Some organizations have few cybersecurity related polices, while others have tens, or even hundreds of them.
Regardless the number, a common question asked is, “How many policies should we have?”
The follow-up question is usually, “Which do I really have to read and comply with?” The answer is: “all of them.”
Understanding Which Policies Matter
Users are frequently overwhelmed when there are too many policies. The policies currently used by organizations should actually be reclassified as standards or procedures. They do not clearly state why something should be done and why or how the prescribed actions align with organizational goals and objectives.
Security standards documents on the other hand, should clearly articulate what has to be done, to comply with the spirit and letter of the policy statements. Procedure or process documents should also clearly specify how standards statements are implemented in daily operational tasks.
In short, two policies are absolutely essential. Everything else serves as a framework against which policy compliance mandates can be managed and measured.
Actions Affecting Data
What actions should policies address? Overall, only four actions affect data or information, and this happens regardless of the business or function of the organization.
Data can be created, destroyed, modified, or read. In spite of these four simple actions, organizations often improperly protect their data. We see the root cause of these issues as associated with the organizations lack of knowledge about the data they have, where it is, who is permitted to do what with it, how sensitive the information is and, most importantly, how valuable it is to the organization.
This lack of knowledge, or gaps in knowledge, often leads to inappropriate security controls being applied to protect the data. How does this impact cybersecurity policy requirements?
Central Data Policy
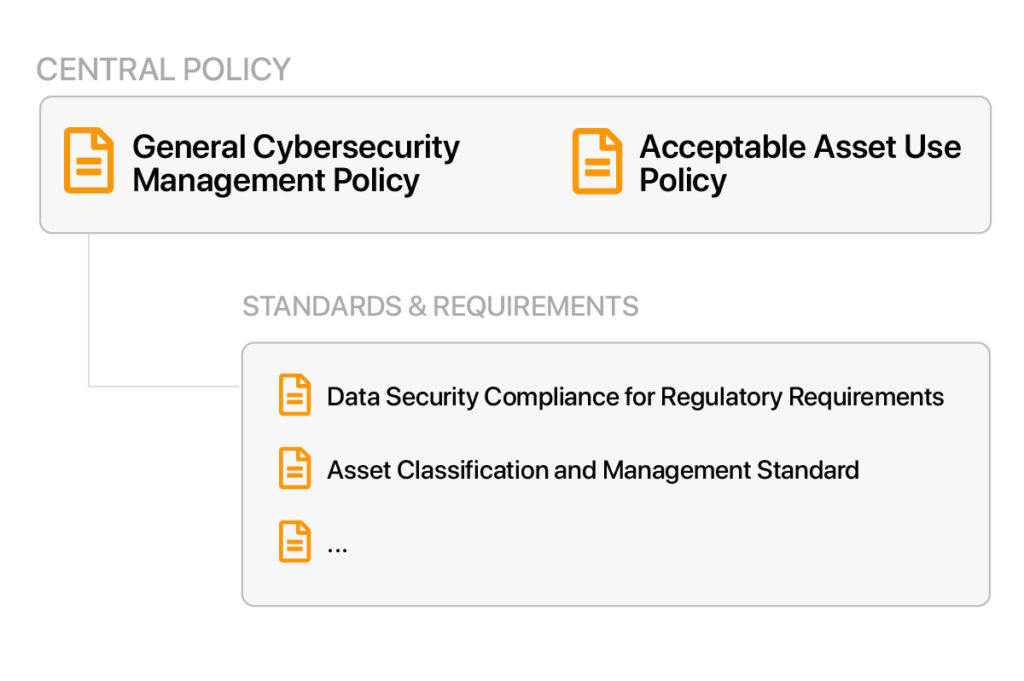
While having too many policies can be overwhelming, there must be a central policy that clearly states why information must be protected, defines what must be protected, and who is responsible for defining that protection. Generally, businesses will then sub-divide the policy into a general cybersecurity management policy and an acceptable asset use policy.
There should also be a policy statement to mandate compliance for the protection of certain kinds of information with regulatory requirements, but it’s usually created as a standard rather than as a policy.
The most oft-forgotten standard is probably an asset classification and management standard. This document is referenced by every other cybersecurity policy, standard or procedure document. It truly is a key security requirements document.
Important to remember is that a cybersecurity policy must articulate the business needs for protecting information. Likewise, cybersecurity standards and procedures define what has to be done and how.
These two policies are the general cybersecurity management policy and acceptable asset use policy. The aforementioned asset classification and management standard effectively drives the need for other documentation to be developed and processes to be implemented. Without this additional documentation and process, the likelihood of maintaining a secure environment where your data and information is appropriately protected is low.
Why Organizations Have Excessive Policies
If we only need two policies, why doesn’t every organization stop there? The answer to this question is often buried in an organization’s history.
Organizations that employ a strong and committed CISO, who is fully backed by the executive committee of the organization, help define these policies so that they support and align with the organization’s goals and objectives.
Implementing Changes
Implementing changes to policies and standards will be challenging. A more detailed explanation or interpretation of a higher-level business driven policy will be one of the biggest hurdles. The issue is often more ingrained within the IT department more so than the users. Usually, the cybersecurity management policy and acceptable asset usage policy are the only policies most users will ever see.
It is rare that users will encounter a cybersecurity standard. These standards are under the purview of the IT and cybersecurity teams. So, accept the challenge, simplify management of policies and reduce confusion.
Adopt two policies and convert most, if not all, of the rest of the existing cybersecurity “policies” into standards, which is what they really are. Successfully implementing a robust policy program will lead to an improved cybersecurity posture based on a very mature cybersecurity management program.
The Author
Mike Tyk is an accomplished Enterprise Security professional with over 30 years of experience in information security consulting. In his current role as Director of Security Services with Novacoast, he assists customers in developing information security management policies and procedures, implementing breach response plans, conducting application threat analyses, and assessing infrastructure vulnerabilities.



