Spoofing, phishing, and business email compromise (BEC) emails have been pounding inboxes relentlessly with malicious intent. In 2021 email malware attacks grew by 600% compared to data from 2019.
One of the most powerful tools we have in stopping inauthentic email before it arrives is called DMARC, and it should be a compulsory step in the configuration of any business email system.
What is DMARC?
A better question is: how to prevent scammers from using your domain when spoofing the “From” address in emails. We’ve all seen these scams from PayPal, Banks, Credit Cards, Employers, and others— all attempting to coerce you into clicking the link and revealing your personal information. It seems like anyone can format their email to appear that it comes from anyone else, leaving only the discerning eye of reader to catch the ploy. If only there was a way to validate an email as authentically generated before it hits the inbox.
There is! One way to go beyond the usual methods of SPF and DKIM is to implement a strict DMARC policy.
Implementing the DMARC standard ensures these types of scams are blocked. It means they never arrive at all in any of your users’ inboxes. In addition, using DMARC provides visibility and reports on who may be sending emails on behalf of your domain. This way, your domain and your business reputation are kept intact.
What Happens When You Don’t Implement DMARC?
Many theorize that not having a DMARC shouldn’t affect message deliverability; the reality is it depends. Do you want to risk your email not getting through?
Perhaps your company hasn’t published a DMARC policy. You’d like to think it’s the responsibility of the domain owner to define how a recipient should treat email messages that fail DMARC validation. But not having a DMARC policy defined often means your outgoing messages won’t even reach the intended recipient.
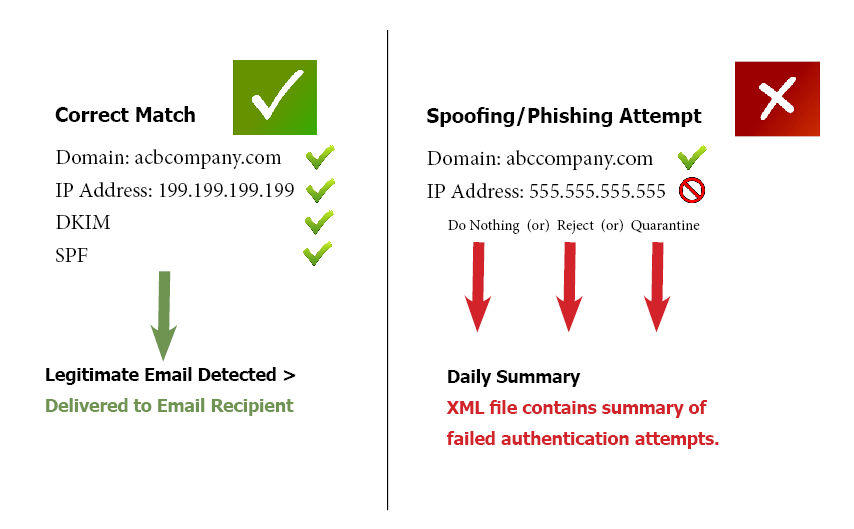
Email authentication has evolved over time to use methods like SPF (DNS-based) and DKIM (key-based between hosts) to accomplish this authentication, but as time passed, attackers have learned to circumvent and bypass these measures.
The SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) verify that the stated sender actually sent the email message, and where it concerns SPF, which IP is allowed to send the message. However, these don’t let the recipient ISP know what it should do with email messages that fail authentication or are unauthenticated.
DMARC specifies to domains receiving unauthenticated email messages what they should do with them. The common options are accepted, quarantined, or reject email responses, as well as who should get a notification of failure.
While some larger ISPs leverage DMARC to protect outbound email messages, most do not. Yahoo and AOL are among the few that publish rejected records, and many more honor DMARC when receiving email messages.
Cost of Attacks
Cybersecurity attacks cost organizations big time. With approximately 5 billion email accounts globally, attackers know they get the broadest reach by leveraging the email vector which remains the backbone of business communication to this day. According to Deloitte, 91% of all hacking attacks and data breaches involve email.
The average financial cost of a spear phishing attack comes in around $1.6 million, and BEC (business email compromise) scams cost US businesses roughly $500 billion annually.
Benefits of Using DMARC
One of the widespread benefits of using DMARC is that it requires “alignment.” The process of alignment checks for consistency between the email domain used in the email headers and those in the authentication. If they don’t match, the email fails authentication.
These days, DMARC is considered critical to a company’s email security and deliverability strategy. The essential benefits it enables are:
Visibility
Visibility is valuable for both sender and recipient. There should be no email activity that is hidden in the magic box or inaccessible to monitoring and review.
While DMARC is implemented and utilized in much the same way as SPF, it goes beyond authentication by allowing configuration of a reporting mechanism for failed authentications.
Brand Protection
Most people who are the target of spoofed messages from your company aren’t going to appreciate or comprehend the novel idea that bad actors can actually send email that appears as if it was sent by you. Damage to brand reputation is easy to inflict this way. The risk to reputation just isn’t worth not implementing ever measure available.
Using DMARC, invalid emails get blocked before victims can receive them.
Security
With phishing being the most common initial attack vector for even the most sophisticated attacks, email security is a high priority and the first line of defense.
When a DMARC policy is set to reject invalid emails, it removes the pressure on end users who may only have basic phishing awareness training. Additionally, DMARC can prevent:
- Malicious phishing campaigns against customers
- Brand abuse and scams
- Ransomware and malware attacks
- Spear phishing against employees
- CEO fraud
How Do SPF and DMARC Work Together?
At first glance, when diving into the technical details of how DMARC works, you’ll notice that DMARC is very similar to SPF—It’s a DNS record-based configuration. The inbound mail server uses the SPF and DMARC DNS TXT records, which are in practical theory only editable by authorized administrators within the organization, to validate acceptable origin mail server hostname or IP address. Here are some examples of implementation on Office 365 (which is configured by default):
An example SF record:
contoso.com IN TXT " v=spf1 ip4:192.168.0.1 ip4:192.168.100.100 include:spf.protection.outlook.com -all"—Versus—
An example DMARC record:
_dmarc.microsoft.com. 3600 IN TXT "v=DMARC1; p=none; pct=100; rua=mailto:d@rua.contoso.com; ruf=mailto:d@ruf.contoso.com; fo=1"The DMARC record adds extra instructions to the receiving mail server for handling of failed authentication messages. p=none indicates to do nothing, allow receipt, whereas p=reject would signal the inbound server to not accept the message.
At least in the case of Office 365, SPF and DMARC will also be used in a coordinated manner to check different fields in email headers. SPF traditionally is used to validate the 5321.MailFrom field, but this can be defeated is the 5322.From field is configured in a malicious message. DMARC will extend this authentication to both fields.
The Never-Ending Journey To Improving Email Security
Security is a landscape that is continually moving. We implement new methods to secure our email; cyber attackers learn how to bypass them. Right now, DMARC is a critical tool we all should have implemented.
It may seem like a case of adding more of the same to stay ahead of spammers and email spoofers, but it does work…for now. Mileage may vary with different email server conventions but adoption of the new DMARC standard is inarguably compulsory at this point. Inevitably those who constantly chip away at email security methods will find a way to defeat it, and by then we’ll have developed something more.




