Phishing hasn’t traditionally been a common attack vector in supply chain attacks, but threat actors have continually proven to be extremely adaptive in their methods of attack just as we find ways to mitigate them.
Experts say they see phishing schemes becoming more advanced, sophisticated, and creative during every campaign. AI has even entered the conversation used as tools to craft more effective phishing emails and polymorphic malware automatically, which makes the effort almost trivial. But that’s a topic all on its own.
Recently, Microsoft shared a report on their analysis of a multi-stage AitM attack that security analysts are tracking under the name “Storm-1167″ which appears to target financial organizations. Let’s look at how these attacks work and why they’re a concern.
What is an Adversary-in-the-Middle (AitM) attack?
An Adversary-in-the-Middle attack is an advanced type of hacking where the objective is to intercept authentication. Positioned in the “middle”, between the user and the legitimate authentication service, the attacker attempts to gain the login credentials, forge identity and encryption keys, or co-opt the active auth session.
With any or all of these in hand, they are prepared to mount additional attacks with the goal of financial gain and/or stealing data.
Like many sophisticated attacks against organizations, this one starts with a business email compromise (BEC) phishing campaign. These campaigns seek to take advantage of trust relationships between organizations by chaining the BEC campaigns together.
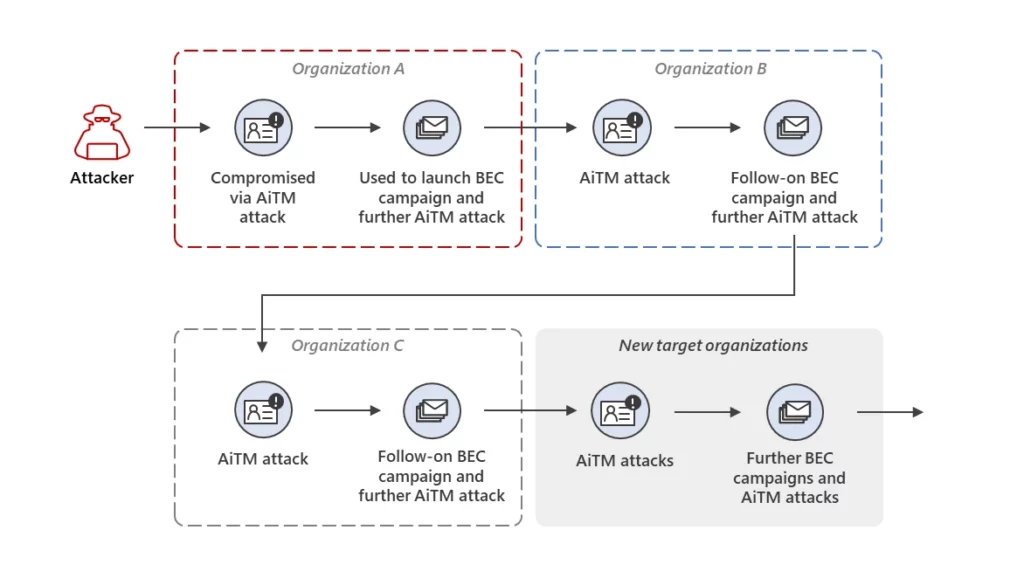
The sequence of the AitM attack documented by Microsoft unfolds like this:
1. Phishing Email From a Trusted Vendor
The user receives an email from a trusted vendor that has a seven-digit code as the subject line, which begins the attack.
According to Microsoft researchers, the email body will contain a link to view or download a fax document. If clicked, the link directs the user to a malicious canva[.]com URL.
2. Malicous Website
Hackers and threat actors typically leverage legitimate brands and services. It helps them avoid detection.
According to the Microsoft report, in the observed attack, the threat actors used the legitimate graphic design platform of Canva where they created and hosted a page that appeared to be a OneDrive document preview and had links to a phishing URL.

3. The AiTM Attack
When the user clicks the URL link, it redirects them to a phishing page hosted on the Tencent cloud platform. The page spoofs a Microsoft sign-in page, but the resulting URL differs for each targeted user, but shows the same spoofed sign-in page.
After the user enters the password on the phishing site, the threat actor uses the credentials in an authentication session which is created on the target site. When prompted with the MFA request, the attacker modifies the phishing page into a forged MFA page. Once multifactor authentication is complete, the attacker captures the session token.
According to Microsoft researchers, the attackers. are hosting the phishing pages for the AiTM attack on IP addresses in Indonesia.
4. Session Cookie Replay Attack
An attacker leverages the valid stolen cookie impersonating the victim in a stolen session cookie replay. It allows them to bypass authentication methods such as MFA and passwords. Microsoft researchers say they saw an attacker masquerading as an attacker by logging in with a stolen cookie from a US-based IP address. While logged in, the attacker was accessing cloud-hosted documents and email conversations. To remain in the environment longer, the attacker also generated a new access token.
5. Changing the MFA Method
Researchers also noted that the attacker then went on to add a new MFA phone-based one-time password (OTP) method to that victim’s account. The added method allowed them to sign in using the stolen credentials of the victim invisibly. By adding a new MFA method in this way, by default the attacker doesn’t need to re-authenticate.
Typically, the researchers saw the attackers adding OneWaySMS, an OTP service, as a new MFA method. Also, according to Microsoft, they saw an Iranian country-coded phone number added as the number to receive the OTP.
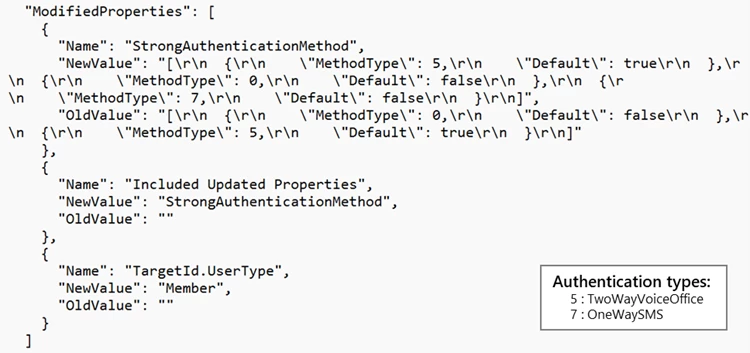
MFA configuration change from cloud application activity logs
6. Creating Inbox Rules
Following this the threat actor used the new session token to sign in and created an Inbox rule with parameters to move all the user’s incoming mails to the Archive folder marking them as read.
7. The Phishing Campaign
The attacker then launches a large-scale phishing campaign, after Inbox rule creation. The phishing campaign involves over 16,000 emails that include a somewhat modified Canva URL.
The phishing campaign’s emails went to internal and external contacts of the compromised user. The recipient list was compiled based on the most recent email threads sitting in the victim’s inbox. As a possible tracking tactic of the attacker, the subject lines of all the emails have unique seven-digit codes.
8. Business Email Compromise (BEC) Tactics
The attacker used typical techniques that kept their activities obscured from the victim’s viewpoint. For example, checking the victim’s inbox for out of office and undelivered emails so they can be deleted from the Archive folder.
Also, the attacker would read responses from recipients who inquired about the authenticity of the phishing email and would falsely confirm the legitimacy of the email. Then they deleted both the responses and emails from the mailbox.
9. Accounts Compromise
Targeted organizational victims of the phishing campaign who clicked the malicious URL were then the target of another AiTM attack. Microsoft Defender Experts could identify compromised users based on sign-in IP patterns and landing IP.
10. Second-stage Business Email Compromise (BEC)
Experts also noted the attackers leveraging the inboxes of users compromised by a second AiTM attack to launch another phishing campaign. To intervene with the second-stage attack, Microsoft revoke the user’s session cookie.
Detecting and Preventing AiTM Attacks
Our Threat Operations say having a robust email security platform, perhaps with AI machine learning capabilities is a good prevention mechanism. Moreso, if it can detect some of the tactics and methods used by the attackers.
Detection is another critical aspect and threat hunters should be looking for suspicious or unknown IP addresses and email rule creation. Analysts should keep eyes on MFA authentication methods, especially where methods are being added. Also, monitor MFA logs for suspicious logins.
Overall, Microsoft did an excellent job in outlining these attacks and its report is very thorough.





