“Zero Trust is not a solution, it’s a strategy.”
Steve Turner, Forrester Research
The pandemic and the massive shift to remote work accelerated the need for Zero Trust. It forced digital transformation in ways we never anticipated and pushed businesses into a new model capable of securing access that doesn’t rely on a perimeter. Traditional security models were failing and, overall, were no longer effective.
Microsoft began pushing Zero Trust and data-centric security strategies starting in 2018. It has invested billions in its platform for Microsoft 365.
In looking at how to apply Microsoft’s solutions, not just for Zero Trust but also for data-centric security, they’ve made all necessary functionality integral to 365. It makes implementation very simple.
“Nirvana is a well-oiled, well-managed security program where all the data is protected 100% of the time wherever it lives,” according to security engineer Michael Howden during his presentation at the Innovate Cybersecurity Summit in Scottsdale, Arizona this October.
That “nirvana” can nearly be achieved through a Zero Trust and data-centric security strategy utilizing Microsoft 365.
Zero Trust strategy components
What comprises Zero Trust? There are six primary components, all pieces of the puzzle needed to achieve Zero Trust.
It’s important to remember that it’s a gradual process when implementing Zero Trust as a strategy. Success is more likely if a phased roadmap is developed that outlines everything to be included in your Zero Trust strategy.
The basic components are:
- Workloads
- Devices
- People
- Networks
- Analytics
- Orchestration
Zero Trust shifts the perceived role of “security restricting” to “security enabling.”
Why are they important?
Why would your business want to do this? What’s the ultimate goal? More importantly, why spend money on micro-segmentation, attribute-based access control for identities, or EDR?
Zero Trust isn’t about getting rid of passwords, firewalls, or VPNs—the traditional perimeter gatekeepers. Instead, it means protecting data at a granular level and with appropriate context.
When it comes down to it, data is everything. It’s the treasure and the target. But implementing the components for a Zero Trust strategy won’t get the job done alone. It must be complemented by a data-centric security strategy to protect the data. The pieces of the puzzle must come together holistically and cohesively.
Data is the perimeter
This isn’t new; data has been the perimeter since the beginning. While you can apply all the other Zero Trust components, it won’t solve the issue of data leaving the organization due to a lack of persistent controls.
The traditional model of building perimeters around silos isn’t effective anymore. To absolutely protect the data, you must shift to the Data-Centric Security Model.
Identifying which data is essential, along with an effective identity management implementation, is key to effective data access control. Consider:
- Who is accessing the data, and how?
- Where are they? This context is essential.
- What is sensitive data, and what is valuable Data?
Intelligent, continued enforcement based on organizational policies is essential in this area.
Data-centric security components
What is the Data-Centric Security Model?
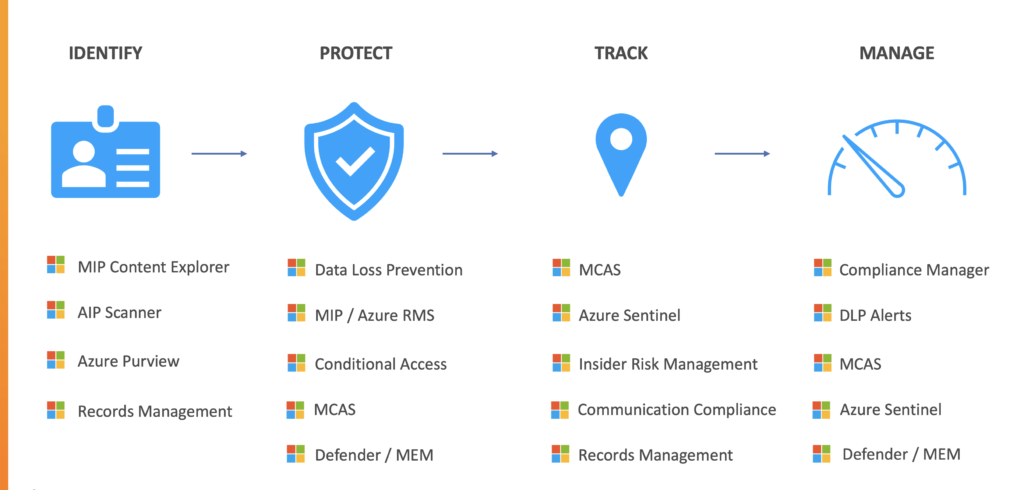
There are four key data-centric security components.
- Identify and know your data
- Protect the Data
- Track the Data
- Manage the Data
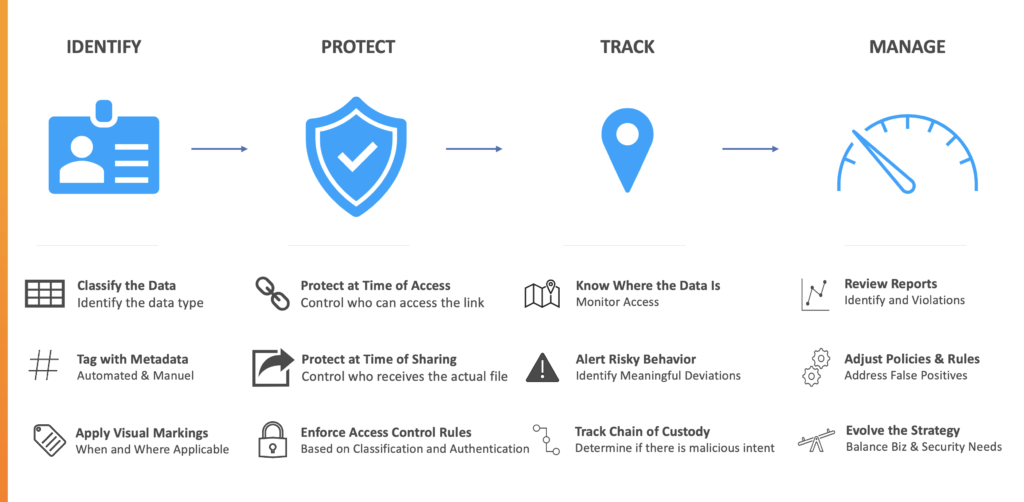
With these components are twelve different actions (per the columns in the above visual), including: classifying the data, protect at time of access, know where the data is, review reports, tag with metadata, protect at time of sharing, alert risky behavior, adjust policies & rules, apply visual markings, enforce access rules, track chain of custody, and evolve the strategy.
The idea is to create a cycle that includes an element of visibility and validation of the result, while iteratively adjusting where needed to make the strategy more balanced and effective.
Microsoft 365 Zero Trust and the data-centric security architecture
At this point it may seem like this strategy is wildly overwhelming to implement. Luckily, Microsoft has already developed the functionality needed for any business to make the transition to Microsoft 365.
Microsoft began its cloud journey 20 years ago, starting with Exchange Online in 2002, then Business Productivity Online Services in 2010, which eventually morphed into Office 365. This course put them on an arc well ahead of other vendors in achieving an integrated and holistic model for data-centric security.
With the advent of Zero Trust as a popular concept, the tools to leverage a data-centric security model are already at your fingertips within the 365 ecosystem.
Implementation
In planning for implementation, a good place to start is by looking at your organizations’s culture and security maturity.
The stage an organization is at can be broken down into three phases: Crawling, Walking, and Running.
Crawling 
At this early stage the most important thing is identifying the data. While you will ultimately Protect, Track, and Manage the data, it’s more important to begin with a classification exercise by tagging data with sensitivity and retention labels and to understand the context you need around that data. Visual markings are unnecessary at this stage.
When you begin to apply some basic protection with Microsoft DLP at the network or endpoint layer, you can track the data, manage it, and review reports in Power Bl or Azure Sentinel. From there, you can determine whether there is additional risk or security awareness training needed to be introduced at the end user level.
An excellent resource provided by Microsoft at this level is Azure Prem. It provides insight into on-prem, hybrid, and SaaS structured data with discovery, classification, and lineage.
Content Explorer will show how existing data matches the SITs in your tenant.
Lastly, the Activity Explorer shows labels being applied or removed to files and emails in the event there are DLP matches, such as: files read, renames, and the location of the emails or files. This label activity is monitored across Exchange, SharePoint, OneDrive, and Endpoint devices.
Walk
At the Walk stage, you have some direction and conviction about the generated data being being labeled and protected. This measure goes beyond protecting the link and access to the container of the files—it is protection on files and emails specifically to encrypt and restrict the data.
More decisions are underway as to where the data can reside:
- Are attachments tracked after they leave the organization?
- How are you measuring and alerting on risky behavior?
- Is DLP and, potentially, Microsoft’s Cloud App Security (CASB) getting enough attention with policy tuning and adjustments?
Risk Management console
Microsoft’s Insider Risk Management console can help with detection, investigation, and action on malicious activity that may be occurring inside the organization.
Within the Insider Risk Management console, there are existing policy templates that can help you get started quickly:
- Data theft by departing users
- General data leaks
- Data leaks by priority users
- Data leaks by disgruntled users
- General security policy violations
- Security violations by departing users
- Security violations by priority users
- Security violations by disgruntled users
You can set up alerts that will let you know if users in your organization are involved in illegal, inappropriate, unauthorized, or unethical behavior and actions. These include leads of sensitive data and data spillage, confidentiality violations, intellectual property (IP) theft, fraud, insider trading, and regulatory compliance violations.
Another insider risk solution in Microsoft 365 is communication compliance. It helps minimize communication risks by assisting in detection, capture, and taking action on inappropriate messages. Pre-defined and custom policies allow scans of internal and external communications for policy matches so designated reviewers can examine them.
Run
The question is not whether your organization can get here, but when. Everyone can get here.
The “Run” phase should incorporate adaptive access rules for accessing data based on classification and authentication, as well as device compliance and user risk. While every organization is different, the options and functionality from Microsoft are there.
How are you tracking and revoking access to data that is being shared internally and externally?
At this point, you should be baselining your compliance strategy using Microsoft’s management components and with specific instructions on technical remediations in your tenant, along with policy and procedural requirements.
In Compliance Manager, everything is available to verify compliance, for running assessments and anything else necessary to satisfy an audit.
Everything can be pulled into Azure Sentinel for free so long as information is not retained for more than 90 days. Basic analytics and asset management without automations are available. Sentinel has more than 100 connectors for native connections, including 10-20 specific to Microsoft and the rest from third party vendors.
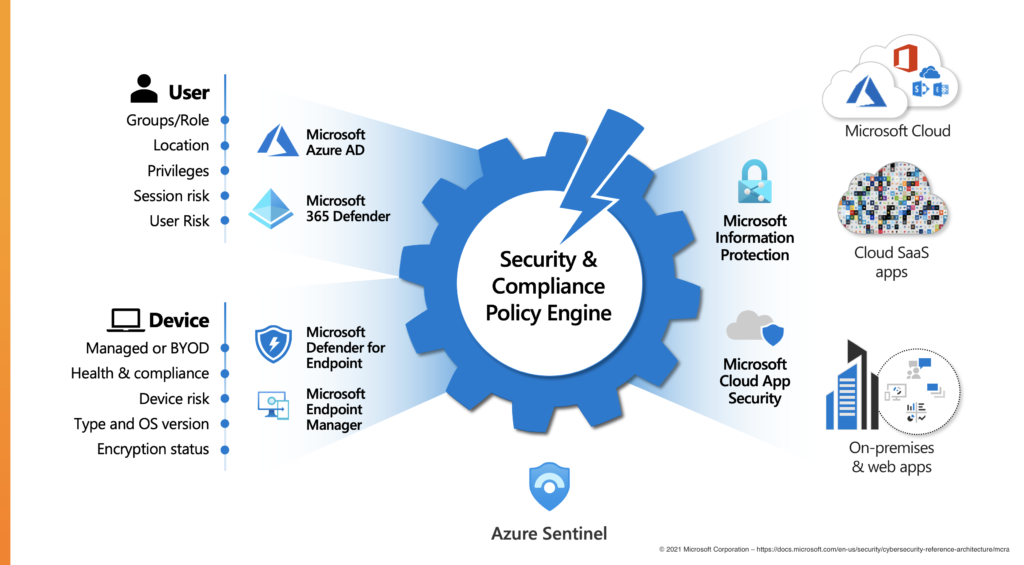
© 2021 Microsoft Corporation – https://docs.microsoft.com/en-us/security/cybersecurity-reference-architecture/mcra
Microsoft security product alignment
Microsoft products all align with the data-centric security strategy and model. There is some overlap, and some products have different levels of implementation, but the tools are proven and available.
Ready?
Ready to implement Microsoft 365 Zero Trust and data-centric security? Here are five practical steps to achieving data-centric security:
- Evaluate maturity— are you still crawling?
- Map a strategy to tools in your Microsoft 365 stack
- Focus on biggest risk points first (e.g. attachments)
- Identify labels and controls
- Pilot, iterate, and mature
While Microsoft builds 100% of the solution, it is essential to design and test the solution that works for your case. Planning and iteration are crucial to success.



