In 30 years of IT and hundreds of large enterprise migrations measured in millions of users, it’s still intriguing how bad the security posture of data is for most organizations. The process of discovering and securing the important data, figuring out who is touching that data, and determining whether the data is sensitive or not—it’s a struggle for even top tier outfits.
It hasn’t been very long since files and data resided only in on-premises silos. In a relatively short time, vendors have come to market to address the need for adapting traditional data access, governance, and data classification, to the expanded scope of cloud and hybrid storage models, amongst other categories of data security tooling.
And with the advent of zero-trust methodologies, there is a vast scope for improvement here. Let’s look at some of new developments in data security and the backstory that makes them necessary.
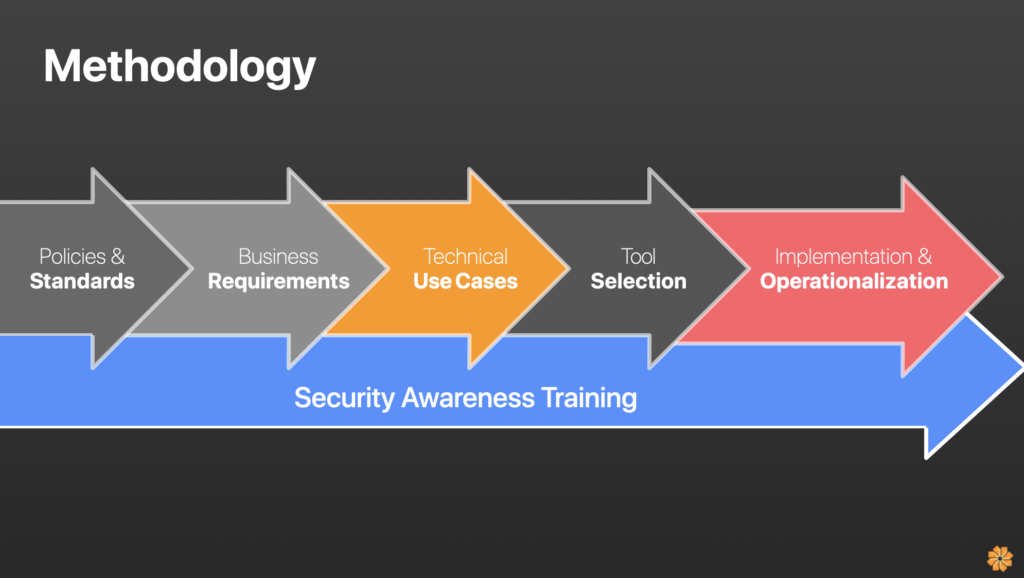
Methodology
It used to be very linear, depending on whether you were doing DLP or classification. Then we started using an iterative approach—starting smaller, picking off a business unit, really digging into getting successful, building out that process, and then iterating back through the different use cases while maintaining communication with people in the organization. Hence, you understand the business requirement side.
It started getting interesting as vendors evolved, and as we looked at data in its lifecycle—when you create it, store it, collaborate—many different things needed to happen.
From a category and data state perspective, this is a typical thing we’ve discussed over the last few years—data governance, classification, and encryption. You must know the structure of the data—is it unstructured or structured? Is it at rest or in motion? And use all these things that are relevant to what’s going on in your organization. Understanding these nuances is critical to comprehending vendors’ go-to-market strategies and functionality.
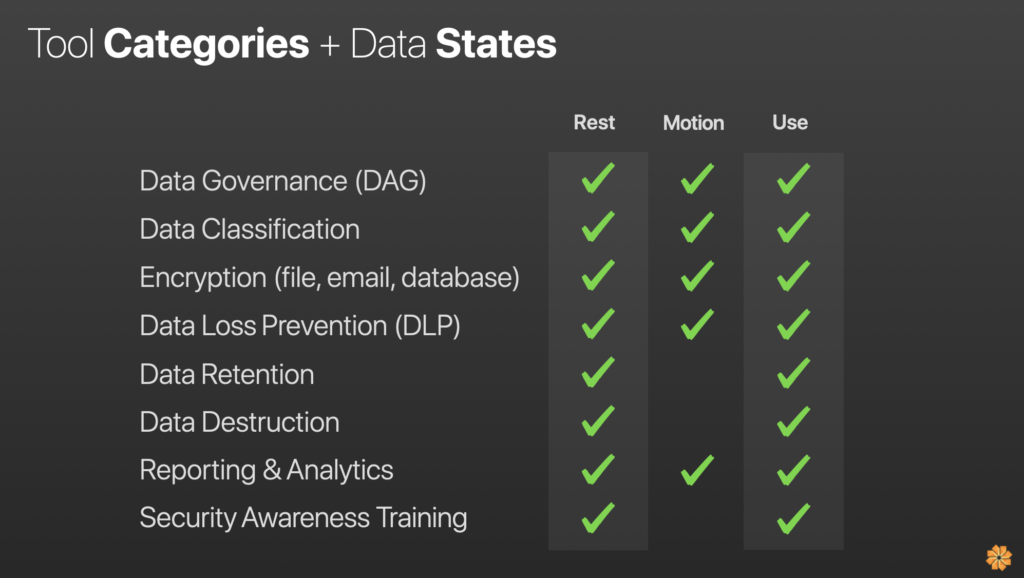
What’s interesting from a vendor count by category perspective is the data governance space got pretty mature. There were probably 25-30 vendors in that area, even though most people can probably only name the top 3.
In data classification, people are still struggling. Is it because of the culture? Are the tools not adequate? It still tends to be a significant issue for many companies.
From another perspective, like DLP with dozens of vendor solutions in this kind of classic category state, it is probably the most mature we’ve seen. It has become commodity, but also doesn’t solve everything an organization requires to protect data inside and outside the company boundaries.
What Are the Pain Points?
In a live poll of CISOs from the audience at the 2022 Innovate Cybersecurity Summit, the results were interesting but not unexpected.
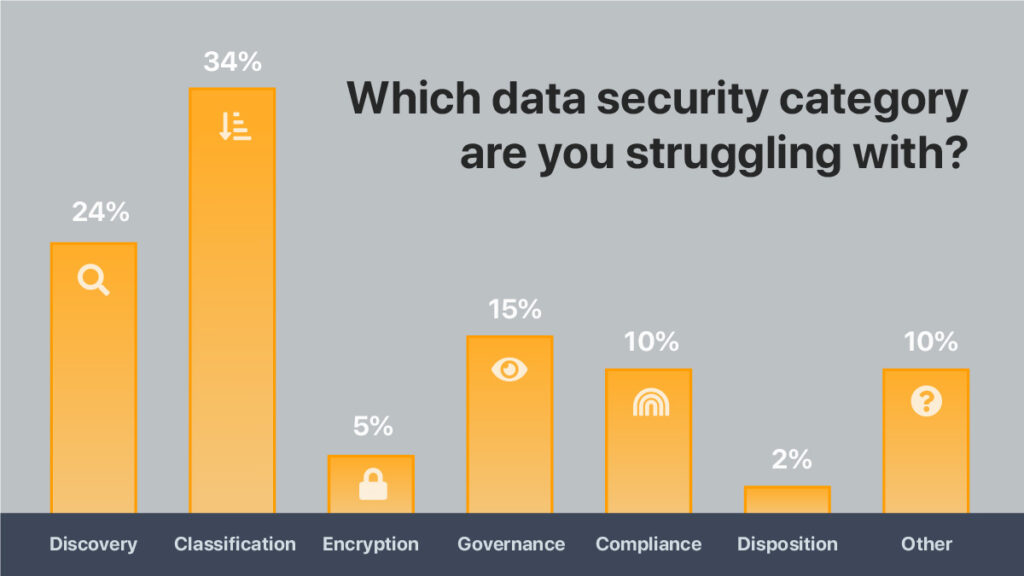
New vendors in this space are spending time on discovery and classification. They’re not necessarily putting metadata on the data itself and tagging that data.
Zero Trust in Data Security
The recent popular methodology of Zero Trust, or securing the perimeter of systems that house the data using a least-privileged model, dovetails well with data security.
But while many people know about zero trust strategies and know data-centric security, most aren’t applying everything in their data privacy and protection programs to ensure appropriate maturity within their existing tools.
New Tool Categories and Data States
As vendors improve through experience with different customers, think back to the original categories—data governance, data encryption, classification, retention, et al. But as the space continues to evolve we have new acronyms to learn based on emerging technologies:
Data Security Platform (DSP)
We’ve seen vendors acquire vendors to bolster their coverage of data security features, ultimately building a platform. We’re nearly at a single pane of glass for all the data security and governance and protections—all bundled as a platform.
There are probably 8-10 DSPs on the market. Microsoft and Proofpoint are the big ones. But DSPs aren’t the best fit for every organization. If you’ve already invested in 15-to-20-point solutions that do very similar things, migrating is a heavy lift. Interestingly, more and more companies are converging, and the movement likely will not slow soon.
Data Security as a Service (DSaaS)
Due to convergence in the data space, more of these vendors are coming to market at a rapid pace. Data Security as a Service (DSaaS) has been quite surprising and is like a DSP. It is a cloud-based service model where you ship all your data up, and they do the transformation.
They do the compliance side and everything necessary to ensure your data is protected, such as format-preserving encryption and data masking. Then you can broker it back to either internal employees or external third parties.
The different offerings have slightly varying approaches; perhaps this will work best for simple use cases.
Key Management as a Service (KSaaS)
This service seems to have been born out of the different cloud providers doing key management independently and not integrating with other cloud providers. Only a handful are in the market, but they are gaining traction to provide universal key management across all platforms. Expect growth in this area and additional integrations via APIs.
Database Activity Monitoring (DAM)
An older category seeing a resurgence is database activity monitoring (DAM). There are a few dozen vendors looking at all the structured data that people generally ignored in the early data governance days.
DAM is monitoring and reviewing how data is being touched—whether it’s Postgres, NoSql, or relational databases—and looking at all the activity in and around the data to provide some form of protection. It’s mainly in the multi-cloud proliferation where this is gaining traction.
Confidential Computing
Here’s one with no acronym; sorry about that. Confidential Computing has also been gaining some traction with highly regulated industries where data encryption is required. Put the data in an enclave and then only allow specific people, even internally, to access that data during compute operations.
Or perhaps that’s how you will keep it from your cloud provider—keeping it encrypted in certain areas and having that trusted execution environment. It’s another exciting thing that is coming up and becoming more relevant.
Data Security Posture Management (DSPM)
This term is interesting; it’s a bit of data access governance 2.0 for the cloud because it asks many of the same questions:
- Who touches my data?
- How do I map users to different datasets?
This one is going to be relevant to all the different silos and structured data repositories in the cloud. It could be Snowflake, S3 buckets, Azure Data Lake, and other similar data stores.
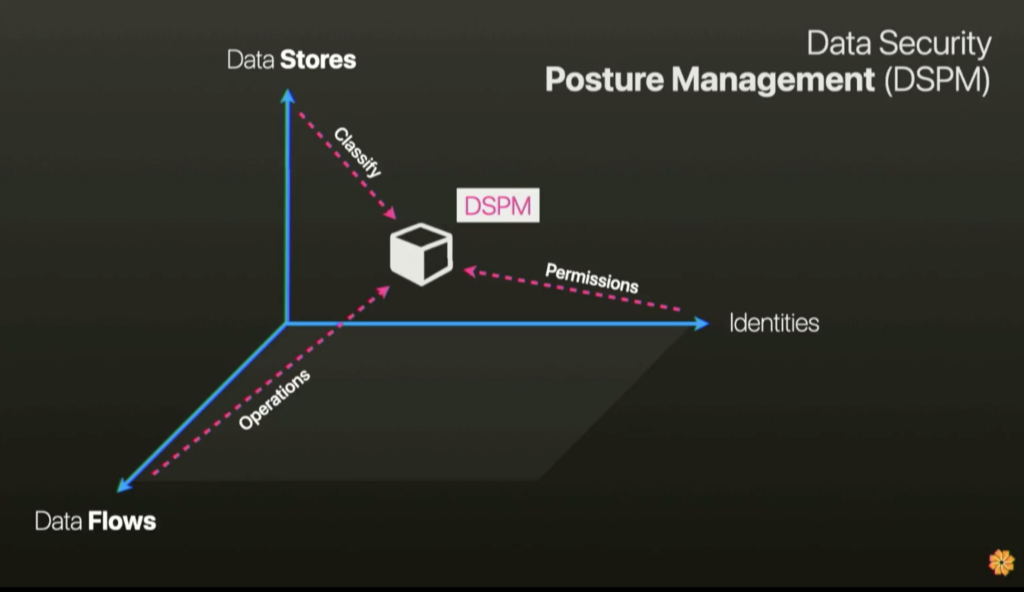
It’s intriguing how DSPM is checks data flows and looks at all the different data stores; it classifies the data, and it’s not really for the sake of classification, but rather so you can understand if you have sensitive or valuable data in a particular bucket or silo.
If sensitive or valuable data is found, it provides guidance on minimizing the level of permissions, potentially looking at it from a risk perspective:
- What is my company doing operationally to contain our sensitive data in the right spots?
- How are we actively trying to remediate potentially like oversharing, extraneous permissions, and other oversights?
DSPM is going to gain the most momentum in the next 1-2 years and become a very crowded space. Watch for early acquisitions and consolidations by bigger companies. Be cautiously optimistic if you’re going to POC or pilot a solution.
Some vendors even say to “reduce the blast radius.” Look at all your applications and data, map how everybody is using it, and look to reduce dormant permissions and apply all the typical hygiene of data governance—that’s where you’d really want to start reducing your risk.
Minimize the effects of getting breached—this is the goal.
A few highlights on DSPM:
- Maps users to sensitive data
- Provides insights and operational visibility
- Maps data flows
- Continuous data risk assessment
- Actionable remediation for oversharing and extraneous permissions
- Detection and alerting anomalies
DSPM will provide constant information about what’s going on in the environment, with a little crossover to User Behavior Analytics (UEBA) because is looks at the visibility of the operations.
DSPM is the one platform to watch this year.
The author
Michael Howden is a Director of Security Services for Novacoast, specializing in data security and DLP solutions. This article was translated from his presentation at the 2022 Innovate Cybersecurity Summit in Scottsdale, AZ.



