3 Steps to Building a Stronger Cybersecurity Program
Even the best-designed security program is only as effective as the quality of its operations and adequate attention given to maturity efforts. How can organizations establish the most effective course that involves strategic planning and clean execution in operating an effective Continuous Monitoring program?
From the perspective of an Advisory & Success team for a MSSP group, the ideal approach to avoiding common pitfalls can be broken down into three areas of consideration: Strategy, Hygiene, and Resourcing. A well-structured program that satisfies the elements of this approach will improve overall monitoring coverage and the ability to deal with detections and incidents.
Before we begin, let’s acknowledge an important fact: an observed 99% of IT Operations are reactive in their response to the organization’s business needs. From minor tasks to major projects, it’s rare to see a proactive or prescriptive process followed. This type of approach creates significant challenges for IT Security Operations as it introduces poor hygiene and doesn’t give security its proper due diligence. From that perspective let’s consider the first challenge:
STEP 1 Strategy
A common misstep in IT Security Operations is when the program follows the same pattern set by IT Operations: a lack of a clear strategy. This is evident when organizations frequently change the frameworks they prioritize. One year it will be NIST, the next NYDFS or HIPAA—depending on the market vertical—and then the following year, yet another framework. There may be other indicators but this is an obvious clue that Reactionary attitudes are typical throughout the organization.
As security practitioners, it’s important to own a level of accountability. It’s important to commit to a strategy and pursue it to an adequate level of maturity. Rather than jump around between security frameworks and cherry pick what’s appealing, let’s commit to developing a program according to two:
- MITRE ATT&CK
- NIST Cybersecurity Framework
Why MITRE and NIST?
MITRE ATTA&CK is a comprehensive framework that documents common offensive tactics or attack techniques bad actors have employed. It helps validate not only your detections but your defenses.
NIST is a well-structured, well-defined, and well-established framework. One can crosswalk to all other major frameworks using it. The alternative is ISO27001 which is popular in Europe.
Looking at GDPR, NYDFS, CCPA, and HIPAA, the main concern is specific to Data Security, which is great, but Data Security should be addressed in your Data Security Program. Follow the “Keep it Simple” (KIS) model to choose the framework that will support setting the foundation to accomplish 98% of your organization’s needs while working to fill unique gaps and reign in outliers.
The second piece missing from most organizations’ strategy is a way to leverage Policy and Standards to identify the controls needed to monitor and determine if there are violations of those controls. This allows identification of malicious behavior or situations when additional cybersecurity training is necessary for non-malicious situations.
Leveraging the correct strategy will help you deal with the challenges of Hygiene and Resourcing later.
STEP 2 Hygiene
What do we mean by Hygiene? Cybersecurity hygiene is a set of standards or best practices that are applied within an organization where individuals perform regular maintenance to ensure the health and security of users, devices, networks and data. If your strategy is properly defined then you should know what hygiene issues should be remediated. So, what is the challenge here?
Too many organizations configure their SIEM to ignore or tune out hygiene issues in their environment, which can create long-term issues, problems, and blind spots where a bad actor can easily evade detection.
One example of an ignored hygiene issue is when service accounts and services aren’t properly maintained. The service accounts will use a cached credential that is no longer valid. This creates failed authentication that can resemble a brute force attack.
This will likely not be a one-time event but an enterprise-wide issue impacting hundreds of service accounts and/or devices. This creates a massive amount of noise which can mask an actual bad actor attempting a real brute force attack.
Faced with this problem, many will make the incorrect choice to tune out those service accounts versus fixing the underlying issue, cementing a blind spot where a bad actor can live with impunity. If the underlying issue can’t be easily remediated then it’s an important reminder that IT Security should be making the organization aware of risks. It shouldn’t try to remediate all risks because that’s impossible; on the other hand, it shouldn’t unilaterally accept risks on behalf of the organization either.
Here is an alternative solution, follow this workflow to integrate your risk management team into your process:
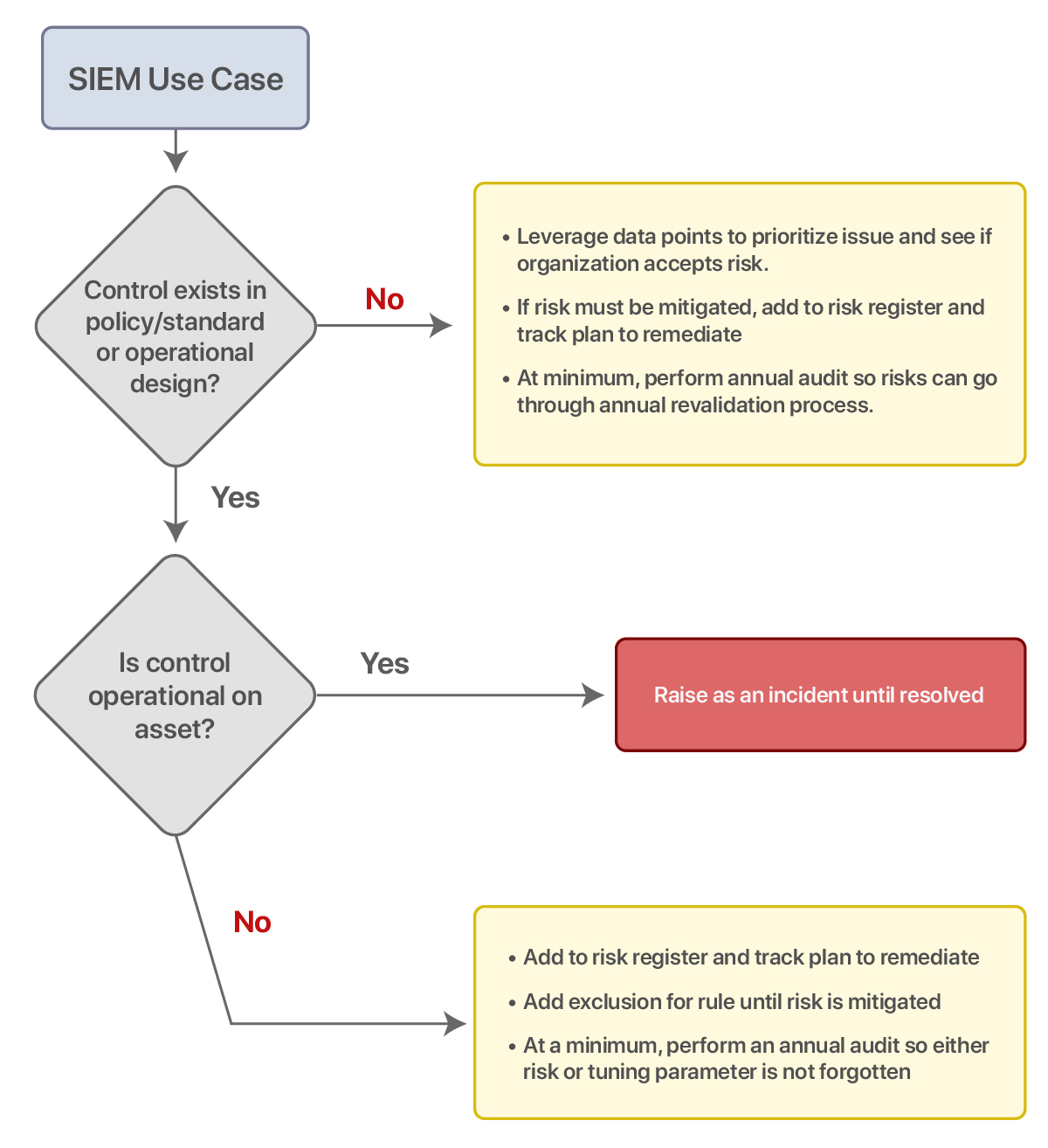
STEP 3 Resourcing
Resourcing challenges: everyone has them. How to be more deliberate in using available resourcing?
Focus and planning are critical to a deliberate approach. Here are 4 highlighted areas that will help with allocation of resources. Keep in mind that control use cases will reference NIST, and IOC use cases will reference MITRE ATT&CK.
1 Reduce Unnecessary Rules
By applying the above strategy & workflow, you avoid implementing SIEM use cases that are control-oriented and don’t fit the purpose. A significant amount of time is lost implementing rules and responding to events that should never have been put into production in the first place.
Before implementing these use cases, validate that a matching control exists in your policies and standards; without that explicit written language, you still have the authority to enforce remediation.
2 Avoid Approval Hazards
Most control-oriented use cases are approved changes, but Tier 1 analysts usually don’t have visibility into the change management system and approval processes. Because of this, Tier 1 analysts can’t verify expected behavior, which creates additional overhead on other security resources, which can escalate to the point where the analyst turns off rules or tunes things out that shouldn’t be. That creates a gap for a malicious bad actor to go undetected.
Fixing this leaves you with three choices:
- Develop an appropriate change management program and process, including giving Tier 1 SOC support visibility of approved changes.
- Accept the overhead of the noise
- Narrow the scope of specific alerting to trigger outside business hours, log the risk until the organization provides the appropriate resourcing level, and/or improve the change management process.
3 Investigation Resourcing Spikes
Organizations must accept that there will be significant resourcing requirements when investigating IOCs.
Two areas where this occurs are:
- The lack of properly resourcing for this need creates an incentive to over-utilize tooling to interrogate a device on potential IOCs and does not always allow for human interrogations. Some people are of the opinion that human intelligence is unreliable, and use it as an excuse to avoid conducting any investigation.
Human intelligence gathering is critical in helping establish confirmable facts, and identifying new areas of inquiry. So human interrogation and intelligence gathering must happen during specific trends or critical events. When and how should be developed in your processes. Once defined you will have a better picture of your resourcing requirements. - There is often a lack of integration with the SIEM where additional contextualization could be provided to the Level 2 analyst and shorten the time to complete the investigation and remediate. There are four core areas that integration helps to improve prioritization & context or initial mitigation:
- EDR
- Threat Intelligence Feeds
- Firewall
- Asset Management / CMDB
4 Identify Gaps
The MITRE framework will help discover unknown business processes. Leverage those data points to improve situational awareness and secure the configuration of assets. That means relevant data is captured and passed along.
Other programs like Asset Management and Configuration Management can benefit and minimize resourcing requirements to re-conduct this discovery in the future.
Conclusion
In conclusion ask yourself: are you providing the right value of service for your organization? How to self-assess?
According to the IT Infrastructure Library (ITIL) Service Strategy, which is a commonly referenced guide for providing services to customers, there are two key examinations for the service you are providing:
- Fit for Purpose?
- Fit for Use?
Examine your program strategy: is it proactive in thought leadership or have you fallen into a trap of being reactive? Is the strategy documented, communicated, consistent, and governed effectively?
Be realistic in the hygiene issues that should be prioritized, and align resources to those tasks. Develop a process to document and discuss risks effectively to all key stakeholders when priority or authority hasn’t been established. If anything in this article gave you an idea for improvement, start making those changes today. The objective is to be in a better position to answer “yes” to both questions and achieve the “value created” statement, while at the same time helping your organization continuously improve on its cybersecurity posture.
Consider Aesop’s Fable “The Tortoise And The Hare”: it wasn’t just the tortoise’s determination that won the race—it was effort, consistency, focus on the end goal, and making many small steps or improvements along the way—all attributes we must exhibit in cybersecurity today.
About The Author
Brian Ehle is the Vice President of Advisory and Success for Novacoast. A 20 year veteran of the IT and cybersecurity industry, he specializes in guiding organizations to optimize their security programs and operations by outlining efficient strategy and coordinating smoother execution of tactics.



