brute force passwords by length and complexity, making a valid argument on the side of long, complex passwords.
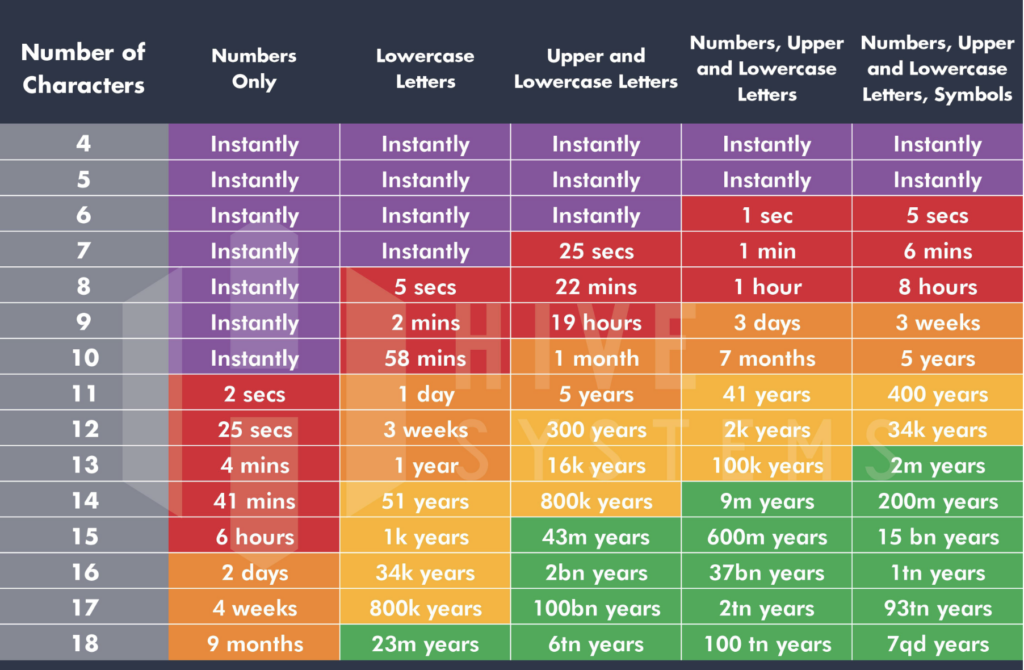
Password strength is far more significant than the length in most cases. A twelve-character password alone makes no huge difference until you add the complexity of mixed case, numerals, and special characters.
Google recently announced that it’s developing a password strength indicator for integration into future versions of the Chrome browser. In doing so, they acknowledge (in addition to many security companies) that password strength is still a linchpin of security.
When implementing a strong password initiative, a typical concern from users is remembering all the different passwords for each application or system they need to access. Use of a password manager such as 1Password, LastPass, or Bitwarden company-wide solves the issue.
Even if not implemented institutionally, make their use part of your security best practices for employees.
3. Endpoint Security
Endpoint monitoring and protection is compulsory security tactic for modern organizations. It’s a way to analyze traffic and endpoint security data to detect suspicious or malicious activity that could lead to attack.
What Is Endpoint Security?
An endpoint security platform protects a business’s infrastructure when external devices such as personal laptops, tablets, smartphones, and other network-connected devices access it.
Use of endpoint protection on all network servers and user devices helps prevent unauthorized access by blocking hackers when malicious activity is detected. It also ensures that business data on lost or stolen devices is protected.
Every external device that connects to your network is a potential threat. Implementing endpoint security and limiting the devices that can access sensitive information helps mitigate the risk from unauthorized access.
4. Security Assessments
Security assessments are critical to evaluating how your defensive posture actually holds up to an attack of unknown scale and nature. By conducting testing that involves experts actually trying to break through your defenses, valuable information is gained on how to better them.
What Are Security Assessments?
Security assessments go beyond monitoring and include a series of tests that help an organization’s IT department understand any gaps and holes so they can fix them before a cybercriminal leverages them.
While there are many types of security assessments, a few types that standout include:
Vulnerability Assessment
A vulnerability assessment finds vulnerabilities! This can include enumerating unpatched servers, uncovering misconfigurations, poorly designed network infrastructure, or systemic issues that can represent opportunities for exploitation in some way.
Penetration Testing
A penetration test seeks to find a way through defenses via a variety of documented tactics and techniques. It will mimic actual attack types such as phishing, spear phishing, social engineering, or whaling. It will also attempt exploits for known vulnerabilities, and can chain multiple exploits together.
The result provides a good picture of where a business is vulnerable to attackers to that problems can be corrected.
Red, Blue, & Purple Team Testing
In these assessments, the teams play the roles of attackers (red) and defenders (blue). The red team includes penetration testers but can also have team members performing physical access attacks.
The blue team defenders include internal security teams. An effective blue team will possess an eternally curious nature and a proactive mindset and continually work toward improving detection and response.
Purple teams are typically made up of both red and blue representatives. The two teams work in unison, sharing data and security insights that help to improve the business’s security overall.
Threat Hunting Assessments
Many organizations use proactive threat hunting assessments to search for undetected cyber threats and malware lurking in a network. Assessments are a deep dive to locate malicious threat actors sitting in wait that may have escaped detection by endpoint security.
These types of threats can remain hidden for months, and during this time they may obtain login credentials, search for sensitive information, and steal data that lets them later move across a network.
Threat hunting is essential to keep an adversary from successfully evading detection and perpetrating an attack. Additionally, many businesses do not have the necessary tools or advanced capabilities to remove advanced persistent threats (APTs) from residing in their network.
Threat hunting assessments are a continual process that works toward rooting out APTs and maintaining a clean environment.
5. Employee Training
Among successful cyber attacks, 95% found human error as a leading factor. Implementing cybersecurity training for employees is a good business investment. The benefits of cybersecurity training are many, but these are a few:
Protecting Your Business
Reducing threats that can end up in a data breach or other cyberattack is critical to protecting your business. Regular training teaches employees how to recognize threats and implement safe business practices so that they don’t ignorantly fall for common tricks that attackers rely on.
Saving Time And Recovery Costs
Cyberattack and data breach recovery easily costs businesses billions annually. Training staff members can potentially save you millions.
If your business experiences downtime after an attack, you’re looking at additional costs on top of the cost of restoring your network and systems back to operation.
Client Trust
A publicized cyberattack can ruin a business’s reputation in the eyes of current and potential clients. In a recent survey, 65% of consumers said they would lose trust in a company after a cyberattack or data breach.
Customers, both the savvy kind and those who only casually understand security, who see that a business has demonstrated due diligence by investing in security training for its staff would be more confident in doing business with them.
Compliance
If your business deals with private, confidential, or sensitive data, it is responsible for complying with any applicable regulations regarding its handling and storage. There will be fines if the methods and procedures defined for the regulated data are not complied with.
Ensuring all staff are trained in cybersecurity best practices and compliance standards is necessary to prevent legal action and/or fines. The training will teach them how to handle the data, which adds another layer of security to your business.
Employee Confidence
The safety of many businesses relies on employee confidence. Employee confidence gets a boost after training, and they will know with certainty which links, emails, and messages are risky.
Your business can reduce the risk of human error causing a cybersecurity incident or breach through proper training.
Don’t Get Spooked
Today, the threats, motives, and capabilities of cyber attackers truly make for the stuff of horror films. Damaging attacks can ruin businesses, wipe out bank accounts, cause endless headaches for users’ identity and credit, and permanently destroy invaluable data. In some cases it’s almost preferable to be haunted by The Babadook or have your children stolen by witches of Hocus Pocus. But with a little strategy and investment, risk can be mitigated.
This Halloween, be sure to take stock of your cybersecurity hygiene and best practices to keep your business and its data protected year-round.



