Dan Bowden and the cyber-risk intelligence teams inside leading global professional services firm Marsh have access to a uniquely valuable vantage point. Because the company handles cyber-insurance brokering and incident response support for thousands of organizations, they see how controls perform under pressure when attackers actually strike, and what happens when organizations call in their insurance carriers for help. This produces a dataset no internal SOC or SIEM alone could ever provide.
From that data, one lesson is unavoidable: incident response planning is the best “goalkeeper” in cybersecurity.
After joining Marsh as CISO in 2021, Bowden was promoted to CISO of parent company Marsh-McLennan, where he estimates roughly 5,000 employees are involved in cybersecurity.
At the 2025 Fall Cybersecurity Summit in Scottsdale, Arizona, Dan expounded on some of the conclusions they’ve made based on their research.
The “Goalkeeper” Model: Which Controls Make Real Saves?
Leaning on a classic sports analogy drawn from one of Marsh’s data scientists: if every attempted compromise is a shot on goal, then a breach represents the ball slipping past the net. The best cybersecurity controls are therefore the ones that make the most “saves.”
Instead of evaluating controls on theoretical value or vendor claims, Marsh evaluates them by historical performance—what prevented real breaches for real clients.
Incident response planning consistently ranks as the most effective control in this model. He explained why: it is the discipline that determines whether a detected incident becomes a contained event or escalates into a reportable, costly breach. When organizations decide in advance how to classify incidents, trigger escalation, communicate internally, and coordinate across legal, compliance, IT, and business leadership, they significantly reduce the odds that an attacker gains room to maneuver.
The Marsh Cyber Risk Intelligence Center
The Marsh roster is stacked with former CISOs, former threat hunters, and people who’ve worked at big threat intel companies. They analyze the information captured from Marsh clients on actual cyber events and breaches, then crunch all of it to put together a model that show you what to watch out for in your networks.
Even more interesting is that Bowden finds there is a need to discuss nuance and distinction as it pertains to incident response. Depending on your team’s current focus, this can mean different things to different people and there are multiple functions within incident response.

The above image groups the various silos of Marsh focus—it’s the big picture. It not only includes cybersecurity but everything else they’re trying to accomplish. He jokes that they’re looking for ways to sell insurance faster but honestly, they work on innovative ways to solve problems for their clients.
The example he shared was an auto manufacturer importing parts. They thought they were safe because their parts all come in through a single vendor, but what Marsh discovered is that the vendor was also acquiring these parts from all over the world from other suppliers.
This translated into additional cyber risk although this specifically seemed more of a geographic exercise. Marsh also does every kind of insurance brokering and has insight into the claims being filed.
Data That Paints a Changing Security Landscape
Marsh’s biannual global survey shows how control maturity has evolved. Some changes were dramatic. Patch-window adherence for high-severity vulnerabilities, for example, jumped from 24% implementation to 89% in two years—likely influenced by regulatory pressures such as the UK’s Cyber Essentials and Europe’s DORA operational-resilience requirements.
Other shifts were more modest but still meaningful. Endpoint detection and response (EDR) deployments climbed, but Bowden noted a gap between buying a control and implementing it with full coverage and proper tuning. Organizations, he emphasized, could no longer assume that acquiring tools alone would move the risk needle.

Across the board, the data consistently reinforced that preparedness—not tools—is what separates mere detection from actual containment.
Why Incident Response Planning Outperforms Everything Else
Dan Bowden broke down “incident response” (IR) into its functional components. The part that matters most for preventing breaches is the pre-incident planning phase, not the firefighting that happens once attackers are already inside.
IR Planning vs. Other IR Functions
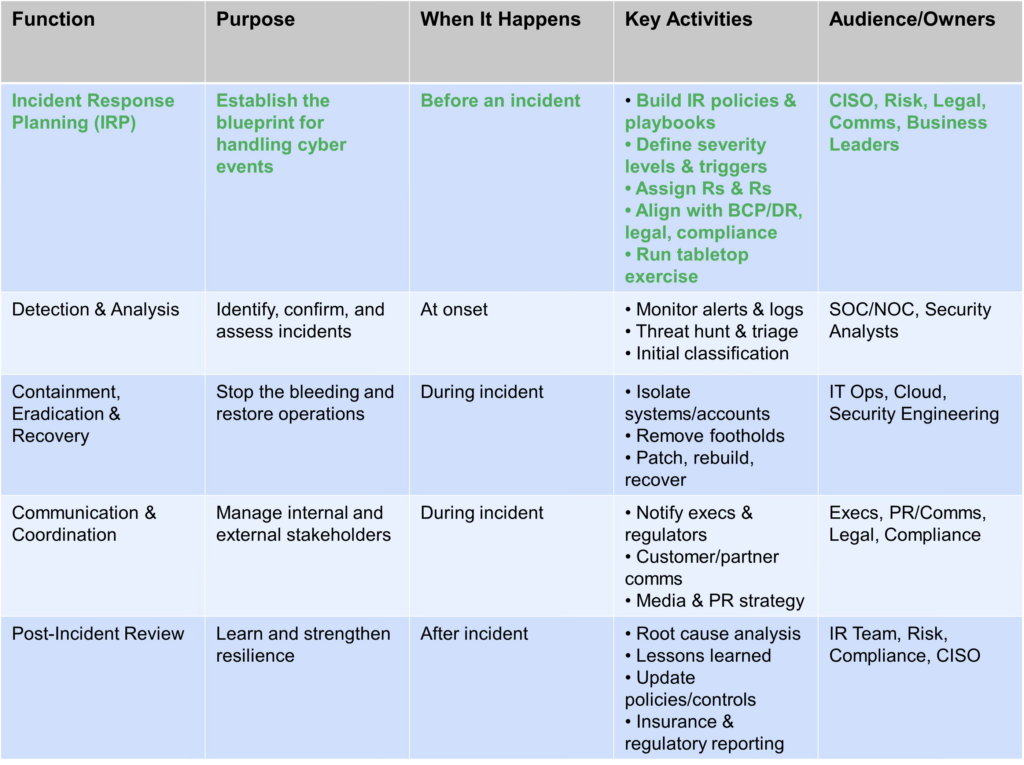
Marsh’s highest-performing organizations invest in:
- Clear incident classification and severity frameworks that executives, counsel, and technical teams all understand.
- Pre-built runbooks for ransomware, data exfiltration, business email compromise, DDoS, and cloud-service disruption.
- Pre-approved communication templates so public messaging does not stall or create reputational damage during chaos.
- Cross-regional tabletop exercises, especially in global organizations where cultural norms, languages, and operating structures differ.
He shared that Marsh conducted approximately 70 tabletop exercises in a single year—more than the number of weeks available. The point wasn’t volume for its own sake, but understanding how different leadership teams react under stress, what their escalation instincts are, and where friction or uncertainty could cause delay when a real incident strikes.
Regulators increasingly demand this rigor. DORA in Europe and similar frameworks in the UK now require testing of business continuity, technology resilience, and coordinated incident response. Bowden noted that this marks a welcome shift: compliance is finally reinforcing good security rather than distracting from it.
Insurance Carriers Are Getting Tougher—And Better
The cyber-insurance market’s dramatic recalibration after the ransomware surge of 2020–2021 taught carriers hard lessons. Underwriting became more stringent. Self-attestation is still the norm, but insurers now probe deeply asking for tooling details, deployment coverage percentages, and sometimes requiring third-party validation.
Dan also observed that insurers are increasingly rewarding organizations that can demonstrate not just tool adoption but control effectiveness. Mature incident response planning is one of the few levers consistently shown to reduce both the likelihood and cost of breaches, so it significantly influences premiums and coverage decisions.
Incident Response Planning Is the Goalkeeper That Saves Businesses
From Marsh’s global incident data to his decades of operational leadership, the conclusion is blunt: incident response planning is the highest-value control in cybersecurity today. It is the goalkeeper that makes the most saves, provided organizations commit to building, practicing, and continuously refining their playbooks.
Bowden closed with clear guidance that aligns with Marsh’s data:
- Prioritize pre-incident planning above all else. Tools matter, but without rehearsed processes, they won’t stop a breach from becoming a crisis.
- Integrate legal, compliance, business continuity, disaster recovery, and executive leadership into the IR process. A siloed IR team is a failing IR team.
- Run tabletop exercises relentlessly—and globally when applicable. The value lies not just in testing technology, but in testing decision-making.
- Practice how to communicate. Silence during an outage creates reputational damage faster than the outage itself.
- Update plans continuously. Each exercise reveals weaknesses; each weakness fixed improves resilience.
Dan emphasized that proactive work is always harder than reactive firefighting, because it competes with daily operational demands. Yet organizations that invest early reap the benefit when it matters most: they avoid the breach, or at minimum contain it before it spirals into a damaging, reportable event.
As security professionals we already know that breaches are inevitable. Dan Bowden’s presentation reframes the challenge: inevitability doesn’t have to mean inevitability of impact. Implementing strong IR planning is the key difference between an event and a disaster. It’s where modern cyber-resilience truly wins.


