Many businesses include a website chatbot. Experts say they help build trust, add a layer of customer service, and increase engagement.
Hackers have paid attention and have devised a new phishing method that includes a chatbot to lure victims into sharing personally identifiable information (PII). Threat actors are now employing convincing legitimate methods such as one-time passwords, Captchas, and in this case, chatbots, making it challenging to identify a fake site attempting to harvest their credentials and other information.
This fake chatbot scam begins with a phishing email that appears to be from a reputable company but includes typical signs of a scam.
The Arrival of the Phishing Email
According to a recent IBM report, human error is the primary contributing cause in 95% of all cyberattacks. A cyber criminal’s typical vector is email, either as a targeted attack or an attack of opportunity. These emails carry compromised files that will install malware or obtain credentials, a technique known as phishing or spearphishing.
Phishing emails often appear to come from a legitimate company or government agency known to the victim. Typical examples include FedEx, DHL, PayPal, Social Security, the IRS, banks, credit card companies, and others. Emails like these prey human nature by exploiting a combination of familiarity and urgency, and are often the precursors of a cyberattack that ultimately compromises business information.
In the current scam scenario, security analysts found emails portrayed as coming from DHL:
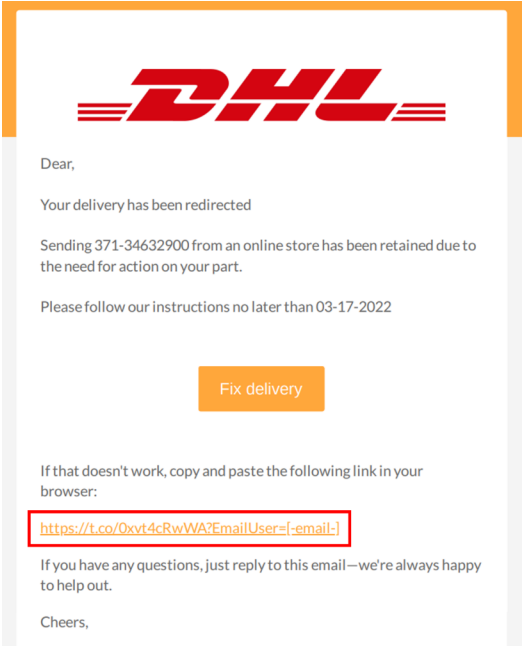
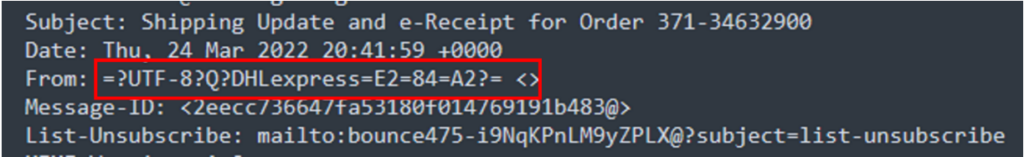
While this email appears to be from DHL, a closer look at the headers show it’s missing a fully formed sender email address—one of several clear indicators.
Should the recipient proceed and click on the “Please follow our instructions” link, a PDF file will be downloaded and likely opened.
This document will direct the targeted recipient to the phishing site in two different ways: the first is by clicking the button “Fix delivery,” and the second is by copying the alternative link contained in the file to a browser tab. No matter which option the user chooses, they will be taken to the phishing website, and the phishing begins there.
The Chatbot-Like Phishing Scam
Once the phishing site is reached, the chatbot-like page appears with a trust-building and friendly appearance.
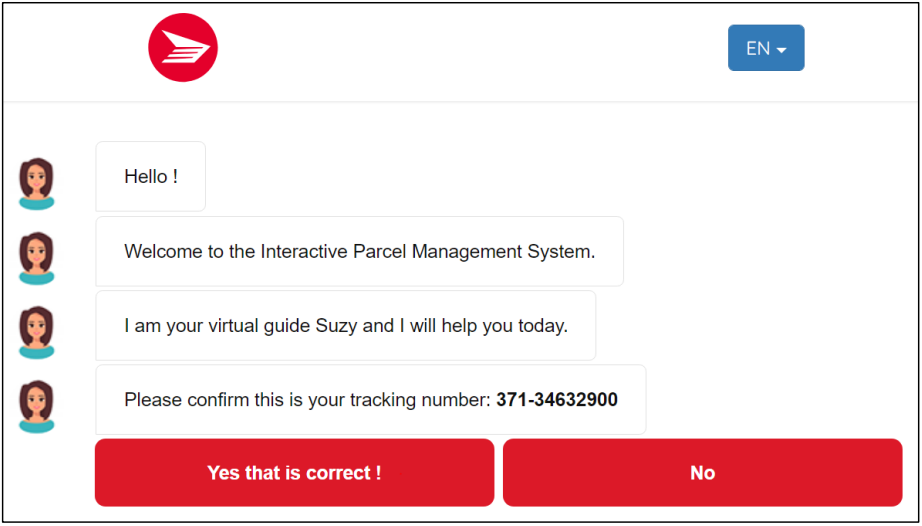
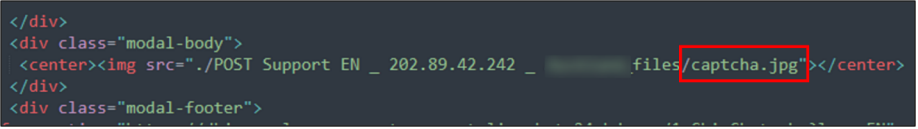
While the page appears to be a legitimate chatbot, it’s not. It’s an application filled with predefined responses that are all based on limited options. The hackers have even included a reCAPTCHA to build trust with the recipient and give them the false belief their input is safe. And that is where it’s a bit odd: most captchas let you refresh or redirect you to the reCAPTCHA site when you click on the reCAPTCHA logo, but the only thing clickable on this one is the “confirm” button. It’s a fake reCAPTCHA made from an embedded image.
Once the victim clicks on the confirm button, they are whisked to a page where the fake “chatbot” collects personally identifiable information, such as the email address, delivery address, and password.
The next step is clicking the “Schedule Delivery and Pay” button, leading the target to a form to collect credit card information. Once the user completes the form and clicks “Pay Now,” they are again directed to a page which will send a one-time passcode (OTP) to the victim’s registered mobile number. The process then authenticates the user for the session.
In a test by security analysts, entering random numbers reloads the page with a message stating the security code has expired. Finally, after the fifth attempt, it reports that it was successful and concludes the phishing chain of events.
| Step | Description | URL |
| 1 | Chatbot Engagement | hxxps://dhiparcel-management[.]support-livechat[.]24mhd[.]com/1_Chi_Chat[.]php |
| 2 | Credential Phishing | hxxps://dhiparcel-management[.]support [1]livechat[.]24mhd[.]com/2_Chi_Contact[.]php |
| 3 | Credit Card Phishing | hxxps://dhiparcel-management[.]support-livechat[.]24mhd[.]com/3_Chi_Pay[.]php |
| 4 | Loading Page | hxxps://dhiparcel-management[.]support-livechat[.]24mhd[.]com/4_Chi_Load[.]php |
| 5 | OTP Page | hxxps://dhiparcel-management[.]support-livechat[.]24mhd[.]com/5_Chi_3D[.]php |
| 6 | Submission Successful Status | https://dhiparcel-management.support-livechat.24mhd.com/6_Chi_Confirm.php |
Using misspelled or similar-but-different URLs like the above, where the “L” in DHL is replaced with “‘i,” is a typical spoofing technique.
How Chatbot Scams Work
Hackers develop malware, ransomware, and other scams for the primary purpose of getting money. Their aim is to achieve this with minimal effort by using automation to carry out their schemes without any human intervention needed. Cast a wider, automated net and let the dollars roll in.
To leverage automation to this end, scammers set up a phishing website with a chatbot system and make them work together.
One tipoff that a chatbot site is fake is that it doesn’t use a SSL. Rather than the expected https://, you’ll see http://.
Another is the URL itself, where scammers attempt to make it look like the original URL by replacing select characters to make it appear the same to the indiscriminate eye.
Knowing what to look for is a big part of avoiding getting caught in the scam.
How to Protect Users from Getting Phished
Most organizations already know that their employees are the weakest link when it comes to cybersecurity. A recent study by Proofpoint revealed that 78% of businesses experienced a ransomware attack that was triggered by a phishing email.
How to prevent employees from getting phished? It’s a challenging problem, but there are a few things in addition to good cyber hygiene that businesses can do.
Utilize a phishing training course or mandatory training that will teach employees to:
- Check the domain names in any email.
- Scrutinize hyperlinks without opening them.
- Look for grammar and spelling errors.
- Review and scrutinize what the email is requesting.
- Avoid reacting to emotional pleas.
- Report phishing emails.
- Never supply personal information (PII) indiscriminately.
- Never provide login credentials if unsure about website validity.
- Participate in phishing tests.
Businesses can implement a system that identifies external origin emails and apply a banner that alerts employees that the email is from an unknown source and carries potential risk. Enabling and requiring multifactor authentication on all login accounts will also decrease risks to the business infrastructure if a phishing scam works.
Beyond training, email protection is an excellent way to protect workers. Emails are vulnerable to harmful programs, ransomware, spyware, viruses, and others. Filtering emails as they arrive is a good way to keep unwanted and dangerous emails out of your workers’ inboxes.



