The Internet Archive was just starting to recover from the October 9 breach when it was hit with a subsequent DDoS attack, taking it offline once again. Let’s take a look at what happened and why.
The DDoS Database Breach
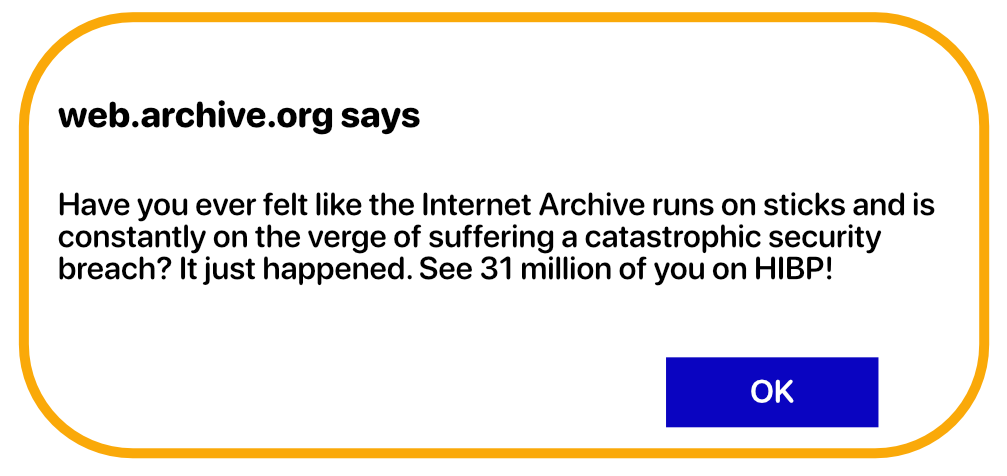
On October 9th, visitors to the Internet Archive (IA) were greeted with a JavaScript alert left by the hacker that shared the news that it had been hit by a data breach. It reads, “Have you ever felt like the Internet Archive runs on sticks and is constantly on the verge of suffering a catastrophic security breach? It just happened. See 31 million of you on HIBP!”
The HIBP the hackers are referring to is the Have I Been Pwned breach notification server. Threat actors frequently share their stolen data with the site.
The first attack was the result of a DDoS attack, which let the hackers steal a 6.4 GB SQL file off of the Wayback Machine servers. The file allegedly contained 31 million singular user data records.
Following this, the organization confirmed the attack and that it was a DDoS that took both archive[.]org and openlibrary[.]org offline.
Founder Brester Kahle shared a few updates on X detailing how the threat actor used a JavaScript library in the attack that showed alerts to website visitors. They attacked the sites with DDoS attacks a few times before the organization disabled its JS Library, cleaned its systems, and upgraded security.
The Second Breach: API Keys Left Vulnerable
All the new protections were still not enough. The attackers returned to attack again just when the Internet Archive announced it was restoring its systems to normal.
The cybercriminals were able to access the site through API keys that weren’t rotated following the first attack and were therefore vulnerable. People who had requested their data be removed from the Internet Archive received replies stating that the organization was once again breached due to stolen authentication tokens that were not correctly rotated.
An email from the cybercriminals said, “It’s dispiriting to see that even after being made aware of the breach weeks ago, IA has still not done the due diligence of rotating many of the API keys that were exposed in their Gitlab secrets.”
This includes a Zendesk token with access to 800K+ support tickets sent to info@archive.org since 2018, as the message demonstrates. Additionally, the email headers all passed the DKIM, SPF, and DMARC authentication checks that confirmed a Zendesk server with the IP 192.161.151.10 sent the emails.
According to Bleeping Computer, it had reached out to the Internet Archive to alert them that their source was stolen through a GitLab authentication token which was publicly available online for at least two years.
“Whether you were trying to ask a general question, or requesting the removal of your site from the Wayback Machine your data is now in the hands of some random guy. If not me, it’d be someone else.“
It’s not clear whether the hacker had serious malicious intent or wanted to prove the point that those managing the Internet Archive need to improve their cybersecurity practices to ensure threat actors can’t breach it.
Rotating authentication keys is a critical component of good security. When keys aren’t rotated, it creates longer lifespans for them, which expands opportunities for threat actors to steal and abuse them.
Zendesk and the Internet Archive
The hacker informed several online media outlets that it still had access to parts of the Internet Archive’s systems. Zendesk confirmed much of what the hacker said while clarifying that nothing pointed to it being a Zendesk related issue.
Subsequently, Zendesk stepped in to assist the Internet Archive in remediating the problem.
Zendesk noted several security failures by the Internet Archive, including not rotating its authentication tokens, which led to the unauthorized access to its Zendesk instance.
The Archive Comes Back
Yes, the Internet Archive is back. For now, it’s only read-only. This means users can search its 916 billion web pages archived over time, but uploading or capturing an existing page into it is on hold while the Internet Archive continues to restore services.
When the Internet Archive is ready, it will resume full access with close monitoring, and may require further maintenance, during which full access will again be suspended.
Best Security Practices
Good cyber hygiene is critical for organizations that want to keep information private and secure. Adoption of security best practices such as rotating personal groups, project access tokens, and using a key management server for storing secrets security is critical.


