In the realm of access control and authorization, the conventional ESAE (Everything Starts at the End) model has long been the cornerstone of security strategies. The old ESAE model, which predominantly relied on a one-size-fits-all approach, often hindered the efficient management and security of digital assets from the user layer. In contrast, the Modern Privileged Access Model, commonly called zero-trust, represents a dynamic shift, recognizing the importance of fine-grained, context-aware authorization and empowering organizations to adapt and enhance their security measures in response to the ever-evolving digital landscape. This transformation reflects the maturation of cybersecurity practices and underscores the importance of a proactive, risk-based approach to safeguarding critical data and resources.
Let’s consider the old tier systems in the ESAE model and the issues associated with them:
1. Cost Inefficiency: The hierarchical structure of the Tier 0 model often led to excessive costs associated with maintaining and expanding the infrastructure.
2. Complexity: The intricate hierarchy of the Tier 0 model resulted in increased complexity in managing resources, leading to potential inefficiencies and errors. This does not even begin to address the problems from mergers and acquisitions and the technical debt related to those procedures that can be incurred.
3. Limited Scalability: The Tier 0 model faced challenges in scaling to accommodate the evolving needs of organizations, resulting in potential bottlenecks and constraints.
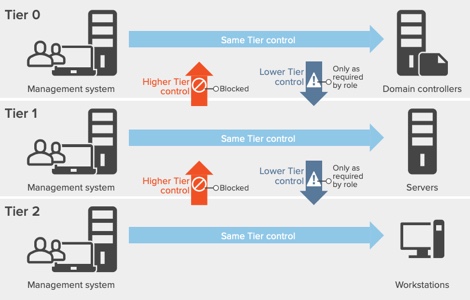
By addressing these problems, organizations understood the limitations of the old ESAE model and recognized the need for a more adaptable and efficient approach to access control.
The Modern Privileged Access Model, also known as the Zero Trust Model, represents a significant advancement in access control and authorization. This approach emphasizes the principle of least privilege, where users are only granted the minimum level of access necessary to perform their tasks. Organizations can enhance their security posture by continually verifying and validating user identities, devices, and activities by adopting a zero-trust mindset. However, despite its benefits, the Modern Privileged Access Model is not without its challenges. Implementation complexity, user experience impact, and monitoring challenges are among the key issues organizations may encounter when adopting this model. These challenges underscore the importance of careful planning, resource allocation, and ongoing management to ensure the successful implementation and operation of the Modern Privileged Access Model in today’s dynamic threat landscape.
Now let’s consider the Modern Privileged Access Model (Zero Trust) and its inherent problems:
1. Implementation Complexity: Implementing the Zero Trust Model or Modern Privileged Access Model can be complex and resource-intensive, requiring significant investments in specialized security tools, extensive training, and the cultivation of expertise.
2. User Experience Impact: Adopting a more rigorous authentication and authorization process, while essential for security, can introduce friction and delays in user access, affecting the overall user experience and potentially hindering productivity.
3. Monitoring Challenges: Security Operations Centers (SOCs) may face considerable hurdles in sifting through the vast amounts of data generated by the Zero Trust Model or Modern Privileged Access Model, identifying genuine threats amidst the noise, and responding effectively. This can lead to operational challenges and increased workload for security teams.
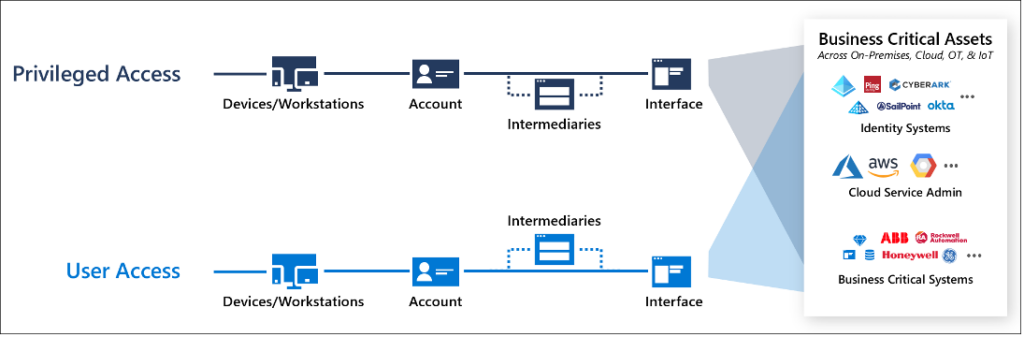
Addressing these challenges is crucial for organizations considering the adoption of the Zero Trust Model or Modern Privileged Access Model, as it allows for a more comprehensive understanding of the potential drawbacks and complexities involved in implementing these security frameworks.
Forging a New Path: The Dual Bastion Model
In response to these challenges, I propose the Dual Bastion Model—a synthesis of the strengths of both ESAE and the Modern Privileged Access Model—while addressing their respective limitations. Unlike the Modern Privileged Access Model, which places significant emphasis on user-centric defenses, the Dual Bastion Model recognizes the importance of trust in organizational dynamics while simultaneously bolstering systemic and user-centric defenses.
The Dual Bastion Model aims to build a new wall around users while keeping strong defenses for organizational systems. It does this by building on the ESAE model’s existing safety features, such as RBAC mechanisms and system-level controls. This transformative approach represents a departure from traditional paradigms and sets the stage for a more proactive and inclusive approach to access control.
Consider the following example diagram. Obviously, this is a general overview, and each component of our model would have a separate technical topology. Still, from a conceptual standpoint, this is what our overall methodology would look like:
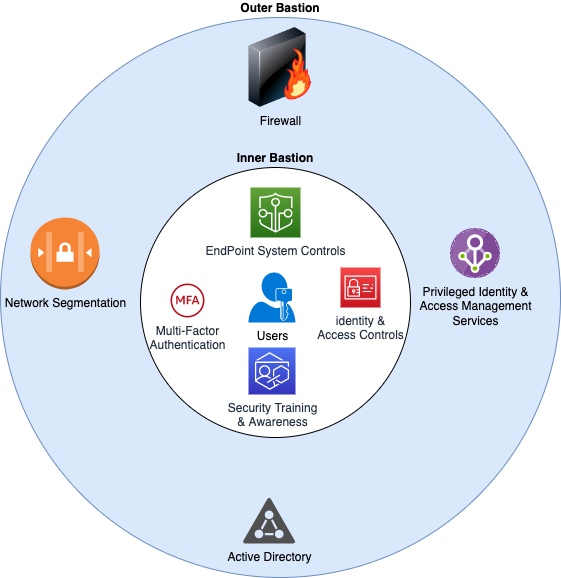
Implementing the Dual Bastion Model
This means putting advanced security measures in place that focus on users, like multi-factor authentication, endpoint system controls, and context-aware access policies, and also making the system-centric defenses stronger. By adopting a proactive approach to both system and user security, organizations can mitigate the risks posed by human factors and enhance their overall security posture.
Challenges and Opportunities
Implementing the Dual Bastion Model prompts a fundamental shift in approach, moving away from simply adding technologies to solve isolated security issues and strategically selecting technologies that enhance the organization’s overall infrastructure and user defenses while providing tangible value. This shift requires carefully considering how each technology aligns with the organization’s broader security strategy and objectives rather than focusing solely on addressing individual problems.
By adopting this holistic perspective, organizations can optimize their investments in security technologies, leveraging them to strengthen both the infrastructure base and the user base while maximizing cost savings and operational efficiencies. However, this strategic approach also presents challenges, such as the need to assess the compatibility of new technologies with existing systems, ensure seamless integration, and effectively manage the associated complexities.
Overcoming these challenges requires proactive planning, robust risk management practices, and a commitment to fostering a culture of innovation and collaboration within the organization. Ultimately, by prioritizing technologies that deliver comprehensive security benefits and align with the organization’s overarching goals, organizations can navigate the complexities of the modern digital landscape with confidence and resilience.
Conclusion
The Dual Bastion Model represents a paradigm shift in access control, moving beyond traditional dichotomies of trust and distrust towards a more nuanced and inclusive approach. By integrating the strengths of existing models and embracing new strategies tailored to the needs of modern organizations, we can better protect our systems and users in an increasingly interconnected and threat-prone digital landscape.
In conclusion, the Dual Bastion Model offers a promising pathway toward enhancing access control for modern security challenges. By combining the best elements of existing paradigms and embracing new approaches, organizations can navigate the complexities of cybersecurity with confidence and resilience, transforming their approach to security in the process.
The Author
William Tooley is the Technical Director for Azure and o365 at Novacoast. He’s a seasoned security engineer with two decades’ worth of expertise, specializing in Microsoft Technologies and Information Security.