“If you know your enemy and know yourself you need not fear the result of a hundred battles.”
Sun Tzu
Defending your organization against cybersecurity threats is akin to stepping into the shoes of a military general, cultivating careful analysis of known attack behaviors and developing a strategy to counter them. Luckily, at our disposal we have a powerful weapon: the MITRE ATT&CK Framework of Tactics and Techniques. Originating in 2013, it has become a well-established security tool and is invaluable in mapping security battles.
Security engineer Graham Guletz wasted no time before diving into what the MITRE ATT&CK framework looks like during his presentation at the 2021 Innovate Cybersecurity event this October. After explaining that MITRE offers a few different framework options for different scenarios, he focused on the biggest question that always seems to accompany the conversation:
“MITRE ATT&CK is amazing, but… how do I implement it?”
Know Your Enemy
Implementing the MITRE ATT&CK framework is the process of understanding how threat actors behave in your environment, and putting logic in place to detect these actions. Ultimately it leads to being better able to defend your organization against attacks including malware, phishing, and ransomware attacks.
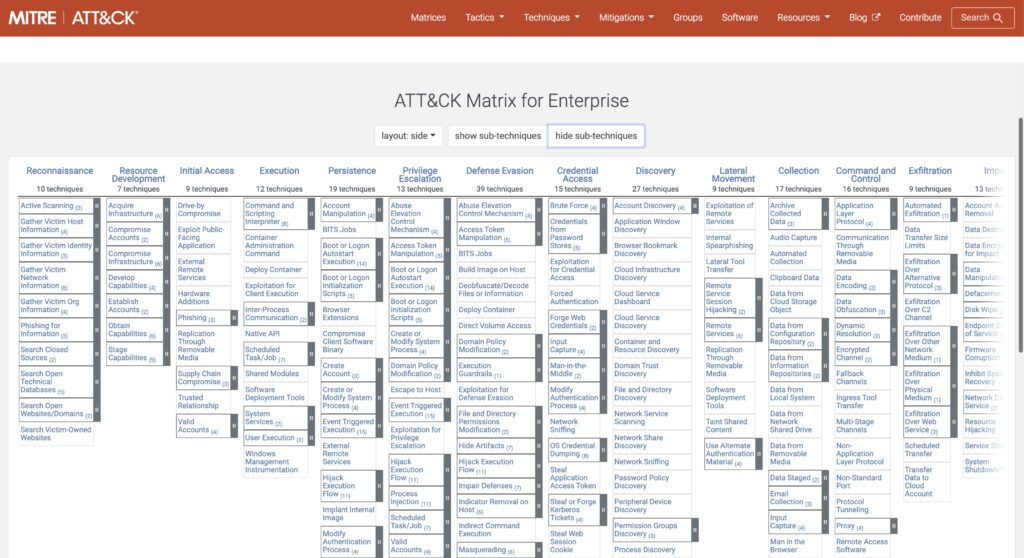
But what does implementing the MITRE ATT&CK framework look like? In the context here, it refers to how we detect these behaviors in our environment.
The MITRE ATT&CK framework is made up of tactics or objectives a threat actor may attempt to achieve on a target system. In the Enterprise MITRE ATT&CK framework there are a total of 14 tactics, and under each is a series of sub-objectives called techniques. Each of these represents the end goal of a threat actor’s behavior, such as successfully gathering network information, escalating privileges, or exfiltrating data.
Overall, MITRE ATT&CK is built to be an abstract framework, and intended to be interpreted and implemented by your organization based on your uniquely identified threat profile and utilized technologies. Different groups will interpret the framework very differently through their own lens.
Gather Intelligence
The first phase of implementing the MITRE ATT&CK framework is a mission of gathering intelligence. This includes identifying the characteristics of the organization. Start a list containing your organization’s key characteristics and identifiers such as industry, products, services, geographic location, and who you do business with. Then set these as keywords — these bits of classifying information assist with identifying which threats, threat groups, and other foes are targeting your organization.
MITRE has a wealth of resources that assist in utilizing these characterizing markers to identify threat actors and threat groups that might have your organization in their sights.
For those new to using ATT&CK, the MITRE website provides a searchable list of threat actor groups as well as useful details about them. Pick keywords from the list based on your organization and search on it to find useful relevant information.
For example, searching “healthcare” on the ATT&CK site will bring up a list of threat actors known as APTs (advanced persistent threats) that target that industry. This provides an excellent starting point and indicates what groups to focus on and the techniques they use.
An in-depth look at specific APTs includes information in the description which can help filter out APTs that may not be relevant to your industry or company. For those you deem as relevant, note the techniques that these groups are known to use. Exploring this intelligence base, finding several threat groups that are relevant to you, and noting the techniques they use is a good starting point in building out your detection logic.
To take this a step further, consider looking outside of MITRE’s website, and utilizing alternative sources of information to manually map threats to ATT&CK techniques:
- External Threat Intelligence – this can come from a service, feed, or be developed internally through research to determine what threats are targeting your industry.
- Manual Mapping – consider what threat actors are trying to achieve in their attacks, then using the MITRE ATT&CK framework manually, map it to your organization. This will require a bit more time and effort.
Extract Techniques
While lists are great, the MITRE ATT&CK Navigator takes the data to a new level. It’s a fully customizable visualization tool on the website that lets you take control and add color coding, filters, and scoring for all the different techniques from the ATT&CK framework.
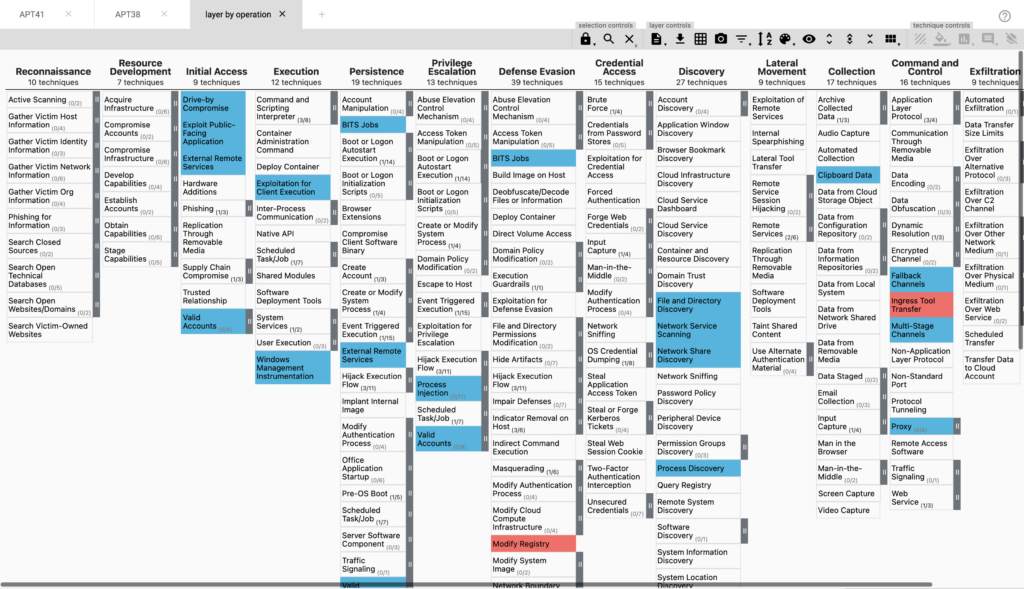
This data lets you prioritize the techniques you want to focus on for your organization. The more data you gather, the more layers you will have and the more comprehensive scoring will be for the techniques.
More groups and more scoring variables in your matrix will help to define the hierarchy in detection for your organization.
Analyze and Organize
To get detection rules in place that allow you to gain good visibility on your environment, you need good data.
Where does this data come from?
There are a few standard resources that an organization can leverage for whatever detection tools it is using:
- Process/Command Line Monitoring
- File/Registry Monitoring
- Authentication Logs
- Packet Capture
Each provides additional visibility into what is going on for all your systems in your environment.
Looking at the details of the MITRE ATT&CK cataloged techniques, each includes a list of potential data sources that can be used. Using these ideas may help you capture this behavior, i.e. once you know which data sources are related to a particular technique you can reconcile any qualifying data sources in your own environment.
A common question is: where does the data go and where to build detection logic?
There are two tools frequently discussed that are robust in developing this upstream element of security data: A SIEM, and XDR.
SIEM began as a log management tool that developers overlaid with detection rules. Historically it is built around defined rules for detections with extensive alarm rule functionality.
XDR has some decidedly SIEM-like features at its core, but expands on this by including open integrations. These may allow you to bring in data from additional sources, while some XDR tools go beyond logic with the addition of anomaly-based detections.
Develop Tools
Assuming the tools are in place, the next question is: how do you implement detection logic for ATT&CK techniques in your environment?
If you don’t have the specific data needed in your organization or don’t have the right tools to produce it, there are two helpful datasets available on GitHub that can be used to test and validate your detection logic:
- Boss of the SOC – is a dataset developed by Splunk
- BRAWL – is a dataset managed by MITRE
These contain historical threat data that can be either pulled into a SIEM or the tools you have available now to begin building detection logic. These will work to get your own data production process in place. The datasets contain excellent examples of what attack behavior looks like in the real world.
Identifying the data is the first significant step in the process. If you don’t have good data already established, consider using the datasets referred to earlier in this article. If you do have good data already in your SIEM, there are some excellent resources available that can help your filter and sort the data to find relevant events.
Cyber Analytics Repository (CAR) is a free tool from MITRE.
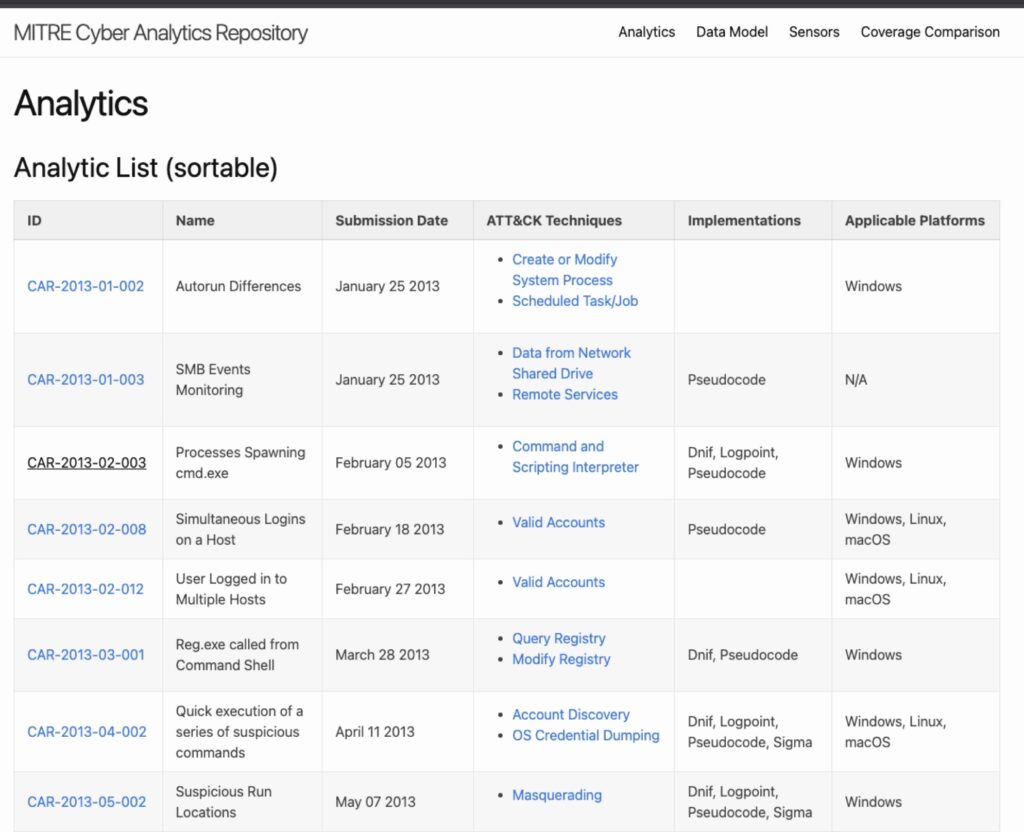
CAR provides pseudocode for many of the threats and techniques in the MITRE ATT&CK framework. The pseudocode is a search filter that locates attack behaviors in your datasets.
MITRE CAR also includes some pre-converted pseudocode for several other tools, for example Splunk, EQL, and DNIF. If CAR can’t produce the pseudocode you need to query for these events in your environment, there are a few other tools that may help:
Uncoder.io
Unicoder.io is a free web-based rule converter that supports bi-directional translation of rule logic between many different SIEM tools. It allows the input of pseudocode, detection logic, and searches from huge list of detection languages, and converts this logic to be supported by the tool of your choice.
It’s invaluable for developing rules to help search your data for some of these behaviors. Very often you can take the pseudocode directly from CAR and convert it using this resource.
SIGMA
SIGMA is another resource similar to Unicoder.io that lets you convert pseudocode and run searches on a command line for a variety of other tools. It may require additional effort to use, but can be very powerful once learned.
Emulate the Adversary
All previous steps have been an effort to train and tool up for the final round of this war strategy, which is to emulate the adversary and ensure that the rules newly in-place are actually effective. It’s time to work with our teams and put this newly-obtained knowledge of our enemy to the test.
Red Team
Blue Team
Purple Team
Merge your Blue Team (Defensive Team) and Red Teams (Pen Testing Team) together into a purple team to ensure that while your Red Team is running “attacks”, your Blue Team is checking to see that the data is both logged and captured, that rules are tuned properly, and you can pull together the data that you anticipated in a sample investigation.
There are several popular tools available for testing:
Attack Simulation
There are several attack simulation tools available, some of which execute commands that can lead to the creation of logs. Some are there to detect config drift and testing your defense without actually producing data.
Make sure that the tool you use produces log data so that it’s captured, and your searches can also capture that information.
Atomic Red Team
Atomic Red Team is an invaluable tool. It’s on GitHub and available for anyone to use. It’s a repository of executables that run these types of behaviors in your environment.
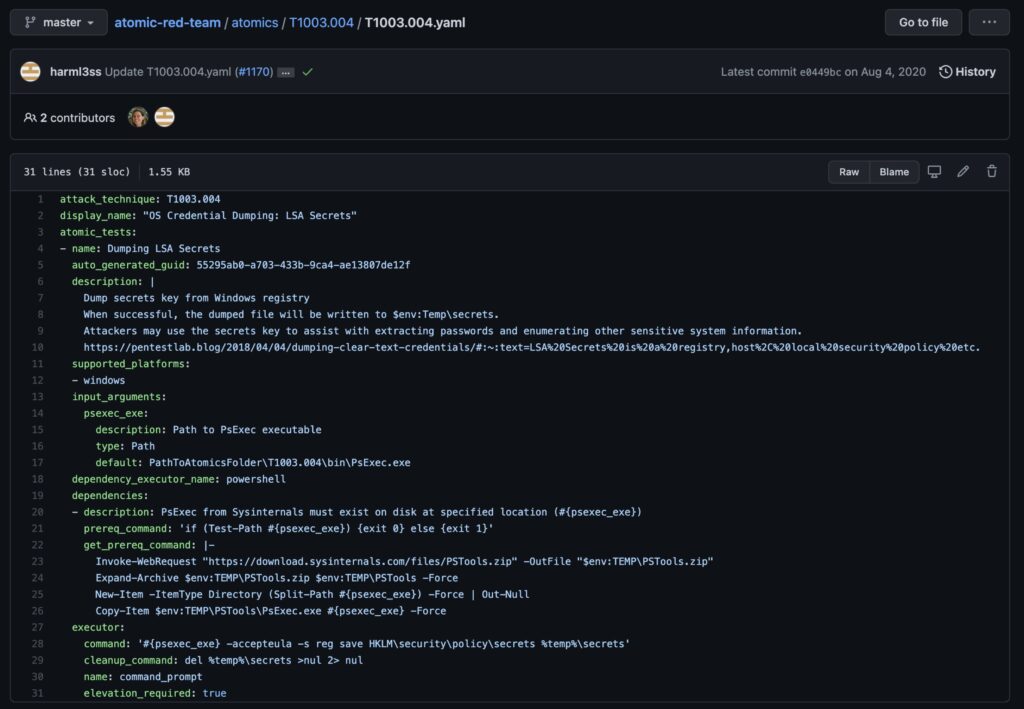
Each executable is detailed, explaining what it does, and allows your team to choose only the ones they’re comfortable with running.
Viewable Logs Post-Execution
You can run all of the executables to produce the data that you are looking to capture. After running each one, you’ll find viewable logs that your searches can capture. This is another method of ensuring your detection logic is working effectively.
When running these executables on a Windows endpoint it’s important to verify the Windows event log is collecting the data before checking if your SIEM is getting it. So, first check there, then the SIEM.
Implementing MITRE ATT&CK
As you work through putting your detection logic in place, you should be filling in your MITRE ATT&CK Navigator with additional scoring.
The end result will be a visualized framework that tracks your organization’s threat detection coverage and clearly identifies gaps that you may want to focus on filling over time and as your organization matures.



