MITRE ATT&CK is the framework that threat hunters, security analysts, and cybersecurity professionals use to catalog the tactics, techniques, and procedures (TTPs) of known threats. ATT&CK contains a wealth of information to aid organizations of all sizes in planning their defense against cyber attacks.
Alex Becerra has developed a method for using MITRE ATT&CK to help with gap analysis and resource prioritization in his role as Director of Threat Operations with Novacoast. At the 2023 Innovate Nashville event, he presented a breakdown of his process which he has dubbed “The Art of ATT&CK.”
What is MITRE ATT&CK?

MITRE ATT&CK is mainly known for the above visual, the relational matrix of categorized TTPs. “ATT&CK” stands for “adversarial tactics, tactics and core common knowledge.” It is a framework that provides information about malware, threats, and threat actors, accumulated via real-world observation. It breaks down into three ecosystems:
- Enterprise
- Mobile
- Industry Control Systems (ICS)
Enterprise, which is the focus here, is comprised of categories like: operating systems, cloud, network infrastructure, and containers, among others. Across the board, MITRE contains 14 tactics and 594 techniques and sub-techniques.
The introduction of sub-techniques a few years ago expanded technique identifiers substantially.
The tactics describe why a threat actor is doing what they are doing, while the techniques describe the how. Specifically, how is a threat actor carrying out a tactic?
MITRE ATT&CK also contains information on mitigations, threat groups, and different software you can use.
Why use MITRE ATT&CK?
When you start looking at MITRE ATT&CK, the looming question is why to use it, and that leads us to take a deeper look at it overall.
- MITRE ATT&CK has over 400 contributors – anyone using it can ride on the back of these amazing threat researchers. You can rely on the integrity of the information you find on MITRE because of this.
- MITRE ATT&CK is based on TTPs, not IOCs – you’re not out in the field playing whack-a-mole because you’re looking at behaviors.
- Vendors are far more forthcoming about their products’ uses, even though they still aren’t revealing their secret sauce. They will tell you what techniques their products can detect.
When talking to vendors, it’s great to ask them upfront what MITRE techniques their product can detect, rather than just sending your logs and hoping they’re doing the right things.
Some customers have the capability to filter by MITRE technique built in as a drop-down in their dashboard. We see this as an affirmation that more vendors in the space are aligning with MITRE.
What is the 2nd Concern?
While there is a lot of great content in MITRE, there isn’t a “how-to” that explains the best way to leverage it for your environment.
When you begin researching, you’ll quickly find yourself drowning in a sea of knowledge. It’s good, but at that point, it’s too much.
We see many struggling with this. They love the information, but making it work for their environment is a huge challenge. Even if you take a step back for a few months, MITRE is continually changing. So, how do you make it work?
The MITRE ATT&CK framework requires some creativity. When you are looking at the navigator, its purpose is not to cover all the possible tactics and techniques. The MITRE navigator is meant to be used as a creative tool, to mold it to your environment, and your use cases, and have the creativity work for your environment.
ATT&CK Mapping Methodology
What is the most effective way to leverage the MITRE ATT&CK framework?
How can you think about mapping in a meaningful way?
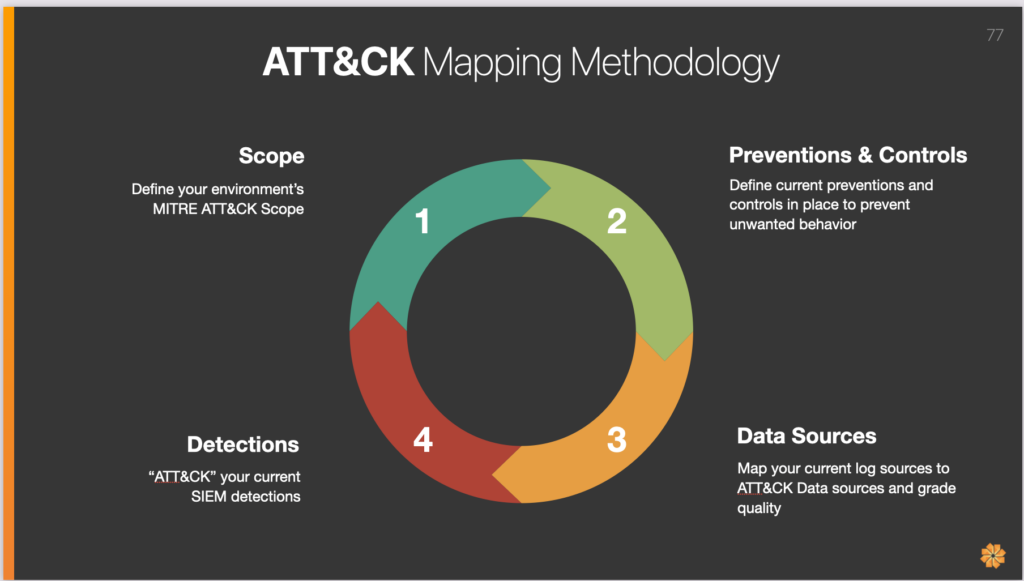
Establishing a MITRE ATT&CK methodology breaks down into these four stages:
1. Scope
When scoping out your environment you want to determine what’s relevant and what you own. At depth, there are a few things to focus on. For example, the ecosystem you’re using.
Next, you’ll select the platforms in your environment. Are you a Windows shop or iOS? This is an important step to ensure results will apply to your environment.
2. Preventions & Controls
Determine which potential mitigations are already live in your environment. Before you begin to evaluate your data, an excellent first step is to evaluate your current preventions and controls. For example:
- Antivirus
- Active Directory Configuration
- USB Control
These are essential things to know because they map directly to mitigation pages on the MITRE site. Of these, antivirus is typically the most common. Most customers will either have antivirus or EDR, but they’re only ingesting the alerts in their SIEM and not all the raw data.
These are significant things to consider – know your preventions and controls and how they relate to your Data Sources.
3. Data Sources
Another mapping method is to look at your data sources. This chart shows the total techniques by the 109 data sources included in MITRE ATT&CK.
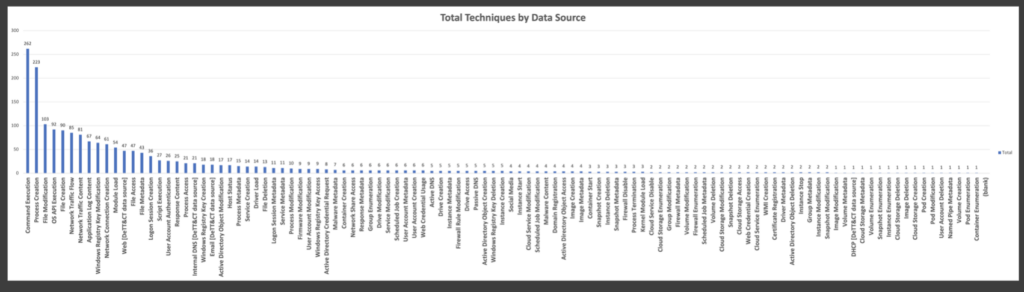
You may note that many of the techniques are ones and twos, but as you near the top, you’ll find command execution and process creation typically top the list. While the purpose is not to have detection and prevention against every technique it’s critical to have endpoint data and monitor what’s going on there.
Ingesting logs that look at Command Execution and Process Creation. Over 50% of all the techniques come from these.
Data Sources – Visibility & Quality
While MITRE provides a massive amount of information on data sources, they don’t provide information on a mapping methodology. The MITRE navigator is an excellent tool, but there is no program and very little guidance around it. It’s changing through the efforts of a number of people working in the space.
One tool that we’ve found is called DETT&CT, which is available on GitHub. It’s an excellent mapping tool that lets you create heat maps on different things. For example, you can have data quality and data visibility heat maps.

A heat map covering data visibility would answer the question of do I own this and show clearly what areas are left vulnerable because you don’t own a product that covers them.
Another heat map you can make analyzes data quality. It looks at the data you’re collecting, such as event logs, to determine what you might be missing. Another example is in EDR. You may have an EDR solution, but is it deployed across all your environments? A data quality heat map will show if there are any gaps in this.
4. Detections
Evaluate whether current SIEM detections are aligned with ATT&CK techniques or not.
Some SIEMs already do this automatically and detect if there is ATT&CK technique alignment, but if there is in-house content checking, this is critical.
For example, Brute Force is an ATT&CK technique, and while most customers have it, they are likely unaware it is an official MITRE technique. It accounts for coverage of one of the techniques.
Once you’ve audited your detections, you can create heat maps. You can use the heat maps to drive prioritization around what is more relevant in your environment and where you have gaps.
You can also combine your detection heat map and prevention heat map. This lets you see what you’re detecting and preventing—overall, this gives you better visibility.
Final Thoughts
While MITRE ATT&CK is not the complete answer to all security problems, it will help you find your gaps.
Consider that by using ATT&CK you can squeeze your team’s energy, blood, sweat, and tears into creating detections. It also helps gain more authority in directing resources and time toward developing rules.
ATT&CK can illuminate the path forward, establishing a road map that is relevant for your environment.
By using ATT&CK in this way, we enable ourselves to be more prepared, informed, and have fewer excuses for that worst case scenario.
About The Author
Alex Becerra is the Director of Threat Operations at Novacoast, specializing in Threat Hunting, Managed Detection & Response, Incident Response/Forensics. He is passionate about educating organizations on the use of the MITRE ATT&CK framework and its ability to pinpoint critical security gaps.


