Magniber emerged as the little guy ransomware group in 2017, but more recently it has managed to make new moves without gaining much attention, despite its effects being catastrophic to victims. Its evolution of clever TTPs along with its relative obscurity and brutal effects make it particularly dangerous.
In this piece, Novacoast’s Elise Manna-Browne takes a look at Magniber from the perspective of a threat hunter: how it is distributed, how it infects systems, and what your business should do now to protect itself from this very serious cyber threat.
Key Points:
- Not much public research available on Magniber ransomware, despite its brutal effects
- Cleverly spoofs PTR records of legitimate origin servers.
- Continues to remain mostly in the dark and has avoided getting its infrastructure blacklisted, which is concerning.
- Take action to mitigate the threat of a successful attack.
Background
While the name may be a challenge for some to pronounce (we say mag-nuh-bur), it is a very dangerous threat. Magniber has been around since 2017, but its roots as an exploit kit go back as far as 2013. And for a malware with such a long history, it is odd that you don’t hear more about it.
Most ransomware kits behave very similarly to Magniber. There are many crossovers, and you won’t see many differences in how they execute or what they do beforehand.
The differences appear in the executions post-exploit, with the name “Magniber” appearng to be derived from the exploit kit that was delivering it. Consider this similar-sounding chain of malware:
MAGNITUDE EK (and others) > MAGNIGATE (malicious adware) > FAKE BROWSER or OS UPDATE
Why Is Magniber Important
This specific ransomware didn’t have a lot of public research available. However, more recently, there’s been some buzz about changes in its TTPs—now delivering ZIP files containing JavaScript payloads from malicious ads on the internet.
Of course, the group could attach a ZIP file to an email for payload delivery, but it doesn’t appear they’ve taken that step yet—to use phishing campaigns as an initial access vector.
Hewlett Packard reported the change that Magniber is now dropping JavaScript payloads, but what is particularly interesting is it was more recently determined that the JS files did not carry the Mark-of-the-Web (MotW)—a vulnerability discovered in Windows that has since been patched.
A deeper look into Magniber reveals it has used both JS and JSE file types, but also WSF, CPL (DLL), MSI (still seeing this reported by Malware Bytes Threat Intelligence as recently as October 17th, 2022), or EXE file types. It has even been observed returning to its roots in exploiting the browser itself.
It’s interesting that what the industry seems to consider a fairly small ransomware family that hasn’t received much attention uses such a dangerous and difficult-to-detect behavior: a fileless infection chain that leverages previously unnoticed Windows zero-days (MotW evasion) and uses additional behaviors such as bypassing EDR/AV by using direct system calls.
Magniber Continues To Evolve
While Magniber has been in the wild for a while, security teams are seeing these new moves by the ransomware family:
– In 2021, the Magniber group was observed exploiting PrintNightmare, and while other groups were also doing this, it was noteworthy because it appeared to indicate the group was “leveling up” in their activities by using newer methods of attack. And as cited above, in 2022, they were observed going back to exploiting browsers such as Edge and Chrome.
– The big reason we’re looking at Magniber is the fileless infection chain. When you take a look at some security blogs that go back as far as 2021, victims are noted as being primarily in South Korea, with some chatter of victims in Italy. However, it would be within the realm of reason that a highly effective malware family would expand its reach over time.
– We know there are many types of infections that will run primarily in memory because fileless payloads make the infection much more difficult to detect. Another way Magniber evades detection is by using direct system calls instead of Windows API calls—the latter being that which most EDR technology monitors.
Targeting Home Users
In recent updates, Hewlett Packard noted that based on the Magniber code, there were identifiers pointing to specific operating systems that it targets, which correspond to personal computers. This is also common to see in the code of many malware families, where it fingerprints the OS so that the right version of the payload is launched.
The code identifiers indicated the ransomware was targeting Windows 11, and this included the pre-release versions. Based on the findings and the fact that this ransomware has always been a single-system-focused one, HP concluded Magniber is primarily targeting home users.
Magniber has not yet been observed as being paired with any worming or spreading mechanisms to infect more than one machine at a time; however, this would be the next logical step in its evolution.
How Magniber Executes
Let’s look at a few examples of how it executes. It begins by obfuscating the JavaScript payload and executing it with wscript upon user click and then uses a variation of DotNetToJScript to load into memory.
The .NET payload then decodes shell code using direct system calls (evading detection by not using Windows API libraries), and then injects itself into a new process. This shell is then used to delete volume shadow copies (a common ransomware behavior) and disables backup services via VBScript loaded into the registry via the following command lines (depending on campaign/variation):
wbadmin delete * -quiet
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled no Another interesting component is that Magniber will bypass User Access Control using fodhelper.exe. For this component of the threat to work, however, the user must be in the administrators’ group.
Knowing this can be helpful if you don’t have many users in the admin group; it’s a bit of a relief. What’s strange in this scenario is the running of fodhelper. It’s not usual to see this in ransomware families. Threat hunters can use this and look into fodhelper activity to search for any anomalies.
So far, the group doesn’t seem to target other types of backup services, such as Adata or Veeam, but this code is already used in the wild by other groups. It also does not appear to be attempting “double extortion,” where data is stolen and ransomed in addition to the ransom payment being used to decrypt infected hosts.
The Ransom Note
Below is the original ransomware note from when Magniber was doing fake software updates. The referenced .onion site has no data on it, and there’s no evidence that the group is leaking any data. They just want to collect payment from the victims to decrypt the system that’s encrypted.

What’s interesting in the four URLs referenced here is these domains are all scooped up and purchased by the attacker. They are malicious domains. The subdomain listed here is actually a victim identifier and also a subdomain of the onion site. It’s how they are tracking their victims.
The domains are interesting because they are part of a bigger web that isn’t really getting attention currently. We’ll look at that next.
In the next version of the ransom note you see a change to the design that you could say is an improvement. On the ransom note page, you just press the button to pay for the “My Decryptor” software and that takes you to site to make the Bitcoin payment.
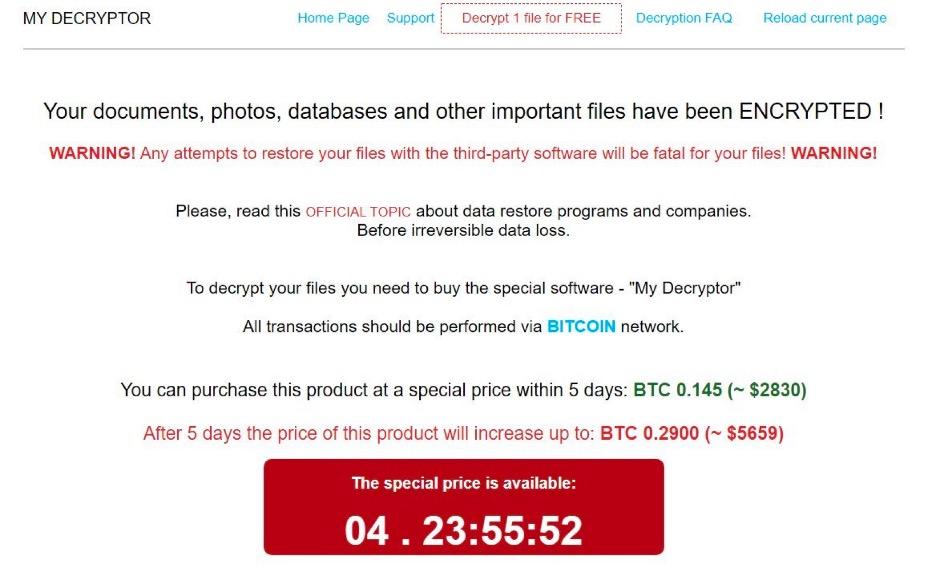
The ransom appears to be a moderate amount of around $2,800 in Bitcoin, theoretically due to home user targeting. But when that is multiplied by the number of systems in an enterprise environment it becomes a huge number very quickly. For example, if multiplied by 5,000 endpoints, it $12.5M.
Another thing that is notable here is the countdown. There is a support option, but there’s no evidence of anyone having used it, so it’s not clear what kind of support will be provided. Typically, ransomware group support is limited to helping victims to pay the ransom and beyond that they don’t support anything at all.
Magniber Ransomware Pay Domains
We dug into the pay domains identified by Hewlett Packard and were able to expand on them using pattern analysis and IOC enrichment. You can see the domains co-located on these IP addresses follow similar patterns and use some top-level domains in common. Although we cannot say these domains are being used for Magniber specifically, they appear at minimum to be part of the same malicious infrastructure:
| Root | TLD | IP Address | Date (VT) |
| fitpull | quest | 104.156.253.46 | 10/20/22 |
| fineher | monster | 104.156.253.46 | 10/19/22 |
| fewease | uno | 104.156.253.46 | 10/19/22 |
| bothhes | fit | 104.156.253.46 | 10/19/22 |
| eyeswhy | quest | 104.156.253.46 | 10/19/22 |
| drawsbe | space | 104.156.253.46 | 10/19/22 |
| anyputs | uno | 104.156.253.46 | 10/19/22 |
| deepson | uno | 104.156.253.46 | 10/18/22 |
| addrare | space | 104.156.253.46 | 10/18/22 |
| boxyet | space | 104.156.253.46 | 10/18/22 |
| cycleis | space | 104.156.253.46 | 10/18/22 |
| getshit | quest | 104.156.253.46 | 10/18/22 |
| getloan | uno | 104.156.253.46 | 10/18/22 |
| forunit | quest | 104.156.253.46 | 10/18/22 |
| flagcan | quest | 104.156.253.46 | 10/18/22 |
| needhas | 209.94.57.131 | 10/19/22 | |
| badif | 209.94.57.131 | 10/19/22 | |
| bigheat | 209.94.57.131 | 10/19/22 | |
| frysan | 209.94.57.131 | 10/19/22 | |
| intoto | 209.94.57.131 | 10/19/22 | |
| airking | 209.94.57.131 | 10/19/22 |
From here it was pretty simple task to take the domains and look at the associated IP addresses to note that until recently there wasn’t a lot of activity. Previously, there weren’t any other domains on these IPs or any other related threats. That doesn’t mean, of course, that there is not older infrastructure elsewhere.
Our research got weird when we began to look into the JARM fingerprints for these domains. What’s disturbing is that the JARM fingerprint on all of these identified domains matches over 770,000 other sites, while instead, this should be a (at least relatively) unique fingerprint (by design) that allows the tracking of malicious infrastructure. JARM spoofing is a method of detection evasion used to make malicious sites blend in with benign domains. For instance, when you look at the 209.94.57.131 IP address and do a reverse DNS lookup, it comes back to a fingerprint that actually matches ip.stat.example[.]com.
The technique is interesting because JARM fingerprints can be used to identify attacker infrastructures—that is what it’s designed to do. For example, in the case of Trickbot and Cobalt Strike, researchers are using these fingerprints to identify those botnets, just as we’re showing here.
When dealing with over 770,000 different sites it’s not a very effective way to identify anything. No one will want to comb through all of it to find the one or two that may be legitimate or malicious.
Toward the end of 2021 is when we see a large uptick in JARM fingerprint records for the spoofed fingerprint which coincides with an increase in Magniber activity.
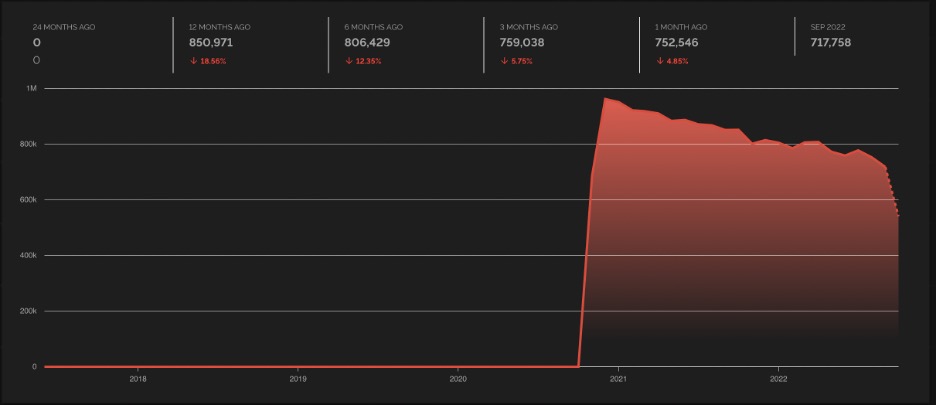
For the domains and IPs we researched, the hosting providers were Choopa and UpCloud USA.If you look at this fingerprint spoofed by Magniber where the domains are also hosted on Choopa (known for hosting VPN as well as C2 nodes), you see a large spike and then it just drops off.
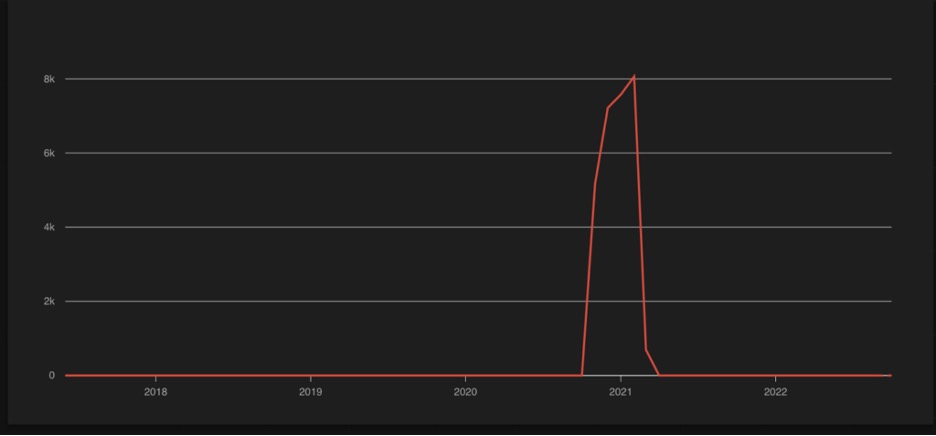
It then appears to correspond to an increase of this JARM fingerprint being used on UpcloudUSA.
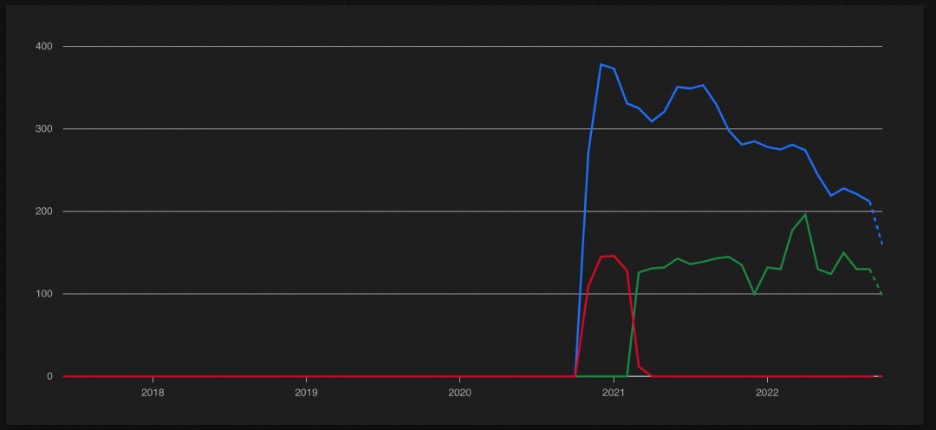
It’s not apparent at this time what the drop in usage at end of 2022 corresponds to—it could be a different JARM fingerprint, different hosting provider(s), or decrease in Magniber activity.
Going in further and looking at the IP addresses such as this one: 104.156.253[.]46; If you visit this IP address directly you will find a random iPhone ad in Korean. Searching using the image of the iPhone on the site reveals many other sites that contain the same lure.
It’s a bit strange for a pay domain because when you visit it directly it’s showing an ad to buy an iPhone at some special deal price, but the same IP is holding all the domains for ransom payments.
Using the image file to search elsewhere on the Internet, the result is a list of all kinds of different domains, none of which are identified as Magniber anywhere else. Most weren’t even flagged as malicious in VirusTotal. The image below is example from searching in URLScan.io:
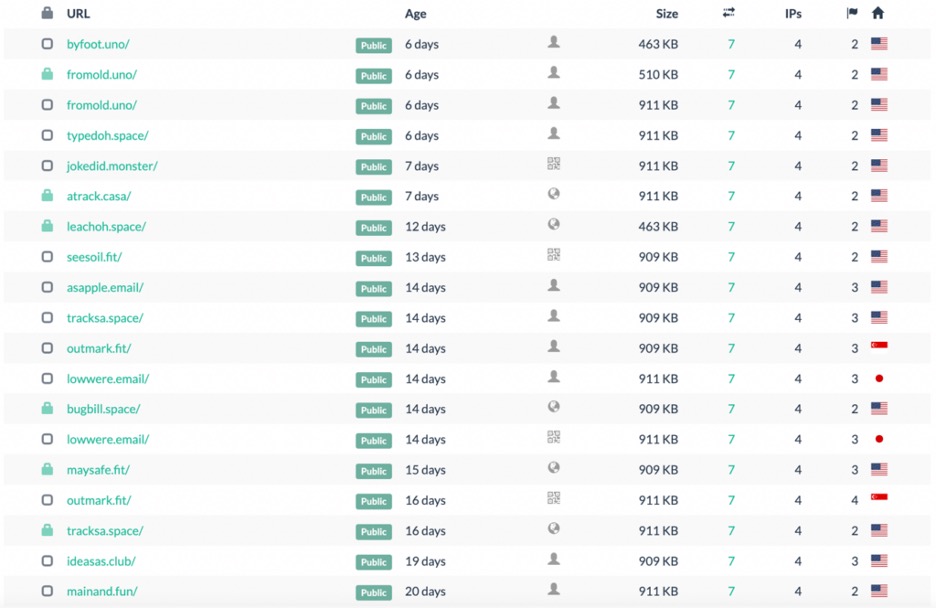
All of these sites contain the same iPhone ad on them. Going through the list, there appears repeated top-level domain usage that’s the same as observed in the Magniber-derived IOC set, such as [.]email and [.]space. Going deeper reveals some JARM fingerprints that continue to match up, for example:
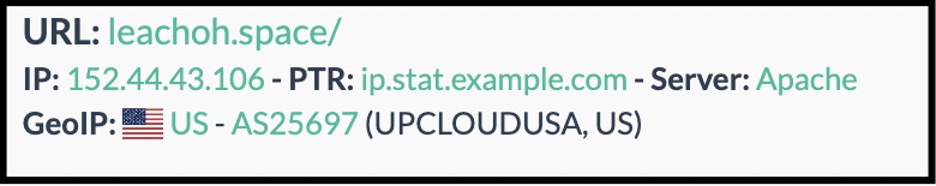
In this breakout, UPCLOUDUSA is the hosting provider and the reverse DNS issue mentioned earlier is found again.
All the pieces of the puzzle are coming together with the ad sites for the domains being part of the malicious ad portion of the botnet. They’re sharing a lot of indicators in common with the payment domains from the ransom notes in the first list of IOCs.
It’s very likely that this infrastructure is linked and if we dig further into the IP address it will reveal even more domains in the web—that tends to be how these things are expanded out. The reason this is important is none of these were flagged.
Conclusion
Even the best intel provider may not have this information about Magniber behavior, at least not at this stage. While these domains will change, the top-level domain thing is very underestimated. If you can block these from your emails and in your firewall, you can save yourself from a lot of hassle.
Spoofed PTR records whose servers are replaying server hellos from other “benign” hosts, basically spoofing these are likely responsible for the JARM fingerprint collision. So, all the data it requires to calculate the “unique” fingerprints is being spoofed by the threat actors to look like those 770,000 sites out there.
For a ransomware family that isn’t very prevalent based on the research available, and is supposedly targeted toward a single country, they have done an excellent job protecting their infrastructure from getting blacklisted. When you combine the fact that they are making sure their infrastructure isn’t flagged with the increase in domains being registered in 2022, it is a concerning and unresolved question.
Action Items to Block Magniber Payloads
Here are some things that can help proactively identify the Magniber threat:
- Match PTR records that come back from domains being contacted and make sure they match the host. There will likely be false positives according due a large number of Email Service Providers such as Mailchimp, Hubspot, and others that don’t update their records (source: Trustwave.)
- Compare rDNS with A records and if it doesn’t match it should be blocked, or at a minimum, examined further.
- UAC Bypass will only work on users in the admin group, so following the concept of least privilege can prevent this component of attack.
- Monitor or conduct threat hunt activities around
wscript,wbadmin,bcdedit, andfodhelper. - Threat hunt the following command lines (sample—you will want to wildcard the random alphanumeric string):
rundll32.exe Shell32.dll,Control_RunDLL
loaddll64.exe “C:\Users\{user}\{folder}\System_Update_Win10.4a4793a31463b.cpl.dll” - Block unwanted TLDs at the perimeter for email and firewall. This is generally a good move but results may vary.
The Author
Elise Manna-Browne is an expert in threat intelligence, threat hunting, phishing, incident response, penetration testing, and malware analysis. She is the VP of Emerging Technologies at Novacoast and leads their cybersecurity incident response team.


