A sophisticated Russian hacking campaign by hackers linked to APT29 (Cozy Bear) successfully bypassed Gmail’s multifactor authentication by using a cleverly designed social engineering attack. The attacks targeted critics of Russia and well-known academics by impersonating US State Department officials. The Google Threat Intelligence Group (GTIG) is tracking APT29 Cozy Bear activity under UNC6293.
According to Google’s Threat Intelligence Group (GTIG), the threat group used extensive rapport-building techniques and tailored lures to convince targets to set up application-specific passwords (ASPs). These techniques are a growing ploy for threat actors. Here we’re taking a deeper dive and breaking down the current threat.
Looking for New Ways In
While some threat group actors are using tried-and-true methods such as phishing for targeted victims’ MFA codes and passwords, many others are seeking out new entry points. Finding ways to bypass MFAs is a current trend, according to a recent report from Cisco’s Talos.
With organizations implementing stronger forms of MFA, including hardware security keys, it’s blocked specific social engineering avenues for threat groups. These pressures, in addition to others, are leading cybercriminals to look towards more complex social engineering techniques and frameworks that are more technically sophisticated, such as the way MFA is targeted.
More specifically, some threat actors are continually experimenting with new and novel ways to get into accounts. These often blend social engineering with account access alternative flow tactics like using access tokens. As previously shared, attackers are now using cross-platform methods where they may reach out to targets on messaging platforms such as Telegram or Signal before moving to other platforms like email. This jigsaw puzzle approach of using separate ecosystems for attack elements makes defending infrastructures against these attacks a challenge for I.T. teams to piece together.
Attacking Gmail App-Specific Passwords
In this attack, the threat attackers used a different technique; it was a personalized and sophisticated novel approach. Researchers at Citizen Lab investigated the Keir Giles ASP attack. The attackers sent an email impersonating an alleged US Department of State official, Charles S. Weber, to Keir Giles, an expert on the Russian military and countering Russian influence operations and information.
The email invited Mr. Giles to an online private conversation. It also included four different @state.gov email addresses on the cc line of the email, including one to Claudie S. Weber’s state.gov address. Security analysts investigating the incident didn’t find any indication that a person named Claudie S. Weber exists or works for the State Department.
It is apparent the attackers knew that the State Department email servers are set up to accept all messages and don’t send any ‘bounce’ responses, even when the address doesn’t exist.
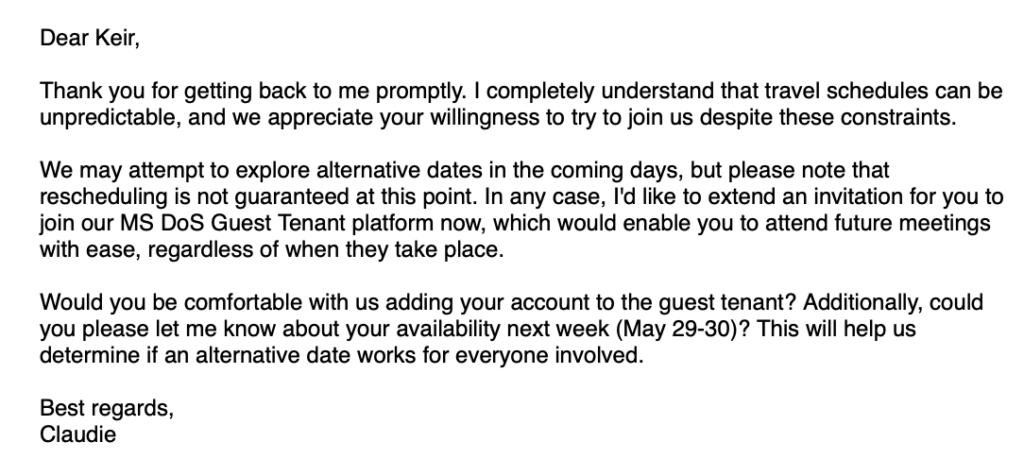
Following several exchanges, the attacker shared a PDF document containing instructions to register for an “MS DoS Guest Tenant” account. The document appears to be legitimate and contains markings and a revision history. It provides a clear step-by-step process for the target on how to create an app-specific password on a Gmail account.
While Mr. Giles was the initial victim of an SPA attack, experts expect there will be similar attacks coming using this method.
Stealing the App-Specific-Password
The next step in this plot is to obtain the app-specific password. The threat actors cover this by explaining in the PDF that it is an alternative method and facilitates secure communication on the platform between external users with Gmail accounts and US Department of State employees. It leads the target to believe they are creating and sharing an app-specific password that will allow them to access the DoS platform securely; instead, they are giving the threat group full access to their Google account.
In addition, the researchers say the way the attack is approached is indicative that they are planned in detail and carried out in a way that tricks victims into sharing the 16-digit passwords that provide the adversary permission to enter their email inbox under the pretext of “secure communications.”
With the passcode in hand, the attackers are then able to set up an email client using the ASP. The likely goal here is to download and read the target’s emails by using VPS servers and residential proxies that help the threat actor to evade detection.
These campaigns began circulating beginning in April 2025 and continued until the beginning of June, according to the Google Threat Intelligence Group (GTIG). The researchers detected two campaigns following two different themes, with one tied to the US Department of State and another tied to Microsoft and Ukraine. Both of these leveraged residential proxies and virtual private services (VPS) in their infrastructure.
Researchers say the threat group used advanced phishing techniques, and the targets were typically individuals involved in high-profile issues related to litigation, conflicts, or advocacy.
Google is recommending those who may fit this profile enroll in its Advanced Protection Program to keep themselves safe from attackers. The program increases the security measures on the account and prohibits app-specific passwords or logging into their account without a specific passkey.
Changing Social-Engineering Techniques
The fact that threat actors are always improving their strategies and tactics should not be overlooked. Users’ expectations of a typical phishing email were not met in this instance due to the slow pace of the conversation and the attacker’s responsive communications with the target, as well as the inclusion of other .gov email addresses on the cc line. It makes it abundantly evident how far a highly skilled attacker would go in order to compromise a valuable target.
When you receive an unexpected or unsolicited email or message, experts advise being cautious. It is best to confirm who you are communicating with when an exchange requests that you share information or change account settings. Getting in touch with the person’s workplace by phone before doing anything else is one way to accomplish this.
Watching Out for ASP Attacks
The services where users can enable ASPs should be closely monitored by security teams, and they should disable them for all users unless certain users or functions require them. Knowledge of ASPs and their effects on personal accounts should be covered in employee cybersecurity education.
Because Google is aware of the risks posed by ASPs and Less Secure Apps (LSAs), Google Workspace users will find that user security has been improved. A plan to phase out ASPs and LSAs was announced by Google Workspaces in 2019. In light of current attacks, the move makes sense.



