The US National Institute of Standards and Technology (NIST) has launched the anticipated update to its Cybersecurity Framework (CSF). The new framework expands on the draft it shared in September 2023 and cites President Biden’s National Cybersecurity Strategy, including an emerging government cybersecurity statement.
The new policy expands its scope to provide cybersecurity protection for organizations of all sizes and industries, rather than its previous focus on critical national infrastructure. The previous version, formally named the “Framework for Improving Critical Infrastructure Cybersecurity,” has now been officially branded to match its common name: the NIST Cybersecurity Framework.
What’s Changed in NIST CSF?
It’s been nearly a decade since NIST made changes to the Cybersecurity Framework. The new version includes updates to address current and future cybersecurity challenges across all types of technology environments, including cloud, mobile, and AI systems. In addition to the core five pillars (Identify, Detect, Protect, Respond, and Recover), NIST has added a new Govern function, designed to help organizations make and carry out informed decisions on cybersecurity strategy.
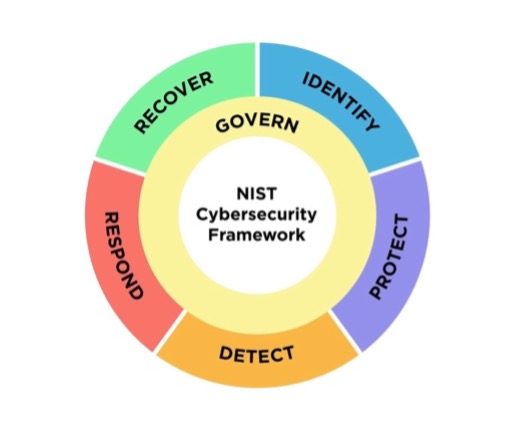
Significant changes to the CSF include:
- A shift in focus from critical infrastructure to a more balanced framework that will help everyone. The move to change the title was to share that expanded view.
- The addition of the Govern pillar, which is meant to round out the main functions of a mature and robust cybersecurity program. The intent of the new Govern pillar is to guide internal decision-making and decision implementation.
- The CSF now includes profiles that it hopes will expand and improve guidance on how to implement the CSF. It also provides a broad range of resources that include quick start guides and illustrations developed with smaller businesses in mind.
The Framework Includes
The CSF 2.0 is meant to help businesses understand, communicate, and prioritize cybersecurity threats, in addition to NIST’s other tools. Encouraging both internal and external communication at all levels, from the C-suite to mid-management and internal teams, will prove extremely useful.
CSF Core
Most firms can manage cybersecurity risks with the aid of the CSF Core, a taxonomy of high-level cybersecurity outcomes.
It provides all companies with the flexibility they need to handle technology, specific hazards, and mission concerns; the outcomes are tech-neutral, sector-neutral, and country-neutral.
Furthermore, regardless of their degree of cybersecurity experience, managers, executives, and practitioners can all readily understand these results.
CSF Organizational Profiles
A CSF Organizational Profile is what describes a business’s current or target cybersecurity posture based on core outcomes. These profiles help understand, tailor, prioritize, assess, and communicate core outcomes, taking into consideration the organization’s stakeholder expectations, mission objectives, threat landscape, and requirements.
When these are in place, a business can then prioritize its actions so that specific outcomes are achieved and the information is shared with stakeholders.
Each Organizational Profile includes one or both of these:
Current Profile
These profiles specify the Core outcomes the business is achieving or attempting to achieve now.
Target Profile
This profile specifies the outcomes the business has selected and prioritized to achieve its cybersecurity risk management objectives.
An organizational profile can be used to help shape the continuous improvement of its cybersecurity.
- Scope the Organizational Profile
- Gather the information needed to prepare the Organizational Profile
- Create the Organizational Profile
- Analyze the gaps between the Current and Target Profiles to create a plan of action
- Implement the action plan and update the Organizational Profile
Since continual improvement is critical, a business can repeat these steps frequently and as much as needed.
CSF Tiers
CSF Tiers inform the Current and Target Profiles and characterize the strength of a business’s cybersecurity risk governance and management practices. These provide context for how a business sees cybersecurity risks and the processes it has in place to manage them.

When using tiers, businesses should seek to complement their already existing cybersecurity risk management methodology, not replace it.
Other Risk Management Programs
With all the risks to privacy, supply chains, AI, and many others, all businesses are using many tools and resources to keep networks protected. Every business takes different measures to monitor risks at the level they need.
The Cybersecurity Framework is critical to helping businesses translate their terminology for cybersecurity risk management and cybersecurity itself into general risk management language so that everyone, including executives, can understand it.i’ve beeni
The CSF is beneficial for integrating cybersecurity risk management in these use cases:
- Cybersecurity risk management and assessment
- Privacy risks
- Supply chain risks
- Risks from emerging technologies
CSF Resources
Businesses can use the CSF Core, Profiles, and Tiers in addition to supplementary resources to understand, assess, prioritize, and communicate cybersecurity risks to stakeholders and others. The National Institute of Standards and Technology has included many resources on its website to assist businesses in understanding and implementing the Cybersecurity Framework 2.0 (CSF).





