Key Points:
- Cyber insurance covers the costs incurred from ransomware loss, data breach, customer lawsuits
- Increasing risk is causing underwriters to scrutinize policyholders’ cyber hygiene
- Be prepared to meet requirements to qualify for coverage. See below for details.
With attacks and breaches on the rise every year, specialty cyber insurance underwriters are being forced into an actuarial risk management position. They are requiring providers to scrutinize the companies they will cover, the extent of coverage, and increase the requirements policy holders must fulfill to get and renew coverage.
Cybercriminals have taken a run on the COVID-19 crisis; state-sponsored cybercrime is being committed at unprecedented levels. There seems to be no end in sight, and the related costs continue to increase.
The number of ransomware attacks has steadily increased every year. According to current data, cybercrime increased approximately 70% from 2019 to 2021 in the US.
Damages from all types of cyberattacks total ~$6 trillion. Most victim companies only survived by virtue of cyber insurance. And with insurance companies starting to bend under the weight of claims, they have begun seeking ways to exert some control on the risk.
Ransomware Attacks Are A Major Motivator
Although the first ransomware attack on record was in 1989, the frequency and severity of attacks have skyrocketed over the last two years. They continue to wreak havoc on companies, costing hundreds of millions of dollars between paying the ransom and recovery efforts.
Ransomware is the primary driver for an organization seeking cyber insurance, as it’s the type of attack that directly results in tangible losses, whether critical data, lost revenue due to downtime, or legal penalties incurred.
Until now, many insurance providers covered the ransom payment and recovery costs, either partially or in full. This is leading some insurers to demand changes from their customers and define limits on what is covered.
Cyber Liability Insurance
Necessitated by the unthinkable costs of a cyberattack, organizations are turning to a somewhat new branch of insurance birthed from a very modern threat. The liability to an organization who loses customer data in a breach can be significant, as class action lawsuits will seek sizable sums to compensate for increasing exposure to identity theft.
Policies typically cover all the costs related to a security breach, such as investigating and documenting the attack, hardware repairs and data recovery, notifying regulatory bodies and customers, PR damage control, crisis management, and more.
Why is Cyber Insurance Important?
There are several reasons that make it a very pragmatic decision to cover your cyber risk with an insurance policy. Some of these include:
- Cyber incidents, directly and indirectly, affect businesses
- Recovery from an attack is costly
- Ransomware costs are huge
- Customers assign their risk to you
Downtime in the modern era has considerable costs associated—many services and processes come to a halt if computer systems aren’t up and running. This is the consequence every business will deal with after a serious cyberattack.
Cyber Insurance Claims
What exactly does cyber insurance cover? It typically breaks down into these four categories:
1 Data Loss (Customer & Employee)
Sensitive data is frequently the target of cybercrime. This data includes personal identifying information (PII) that can be compromised or lost even when a data breach wasn’t committed with criminal intent. These areas of coverage include:
- Identity recovery solutions
- Expenses related to crisis management
- Loss of income and wages
- Regulatory penalties and fines
- Mental health counseling for customers or staff
- Forensic investigations
- Expenses related to public relations
2 Business Extortion and Interruption
This category refers to ransomware attacks that lead to extensive downtime while access to systems is repaired and restored . These can include significant payments to the criminals, and coverage under this category typically includes:
- Ransom payments
- Data restoration and recreation
- Business loss and fallback plan
- System failure recovery
- Forensic accounting solutions
3 Payment Fraud
Payment fraud is when cyber criminals trick employees into sending money directly to fraudulent accounts or sharing sensitive information. This can also involve hacking into systems where criminals either install malware or steal funds. The purpose of this coverage category is to help with managing telecommunications providers and recovering lost funds.
First-party coverage in this category includes support for expenses related to three major events:
- Telecommunications fraud
- Computer fraud
- Misdirected payment fraud
4 Third Party Liability
Third party coverage is for liability which includes expenses incurred from lawsuits. Examples:
- Trademark and copyright infringement
- Network security liability
- Electronic media liability
- Unintended defamation
- Violations of privacy rights
Support for public relations expenses is often also included in cybersecurity insurance policies to assist businesses in managing media coverage in an effort to preserve or restore the company’s reputation and broadly inform those affected.
Costs of Cyber Insurance Claims
How do a cyber insurance claims breakdown by the numbers?
Costs of Claims
The chart below a depicts a distribution of costs incurred by a cross section of attack targets, where percentage of total claims was weighted at $50,000 or less. For total costs, the higher value claims ($5M or more) dominate the distribution.
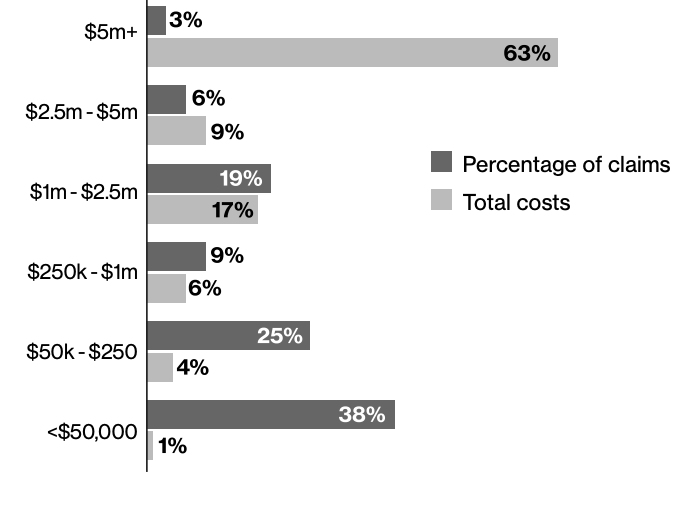
Costs of Claims by Type
Cost of attacks are substantial, and insurance underwriters want to see that every business they insure is preventatively doing all it can to defend against attacks before they will grant a policy.
Advisory firm Marsh has identified 12 requisite security hygiene controls that underwriters will look at when deciding if a business is insurable.
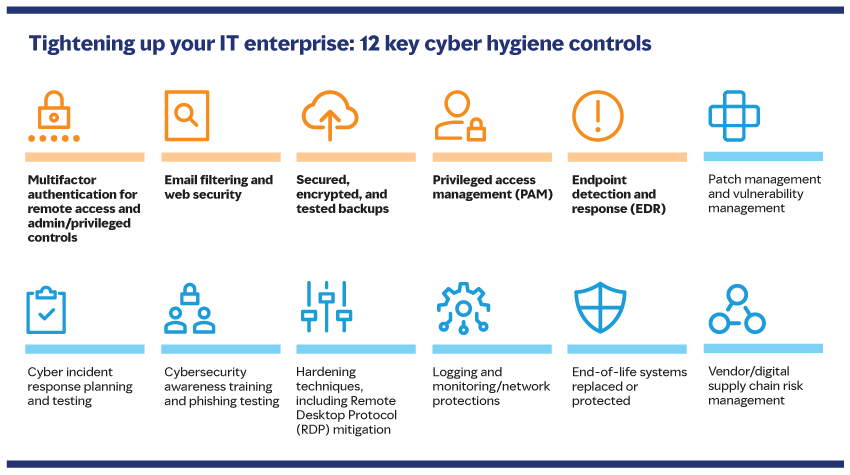
Meeting Insurance Requirements
Insurance is a business, and its profits are a simple equation. It comes down to this: Premiums – Claims = Profit.
Cyber insurance isn’t a new business model; it’s still insurance, the only difference is the type of risk it covers. Compare it to other high-risk insurance types such as flood, earthquake, and auto insurance.
In the current risk climate, insurers know that it’s no longer a question of whether a company will face a cyberattack but when. Good cyber hygiene is no longer a suggestion but a minimum requirement of insurers that underwriters look at when determining insurability.
Businesses with solid cybersecurity programs are already emphasizing controls to mitigate ransomware risks and boost resilience and cybersecurity positioning.
Risk profiles and cyber hygiene are now a large part of what makes a company a good fit for insurability, and insurers have set these as new requirements:
1 Multifactor Authentication (MFA)
MFA is a hygiene control critical for remote access users and accounts with admin or escalated privileges. Passwords – even the so-called strong ones – can longer hold up to modern attacks. Vulnerabilities can occur when users reuse the same passwords on multiple sites.
Using MFA helps businesses boost their security since it requires at least two ways to verify the user’s identity. Typically, the factors are something they know and something they have: A short-lived code delivered through an authentication app or mobile device that expires in less than a minute and the user’s password.
Cybersecurity tools are not infallible, but MFA has been proven an excellent barrier and deterrent against unauthorized access.
2 Email Filtering
Received email represents a very large attack vector. Emails crafted to phish account owners are one of the most effective opening attacks in play today. By using email filtering, businesses are able to identify messages that have attachments or links, and some systems will scan them for potentially malicious content or malware.
3 Backups
With ransomware continuing to increase, it has made most businesses aware of the critical need for a robust strategy when it comes to backups, specifically for vital data. A few recommendations:
- Backups should be encrypted
- Incremental backup intervals should be based on data changes with periodic full backups
- Administrators should logically separate backups from the network
- IT should set a data restoration testing schedule to ensure backups are working properly
- More resilient media, such as magnetic/tape/optical, should be considered for maximum safety.
4 Privileged Access Management (PAM)
Access to administrator or privileged permission accounts should secured by more stringent login credentials and differ from general user access.
Permissions and authorization should be siloed so that only select users such as IT, database, or network administrators should be allowed to do specific things using their privileged access. They should also be required to log out of their accounts to carry out tasks not requiring privileged access.
PAM systems work similarly to a password vault where passwords are never viewed or seen, and access is “checked out” only for the necessary time to perform privileged actions.
5 Endpoint Detection and Response (EDR)
Organizations should keep up-to-date accounting of all devices employees use to access and receive business information, whether desktop, laptop, or mobile device.
EDR monitors these devices and collects essential data about the device such as location, software versions and updates, and if/when the user tries to download or install software.
EDR also aids in incident response via remote wiping or forensics.
Bottom Line: Cyber Hygiene Benefits Everyone
Regardless whether the motivation is to comply with the requirements of an insurance policy or to simply strengthen an existing security posture—implementing a solid cybersecurity program that includes everything above will have far-reaching benefits.
Some things can’t be replaced with an insurance payout, like priceless intellectual property or proprietary research that might lead to unknown marketable profits. Or the trauma of putting a customer though an identity theft crisis that cost them a mortgage qualification mid-escrow. Maintaining good security hygiene benefits everyone in the sphere of an organization.



