Remote Access Trojans have existed and evolved since the dawn of malware, with 2024 being no exception in continuing to demonstrate its effectiveness—Hiatus Rat, DarkGate RAT, or the Bitter APT group with WmRAT and Miya RAT all made headlines this past year. From attacks on DVR cameras and targeting of Turkish defenses to vishing attacks in Microsoft Teams—these RATs are everywhere.
In this article, we’re taking a year-end look at recent activity and novel malware techniques utilized by these Remote Access Trojan families.
The HiatusRAT in the Wild
The Hiatus Remote Access Trojan (RAT) was first seen in use in July 2022. At that time, it primarily targeted i386-based DrayTek Vigor routers that were not updated. A Forescout Technologies report shared 14 vulnerabilities that researchers discovered in popular Taiwanese networking devices from DrayTek.
As identified by Lumen Black Lotus in March 2023, the Hiatus campaign targeted over 100 edge networking devices, used compromised routers in its intelligence-gathering efforts, and established hidden C2 (command-and-control) operations.
More recently, analysts say this Chinese-backed malware operation is leveraging Chinese-made smart cameras and video boxes to build a botnet. According to the FBI, this group has been seeding internet-of-things (IoT) devices with malware that allows for remote access and control, with Hiatus targeting both DVR boxes and smart cameras. In addition, cybersecurity companies note that the threat actors were using a range of Taiwan-based organizations to observe a US government server that is used for retrieving and submitting proposals for defense contracts.
In March 2024, a scanning campaign targeted Chinese-made IoT devices in the US, Canada, Australia, the United Kingdom, and New Zealand.
| CVE | Description | Mitigation |
| CVE-2017-7921 | When an application doesn’t properly authenticate users, and improper authentication occurs it can allow a malicious user to escalate privileges on a system that lets them access sensitive data. Note that this has been observed in these Hikvision devices: DS- 2CD2xx2F-I Series V5.2.0 Build 140721 to V5.4.0 Build 160530, DS- 2CD2xx0F-I Series V5.2.0 Build 140721 to V5.4.0 Build 160401, DS- 2CD2xx2FWD Series V5.3.1 Build 150410 to V5.4.4 Build 161125, DS- 2CD4x2xFWD Series V5.2.0 Build 140721 to V5.4.0 Build 160414, DS- 2CD4xx5 Series V5.2.0 Build 140721 to V5.4.0 Build 160421, DS- 2DFx Series V5.2.0 Build 140805 to V5.4.5 Build 160928, and DS- 2CD63xx Series V5.0.9 Build 140305 to V5.3.5 Build 160106. | As of December 13th, 2024, Hikvision has not mitigated this vulnerability across all impacted devices. Hikvision has released updates to mitigate the improper authentication vulnerability in cameras sold through authorized distributors. The updates can be found at: HSRC-201703-04 |
| CVE-2018-9995 | This impacts BK DVR4104 and DVR4216 devices, along with Novo, CeNova, QSee, Pulnix, XVR 5 in 1, Securus, Night OWL, DVR Login, HVR Login, and MDVR Login. These run re-branded versions of the original TBK DVR4104 and DVR4216 series, and allow remote attackers to bypass authentication via a “Cookie: uid=admin” header, as demonstrated by a device.rsp?opt=user&cmd=list request that provides credentials within JSON data in a response. | Currently, there aren’t any security updates to address these flaws. It is suggested that users immediately replace vulnerable surveillance systems with actively supported models. |
| CVE-2020-25078 | Some Dahua devices allow for an identity authentication bypass. Attackers can bypass device identity authentication by constructing malicious data packets. | Some of the affected devices are end-of-life (EOL) devices. Users can find updates for still supported firmware at SAP10180. |
| CVE-2021-33044 | Dahua recommends users download a patch from its website’s Download Center or contact technical support to upgrade to a newer version. | A command injection vulnerability in the web server of some Hikvision products has been discovered. According to analysts, it is due to insufficient input validation that malicious cyber threat actors can exploit this vulnerability and launch a command injection attack by sending malicious commands through messages. |
| CVE-2021-36260 | A command injection vulnerability in the web server of some Hikvision products has been discovered. According to analysts, it is due to the insufficient input validation, that lets malicious cyber threat actors can exploit this vulnerability and launch a command injection attack by sending malicious commands through messages. | It is recommended that users download the updated firmware from Hikvision found at Security Advisories. |
Microsoft Teams Vishing & the Spread of DarkGateRAT
Threat groups continually change their attack methods and find new technology with reputations for spreading campaigns. This current attack, which uses Microsoft Teams and AnyDesk to spread the DarkGate RAT, is another iteration of this practice and an example of how threat actors continue leveraging technical vulnerabilities and social engineering to infiltrate business networks.
Key Findings
Here, we look at some of the fine details surrounding the attack, its consequences, and measures that help prevent these attacks.
Abusing Microsoft Teams
As Microsoft Teams is a trusted platform, the threat actors leveraged it to deceive victims. To initiate the attack by exploiting Microsoft Teams, the attacker used these TTPs:
Bypassing Email Filters: The goal of bombarding the initial email was to overwhelm spam filters and ensure the malware-infused message was delivered to the target’s inbox.
Session Hijacking: Escalating their privileges and deploying malicious payloads was the desired outcome for the attackers exploiting Microsoft Teams.
Spoofed Caller Identity: The attackers used techniques that allowed them to appear as representatives of trusted external suppliers.
AnyDesk Remote Access Exploitation
The next part of the attackers’ plot comes after convincing their targets to download and install a clean version of AnyDesk that allows them remote access by continuing their social engineering ploy pretending to be technical support. This access is then used to deploy additional payloads, including the signature DarkGate RAT. The TTPs used by DarkGate after gaining initial access to the system include:
DarkGate Delivery
The attackers use AutoIt scripting to deploy the DarkGate malware. AutoIt is a programming language often used for automating Windows-based tasks. The TTPs used to carry out the deployment include:
Process Injection: Attackers leverage script-embedded process injection techniques that embed DarkGate into legitimate processes such as svchost.exe or explorer.exe, which helps them avoid detection.
Payload Obfuscation: By heavily obfuscating the AutoIt Script, the attackers were able to evade signature-based antivirus detection.
Dynamic Command Loading: The malware dynamically grabbed more commands from its C&C server, allowing real-time acclimatization to its target’s network and environment.
DarkGate Capabilities
DarkGate is now available as a Malware-as-a-Service (MaaS) offering and offers attackers advanced features. Some of its TTPs include credential dumping, a keylogging mechanism, fileless persistence, and network surveillance.
Attack Indicators
Several indicators of compromise have been identified by Trend Micro researchers from the DarkGate campaign including:
| Indicator of Compromise | Description |
| Suspicious Domains | example-remotesupport[.]com and similar domains used for C&C communication. |
| Malicious File Hashes | – AutoIt Script: 5a3f8d0bd6c91234a9cd8321a1b4892d – DarkGate Payload: 6f72cde4b7f3e9c1ac81e56c3f9f1d7a |
| Behavioral Anomalies | – Unusual outbound traffic to non-standard ports. – Unauthorized registry modifications under HKCU\Software\Microsoft\Windows\CurrentVersion\Run |
Researchers note that
Researchers note that this campaign has been accompanied by other malware delivery and phishing tactics. These include cloud exploitation, file attachment exploits, squishing (QR Code phishing) campaigns, and mobile malware.
Implications
The DarkGate Malware campaign highlights how threat actors have increased the sophistication of their attacks, leveraging legitimate tools for their malicious purposes.
| Advanced Threat Evasion | The use of obfuscation and process injection complicates detection by traditional antivirus solutions. |
| Cross-Platform Risks | The compromise of a single endpoint can serve as a gateway to further network exploitation, endangering sensitive organizational data. |
| Organizational Exposure | The compromise of a single endpoint can serve as a gateway for allowing for further network exploitation, endangering sensitive organizational data. |
Recommendations for Mitigation
Researchers offer these recommendations for mitigating DarkGate malware attacks.
Use Email Filtering and Monitoring: Implementing AI-driven email filtering systems can help detect and block email bombardment campaigns.
Enable Advanced Threat Detection: Deploy endpoint detection and response (EDR) solutions that identify anomalous behavior, such as dynamic command loading and process injection.
Restrict Remote Access Tools: Restrict the use of tools such as AnyDesk to approve use cases with enforced strict monitoring.
Enhance Endpoint Security: Regularly patch and update operating systems and applications to mitigate vulnerabilities.
Educate Employees: Conduct employee training sessions to help them recognize and avoid social engineering and phishing tactics.
Implement Network Segmentation: Segment high-value assets to limit the spread of malware within the organization.
Bitter APT With WmRAT and MiyaRAT
The Bitter APT group has a long history of targeted cyber espionage. In addition, their targets typically include persistent attempts to infiltrate industrial and governmental organizations to collect private data.
On November 18, 2024, researchers observed Bitter APT (TA397) targeting a defense sector entity in Turkey using a spear-phishing tactic. The email included an attachment of a compressed archive (RAR) file that contained a decoy PDF (~tmp.pdf) file that detailed a World Bank public initiative in Madagascar for infrastructure development. It also contained a shortcut (.LNK) file that masqueraded as a PDF (i.e. PUBLIC INVESTMENTS PROJECTS 2025.pdf.lnk[EM1] ), and an Alternate Data Stream (ADS) file that had a PowerShell code.
The phishing email subject line contained “PUBLIC INVESTMENTS PROJECTS 2025_MADAGASCAR.” This matched closely with the shortcut (LNK) attachment posing as a PDF within the RAR archive: “PUBLIC INVESTMENTS PROJECTS 2025.pdf.lnk”.
Researchers note that the use of RAR archives to deliver payloads is a typical component of the Bitter APT group’s attacks. Throughout the first half of 2024, researchers observed the group using Microsoft Compiled Help Files (CHM) contained in RAR archives to create scheduled tasks on target devices.
The Infection Chain
The researchers note that the phishing email came from a compromised government organization account and contained a RAR archive that contained many artifacts. Next to the LNK file, there was a ~tmp.pdf file and two NTFS alternate data streams (ADS). One was titled Participation, and another Zone.Identifier.
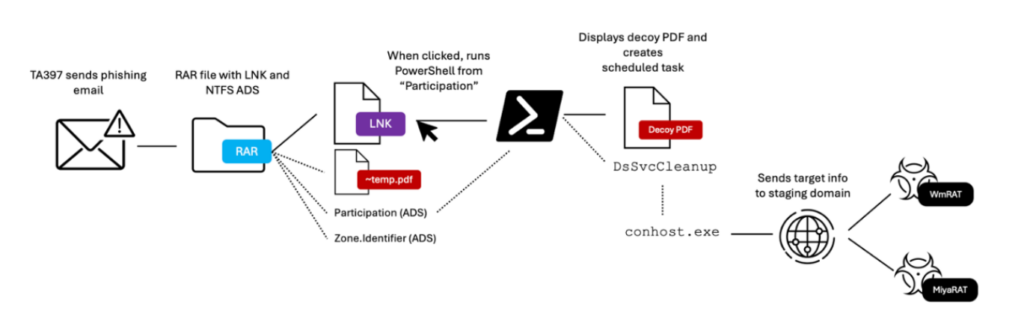
The target only sees the LNK when opening the RAR file because the ADS streams are hidden when the user is using Windows’ built-in RAR extraction utility or WinRAR. In addition, the PDF’s attributes are Hidden, System, and Files Read for archiving.
ADS Streams: These are a feature of the NTFS file system in Windows and allow users to attach data streams to a file.
Zone.Identifier Stream: This is an ADS that originated in older versions of Windows as a security feature. The Zone.Indentifier stores information regarding a file’s origin. It typically includes the URL Security Zone, which determines if the file is trustworthy.
In addition, when files are extracted from a downloaded archive through Windows Explorer they inherit a Zone.Identifier stream with a ReferrerUrl that points to the original archive. While a Zone.Identifier is required for the success of this attack chain, it does provide valuable forensic information.
The Zone. The identifier also holds data about the ~tmp.pdf file that includes its origin.
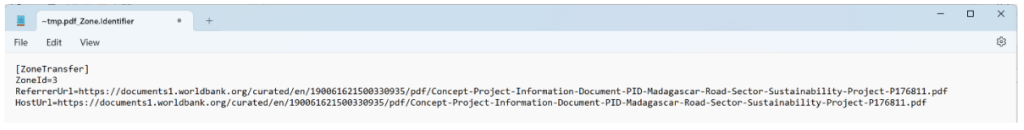
The ~tmp.pdf downloaded from the World Bank organization is a legitimate PDF detailing an infrastructure project on Madagascar’s paved roads. However, it’s being used as a decoy in the phishing campaign.
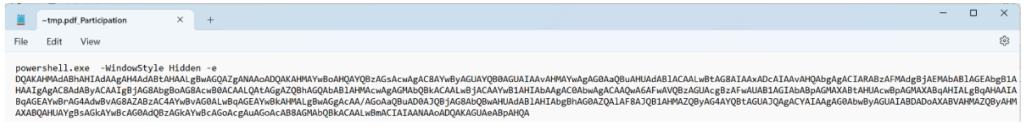
Next is the Participation ADS which contains a blob of base64 Powershell code:
The analyst also noted that the LNK file ran this conhost command:
--headless cmd /k "cmd < ~tmp.pdf:Participation & exit"
This command made the ~tmp.pdf to run the base64 PowerShell file contained in the Participation ADS stream. That decoded to this command:

The PowerShell led to the opening of the PDF lure, which set up a scheduled task, DsSVcCleanup, that attempts to send data over to the target host using the curl utility every 17 minutes to the domain jacknwoods.com. According to analysts, the URL structure is regularly used by TA397. If the retrieval of a payload is successful, the downloaded file is launched using a command prompt.
It is noted that the TA397 operators will respond manually to the requests approximately 12 hours after the scheduled task request that deploys two distinctive payloads, and a third command issues a Post request that contains the data from the enumerated target device.
The first payload downloads and runs anvrsa.ms that installs the WmRAT file abvrsa.exe. Following this, these commands issued start the enumeration of the target machine:

Next the second payload runs the file gfxview.msi
Next the second payload runs the file gfxview.msi:

This payload acted as a dropper and installed “xrgtg.exe”, the MiyaRAT payload. The QiAnXin Threat Intelligence Center was the first to identify WmRAT and MiyaRAT.
The TA397 is an espionage-focused APT prominent in South Asia. It typically targets energy, government, telecommunications, engineering, and defense organizations throughout the APAC and EMEA regions.
Mitigating Threats like the TA397 APT
Security analysts suggest a multipronged approach to combat these threats. These include:
Advance Threat Detection: Leverage AI-driven tooling to detect and identify anomalies, including unusual ADS use or unexpected scheduled tasks.
Awareness Training: Educate everyone regarding phishing tactics so that employees can recognize and avoid deceptive emails.
Incident Response: Develop robust protocols that can contain breaches swiftly to limit damages and liabilities.
Remote Access Trojans: More Risks Ahead
As cyber threats continue to become more complex, these are not the last trojans or social engineering-based threats we will see. Implementing tooling and security controls that detect and block remote access activity is crucial since these malware types lead to other droppers and other further malicious activities such as data exfiltration or ransomware deployments.


