On April 19th, MITRE revealed it had discovered foreign threat actors accessing its Networked Experimentation, Research, and Virtualization Environment, known as NERVE. State-sponsored threat actors from China launched the cyberattack in January, leveraging two vulnerabilities found in Ivanti Connect Secure.
MITRE’s President and CEO noted, “No organization is immune from this type of cyberattack, not even one that strives to maintain the highest cybersecurity possible,” while assuring customers and the public of its continued commitment to providing cutting-edge solutions, such as the MITRE ATT&CK Framework.
The CTO of MITRE gave a brief overview of the incident. During this, he highlighted the importance of the cybersecurity sector continuing to develop innovative security solutions. Businesses should be equipped with resources that can combat new threats. These must safeguard businesses and the global community from constantly changing and more intricate threats.
The attack on MITRE has been documented, so let’s explore what happened and cover some methods businesses can use to safeguard themselves.
The Cyberattack
In January of this year, threat actors leveraged two zero-day Ivanti Connect Secure vulnerabilities in MITRE’s VPN infrastructure, bypassing multifactor authentication (MFA) by using remote session hijacking. This provided them with unauthorized access to MITRE’s network. The attackers then used different remote services such as Secure Shell (SSH) and Remote Desktop Protocol (RDP), letting them access a compromised admin account to move laterally across MITRE’s network.
The attackers then leveraged a mix of webshells and backdoors to maintain persistence, collect credentials from MITRE’s network, and dig deep into its VMWare system.
MITRE discovered and mitigated the VPN vulnerability quickly, but the infiltration by the threat actors and the continued lateral movement in its network remained undetected until April. This lapse led to a false sense that all was secure.
The Flow of the Attack
MITRE followed best practices, government advice, and the vendor’s instructions to upgrade, harden, and replace its Ivanti system. All the actions taken still fell short of resolving the vulnerabilities and protecting MITRE’s network from the cybercriminals activities in its network.
The chart below shares the MITRE Techniques, Tactics and Procedures (TTPs) the threat actors used in the attack.
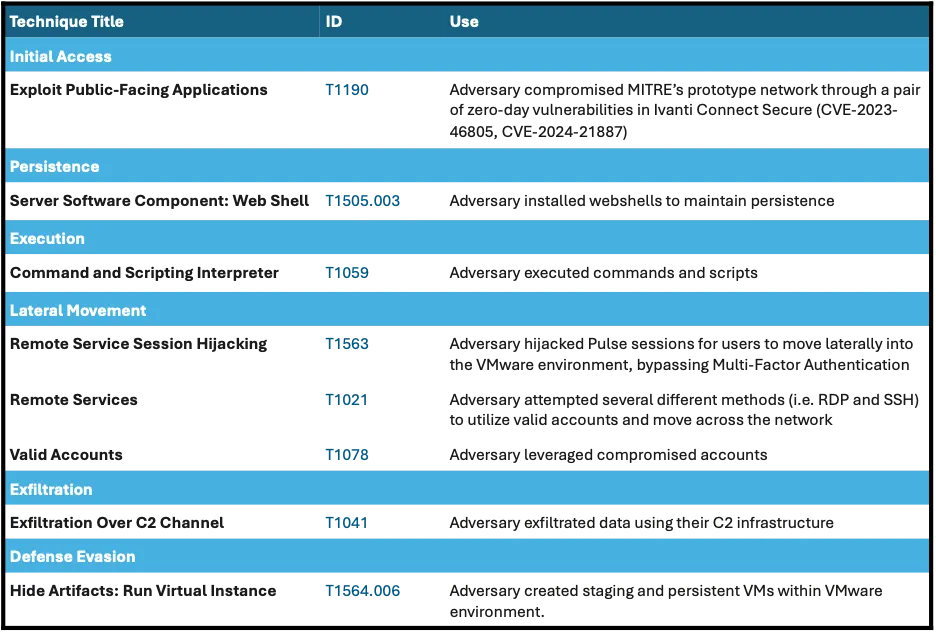
Responding to the Attack
The cybercriminals avoided detection from January until April, bypassing the MFA that protected the system by using remote session hijacking.
MITRE’s incident response team began its response plan immediately after detecting its network was breached. Some of its key steps included:
Containing the Threat
Isolating systems and segments of the network was key to preventing the attack from spreading further. Firewall rule changes proved insufficient since the network was connected to labs across the business. Shutting down access to the infrastructure and isolating edge systems in labs was critical to effectively containing the breach.
Governance Alignment is Critical
While its CTO led MITRE’s response, its board of trustees was actively involved and supported the mission by chartering an ad hoc committee to provide oversight and governance. An aligned board and management team are critical parts of an effective recovery and response.
Analyzing the Attack
Using a multi-stream approach, forensic analysis was a critical component in determining the extent of the compromise. It also helped in identifying the techniques used by the attackers and if the attack was widespread or limited to the prototyping and research network.
MITRE still has a lot to investigate to completely assess how the cyberattackers interacted with its systems. They say trusted log aggregation is the most critical component in their security arsenal when it enables forensic investigation.
Remediating the Compromise
Once the compromised system was isolated and contained so forensic analysis could be conducted, MITRE needed to set up alternative storage, compute and networking resources for its projects to use. Once it identified alternative platforms and performed a full security audit on them, an established procedure was put in place to migrate projects over. Within two weeks, the highest-priority projects were back online in clean environments.
Maintaining Transparent Communication
Maintaining transparent communication with all stakeholders, such as affected customers, employees, law enforcement, and the public, is critical. As the investigation into a breach goes on, finding the right balance of what to share and when is a challenge.
MITRE decided the best course was open transparency with its stakeholders and the public. Throughout its investigation into the attack, it worked to help improve the understanding of the attack and how organizations can combat the threat themselves.
Preparing for the Long Game
Rapid deployment of new sensor suites was necessitated during MITRE’s forensic investigation. Not only did this aid in collecting new information from affected system, but the process also allowed for enhanced monitoring with long term benefits.
MITRE says it could use IOCs from the affected systems, law enforcement agencies, and its partners that will aid threat hunting throughout its network.
Detection Best Practice Tips
As part of its investigation, MITRE released these high-level strategic tips for better detection abilities.
- Anomaly Detection: Monitor VPN traffic for unusual patterns
- Behavior Analysis: Look for deviations in user behavior
- Network Segmentation: Segmenting networks can limit lateral movement
- Threat Intelligence Feeds: Stay updated with threat intelligence feeds
- Adversary Engagement: Deploy adversary engagement resources in your environment
Hardening Your Network
Implementing high-level methods for network hardening should be included in next steps, following these suggestions from MITRE:
Strong Authentication
Implement strong multi-factor authentication mechanisms as part of robust access controls and least privilege principles.
Scheduled Patch Management
Keep all systems and software patched and up-to-date to aid in mitigating vulnerabilities.
Network Segmentation
To limit the impact of a potential breach and contain malicious activity, leverage network segmentation.
Threat Intelligence Program
Stay updated on industry and CISA’s cybersecurity advisories and implement the latest fixes, mitigations and detection techniques.
Least Privilege Access
When user privileges are restricted, it limits abuse of compromised credentials by cyber criminals.
Vulnerability Assessments
To identify and mitigate weaknesses proactivity, organizations should be running security assessments regularly.
There is an ongoing need for vigilance and enhanced security to adapt to and combat new threats in the ever-changing cybersecurity landscape. MITRE is committed to public facing mission to strengthen cybersecurity for the industry.



