Almost as fast as new vulnerabilities are found, new vendors, technology, and acronyms are created. It can be overwhelming and difficult to untangle.
This article will add some clarity by covering some of the new and old security technology stacks, compare their differences and similarities, and illustrate how vendors are all on a collision course to achieve parity in the race for the market.
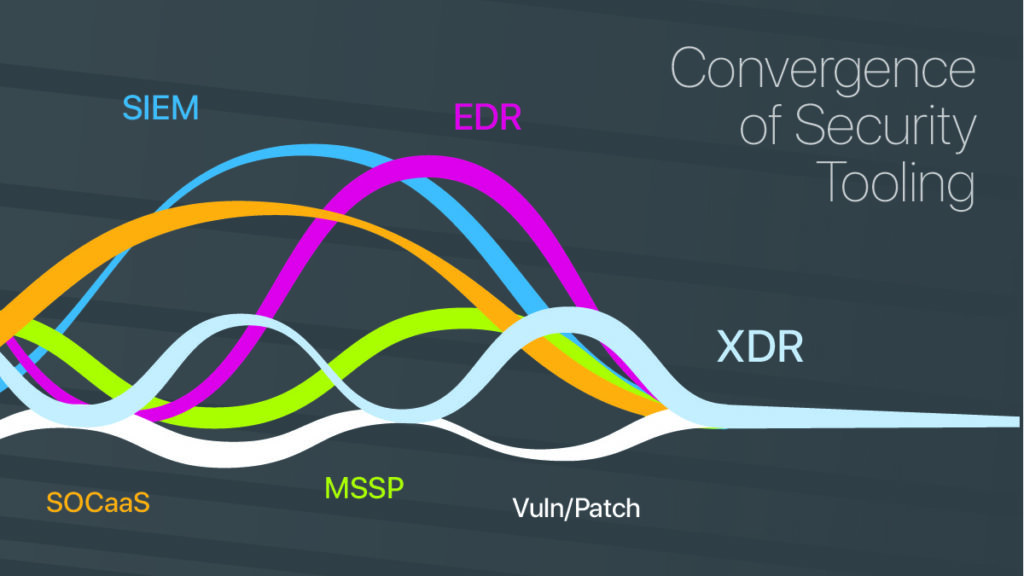
This moment in cybersecurity is messy. We’re at a turning point where the lines between some segments of security tooling are blurred as they blend into a continuum: SIEM, EDR, and MSSP are no longer distinct categories of the market.
Let’s take a closer look at where we started, where we are now, and where we think we’re heading to gain insight into the decisions at hand for security infrastructure in the short term.
Background
The popular toolsets and service structures used in cybersecurity such as SIEM, EDR, XDR, SOCaaS…all have an origin story to explain where they fit in now.
SIEM
The SIEM was developed to collect logs from many data points. The logs get indexed and searched to supply alerts that identify meaningful events in the data.
The history of SIEM isn’t a particularly long one—it was only twenty years ago that the first commercial SIEM products were introduced. Back then it was known as SIM (Security Information Management) and SEM (Security Event Management.) In 2005, Mark Nicolette and Amrit Williams of Gartner coined a new definition, and acronym, of what a SIEM is.
Developers of the first SIEM wanted a tool to help businesses with compliance, and these systems evolved into the threat detection platforms we all depend on today. In looking at how SIEM has evolved over time, we can see that prevailing threats and many other market drivers played a hand.
When Splunk arrived it was an IT log collection platform. After trying to make a transactional dashboard, the company leaned into what potential customers were actually excited about: its ability to search large log data sets. This was before the company productized its current security use case.
Numerous SIEM vendors have come to market that fall into one or more of a few buckets:
- Cloud native
- On prem
- Adopted from an existing product that already does log collection at scale
- Created purpose built for security use cases
EDR
Endpoint Detection and Response, or EDR, started as a tool to collect endpoint data that goes beyond just logs. EDR gave birth to Threat Hunting, which is the science of searching EDR data for evidence of bad actors in hiding.
MDR is simply a managed service for EDR, where an analyst tunes the EDR tooling for a specific environment and use case, provides human eyes for alerting, and performs the threat hunting.
SIEM vs EDR
Although organizations do need both a SIEM and an EDR for unique purposes, the tools are fundamentally doing something very similar:
- Collecting a continuous stream of data
- Indexing the data
- Providing end-users search capability
- Providing end-users a way to alert on events that occur in the data.
It Gets Messy
Although XDR is not new, it’s still loosely defined, and varies. It’s basically the XDR vendor’s whimsical definition of the three letters that make up what data they collect, with the same purpose.
Under the brand of XDR, EDR, and SIEM, vendors are starting to cross over into each others’ respective space and collect the same data alongside other XDR products which definitely collect the same data sets. It can be redundant.
There appears to be an arms race among cybersecurity vendors who want to be the go-to hub of data collection. It makes sense that whoever can collect the data most efficiently will supply the most value.
On the Service Front
An MSSP is no longer just a SOC that looks at SIEM alerts. It might be providing MDR services, or it could be a SOC monitoring several data-fed toolsets. Traditional MSSP structures have changed, from the original model that Gartner defined as monitoring ingress-egress traffic, to something now much broader and undefinable.
If you browse the annual MSSP Alert 250, large swaths of these entities do not even remotely perform the same function. Yet, they’re all fitting under the same umbrella of “MSSP.”
The EDR Vendors
It seems that in this space, each vendor packages their offering differently from all the rest, which makes vendor comparisons impossible. And how effective are they, really? Most EPP and EDR products are underperforming.
SOC-as-a-Service Vendors
The recent category of SOC-as-a-Service vendors may do all the above, or parts of it, and include the software. This is a very promising new space as it maximizes the core service aspect of a SOC while minimizing the overhead and initial customer investment.
Vulnerability Management Vendors
Many vendors of VM tools use the same techniques as EDR and XDR vendors to collect data. They scan the data, find the vulnerabilities, and remediate. It’s likely these vendors will continue to collide more in their scope rather than less.
SOC-as-a Service vendors have picked up on this critical function quickly and provided VM as a core feature early on.
Doing vulnerability hunts instead of threat hunts with EDR tools has been happening for a while. We saw a lot of this during the recent log4j/log4shell crisis that saw many organizations clambering for visibility of log4j instances in their environment.
Where Are We Going? A Few Takeaways:
As the market shifts in a time of flux, consider which products represent an appropriate solution stack for your requirements. With the lines blurred among solutions, and the market slowly achieving an equilibrium in feature set, one vendor may cover all your use cases, or it may take more. While it sometimes seems they’re all gravitating toward the same thing, it may not be true for every use case.
Consider these floating criteria:
- Who collects not just the most data, but the right data?
- Who does the best job supplying a complete and up-to-date-in-real-time set of correlated content? Actionable information like alarms, alerts, etc.?
- Who can do it in the most cost-effective way?
From this perspective, look past the noise of sales and marketing or arbitrary product differentiation. Determine an appropriate mix of actual features from whichever SIEM, EDR, and MSSP is under consideration to minimize redundancy and maximize effectiveness. The gaps in between get narrower every day.





